IP security (IPSec)
Last Updated :
03 Apr, 2023
Pre-Requisite: Types of Internet Protocol
IP Sec (Internet Protocol Security) is an Internet Engineering Task Force (IETF) standard suite of protocols between two communication points across the IP network that provide data authentication, integrity, and confidentiality. It also defines the encrypted, decrypted, and authenticated packets. The protocols needed for secure key exchange and key management are defined in it.
Uses of IP Security
IPsec can be used to do the following things:
- To encrypt application layer data.
- To provide security for routers sending routing data across the public internet.
- To provide authentication without encryption, like to authenticate that the data originates from a known sender.
- To protect network data by setting up circuits using IPsec tunneling in which all data being sent between the two endpoints is encrypted, as with a Virtual Private Network(VPN) connection.
Components of IP Security
It has the following components:
- Encapsulating Security Payload (ESP)
- Authentication Header (AH)
- Internet Key Exchange (IKE)
1. Encapsulating Security Payload (ESP): It provides data integrity, encryption, authentication, and anti-replay. It also provides authentication for payload.
2. Authentication Header (AH): It also provides data integrity, authentication, and anti-replay and it does not provide encryption. The anti-replay protection protects against the unauthorized transmission of packets. It does not protect data confidentiality.

IP Header
3. Internet Key Exchange (IKE): It is a network security protocol designed to dynamically exchange encryption keys and find a way over Security Association (SA) between 2 devices. The Security Association (SA) establishes shared security attributes between 2 network entities to support secure communication. The Key Management Protocol (ISAKMP) and Internet Security Association provides a framework for authentication and key exchange. ISAKMP tells how the setup of the Security Associations (SAs) and how direct connections between two hosts are using IPsec. Internet Key Exchange (IKE) provides message content protection and also an open frame for implementing standard algorithms such as SHA and MD5. The algorithm’s IP sec users produce a unique identifier for each packet. This identifier then allows a device to determine whether a packet has been correct or not. Packets that are not authorized are discarded and not given to the receiver.
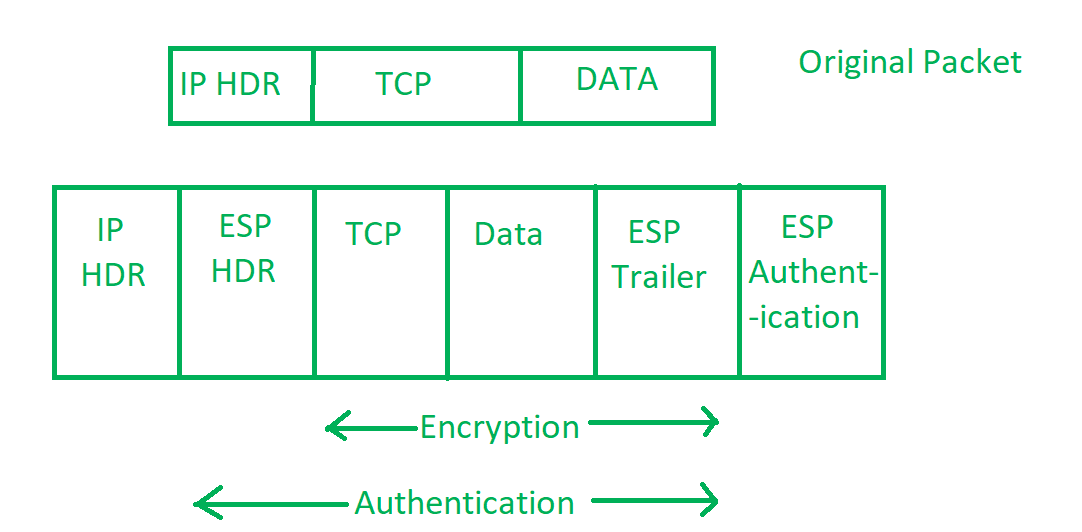
Packets in Internet Protocol
IP Security Architecture
IPSec (IP Security) architecture uses two protocols to secure the traffic or data flow. These protocols are ESP (Encapsulation Security Payload) and AH (Authentication Header). IPSec Architecture includes protocols, algorithms, DOI, and Key Management. All these components are very important in order to provide the three main services:
- Confidentiality
- Authenticity
- Integrity
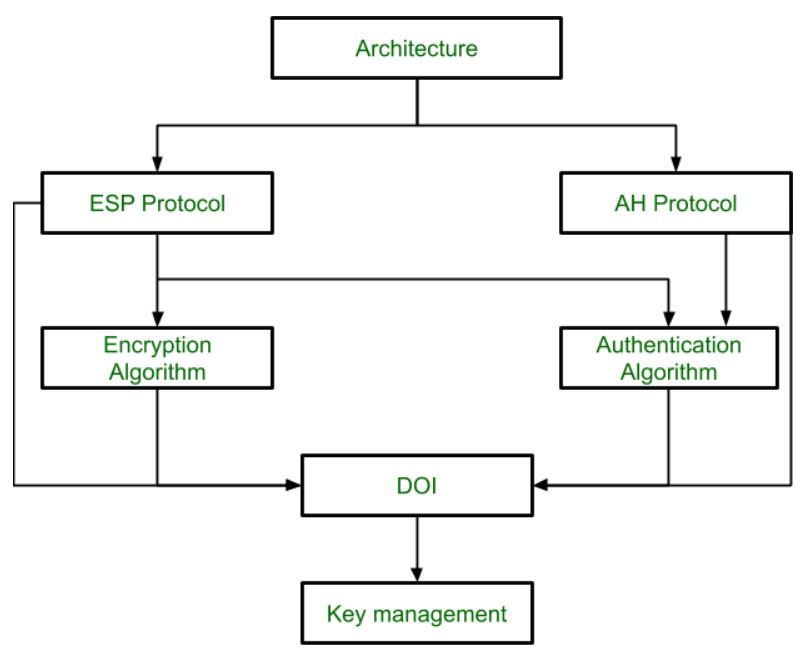
IP Security Architecture
Working on IP Security
- The host checks if the packet should be transmitted using IPsec or not. This packet traffic triggers the security policy for itself. This is done when the system sending the packet applies appropriate encryption. The incoming packets are also checked by the host that they are encrypted properly or not.
