Zero-day Exploit (Cyber Security Attack)
Last Updated :
06 May, 2023
In this IT era, majority of the cyberspaces are vulnerable to different kinds of attacks.
Zero-day exploit is a type of cyber security attack that occur on the same day the software, hardware or firmware flaw is detected by the manufacturer. As it’s been zero days since the security flaw was last exploit, the attack is termed as zero-day exploit or zero-day attack. This kind of cyber-attacks are considered dangerous because the developer have not had the chance to fix the flaw yet. Zero-day exploit typically targets large organizations, government departments, firmware, hardware devices, IoT, users having access to valuable business data, etc.

Working of Zero-day Exploit:
A software is developed and released without knowing the fact that it has a security vulnerability. An attacker identifies or exploits this vulnerability before the developers identifies or fixes the same. While still the vulnerability is open and unpatched, exploiting the vulnerability, the hacker attacks and compromises the software which can lead to data theft, unauthorized access or crashing of the software itself. After the attacker attacks the target, the public or developer identifies the attack and tries to figure out the patch. The developer identifies the fix and releases the update to safe guard its new user.
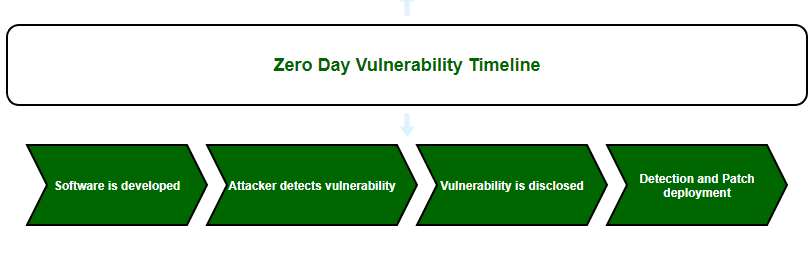
Zero-day Exploit Detection:
Probability of detecting zero day exploit is rare or in other words, the attack leaves no opportunity for detection. But there are a few ways to identify the existing known vulnerabilities.
- Signature Based – In this method, the occurrence pattern of known vulnerability can be detected with the help of pattern matching. Even though this method cannot detect the malware code used for zero-day exploit, it is capable of detecting known attacks like SQL injection that may lead to zero-day vulnerability. While a developer may not be able to detect zero-day attack, the system firewall may be able to detect and protect against few known specific attack types such as XSS , SQL injection, etc.
- Statistical Techniques – By monitoring the normal activity, this technique learns the normal behavior of the network. When the system identifies any deviation from normal profile it will detect a probability of vulnerability.
- Behavior Based – The implementation of behavior based detection typically depends on a ‘honeypot’. A honeypot is a security mechanism that is developed to detect the presence of hackers or hacking attempts.
- Hybrid Techniques – This hybrid technique use the advantage of statistical, behavioral and traditional signature based defense mechanism. They are comparatively more effective as the weaknesses of any single detection technique will not break the security.
Zero-day Exploit Prevention : As zero-day exploits cannot be easily discovered, prevention of the zero-day exploit becomes difficult. There is hardly any ways to protect against zero-day exploit as we don’t have any idea about its occurrence well in advance. We can reduce the level of risk opting any of the following strategies:
Example Cases of Zero-day Exploit :
Zero-day exploit refers to a security vulnerability that is unknown to the software vendor or the public, allowing attackers to exploit it before it can be patched. Here are some examples of zero-day exploits:
Stuxnet: Stuxnet is a well-known example of a zero-day exploit that was discovered in 2010. It was a sophisticated piece of malware that was specifically designed to target industrial control systems, particularly those used in Iranian nuclear facilities. Stuxnet exploited several zero-day vulnerabilities in Windows and Siemens software to gain access to the systems and cause physical damage.
WannaCry: WannaCry is a ransomware attack that was first discovered in 2017. It spread rapidly across the globe, infecting hundreds of thousands of computers in over 150 countries. The attackers exploited a zero-day vulnerability in Microsoft Windows to infect the systems with the ransomware.
Pegasus: Pegasus is a spyware developed by the Israeli company NSO Group. It was used to target the mobile phones of journalists, activists, and government officials in several countries. The attackers used a zero-day vulnerability in Apple’s iOS to install the spyware on the victims’ phones.
Heartbleed: Heartbleed is a vulnerability in the OpenSSL cryptographic software library that was discovered in 2014. It allowed attackers to access sensitive information, including passwords and encryption keys, from servers running the affected software. The vulnerability was present in the software for over two years before it was discovered.
Dirty COW: Dirty COW is a vulnerability in the Linux operating system kernel that was discovered in 2016. It allowed attackers to gain root access to the system by exploiting a race condition in the copy-on-write (COW) mechanism of the kernel. The vulnerability affected millions of systems running the Linux operating system.
Meltdown and Spectre: Meltdown and Spectre are two vulnerabilities in modern computer processors that were discovered in 2018. They allow attackers to access sensitive information, including passwords and encryption keys, from the memory of other running programs. The vulnerabilities affect almost all modern computer processors, including those used in smartphones and cloud servers.
These are just a few examples of the many zero-day exploits that have been discovered in recent years. They highlight the importance of regular software updates and patches to prevent such exploits from being used to compromise systems and steal sensitive information.
Share your thoughts in the comments
Please Login to comment...