- Then IKE Phase 1 starts in which the 2 hosts( using IPsec ) authenticate themselves to each other to start a secure channel. It has 2 modes. The Main mode provides greater security and the Aggressive mode which enables the host to establish an IPsec circuit more quickly.
- The channel created in the last step is then used to securely negotiate the way the IP circuit will encrypt data across the IP circuit.
- Now, the IKE Phase 2 is conducted over the secure channel in which the two hosts negotiate the type of cryptographic algorithms to use on the session and agree on secret keying material to be used with those algorithms.
- Then the data is exchanged across the newly created IPsec encrypted tunnel. These packets are encrypted and decrypted by the hosts using IPsec SAs.
- When the communication between the hosts is completed or the session times out then the IPsec tunnel is terminated by discarding the keys by both hosts.
Features of IPSec
- Authentication: IPSec provides authentication of IP packets using digital signatures or shared secrets. This helps ensure that the packets are not tampered with or forged.
- Confidentiality: IPSec provides confidentiality by encrypting IP packets, preventing eavesdropping on the network traffic.
- Integrity: IPSec provides integrity by ensuring that IP packets have not been modified or corrupted during transmission.
- Key management: IPSec provides key management services, including key exchange and key revocation, to ensure that cryptographic keys are securely managed.
- Tunneling: IPSec supports tunneling, allowing IP packets to be encapsulated within another protocol, such as GRE (Generic Routing Encapsulation) or L2TP (Layer 2 Tunneling Protocol).
- Flexibility: IPSec can be configured to provide security for a wide range of network topologies, including point-to-point, site-to-site, and remote access connections.
- Interoperability: IPSec is an open standard protocol, which means that it is supported by a wide range of vendors and can be used in heterogeneous environments.
Advantages of IPSec
- Strong security: IPSec provides strong cryptographic security services that help protect sensitive data and ensure network privacy and integrity.
- Wide compatibility: IPSec is an open standard protocol that is widely supported by vendors and can be used in heterogeneous environments.
- Flexibility: IPSec can be configured to provide security for a wide range of network topologies, including point-to-point, site-to-site, and remote access connections.
- Scalability: IPSec can be used to secure large-scale networks and can be scaled up or down as needed.
- Improved network performance: IPSec can help improve network performance by reducing network congestion and improving network efficiency.
Disadvantages of IPSec
- Configuration complexity: IPSec can be complex to configure and requires specialized knowledge and skills.
- Compatibility issues: IPSec can have compatibility issues with some network devices and applications, which can lead to interoperability problems.
- Performance impact: IPSec can impact network performance due to the overhead of encryption and decryption of IP packets.
- Key management: IPSec requires effective key management to ensure the security of the cryptographic keys used for encryption and authentication.
- Limited protection: IPSec only provides protection for IP traffic, and other protocols such as ICMP, DNS, and routing protocols may still be vulnerable to attacks.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...