WhoUr Tool for information gathering in Linux
Last Updated :
15 Nov, 2023
WhoUr tool is an automated tool that is used to perform SQLi Vulnerability Scanning and also can perform basic information gathering on the target domain. This tool can get information like DNS Lookup information, IP Reverse Lookup Information, and also can find the Admin Panel Links. The WhoUr tool uses the Google Dork queries to find the URLs on the internet and test them for SQLi flaws. We can provide the custom dork query or directly run the tool, so the tool selects the random query from its database. The WhoUr tool is developed in the Python language and is available on the GitHub platform. As this is available on GitHub it’s free to use and open-source, so anyone can contribute to it.
Features:
- Whois: It provides information about the domain or website, including domain registration details, owner contact information, and registration date.
- DNS Lookup: This feature allows users to perform DNS (Domain Name System) lookups to retrieve information about a domain’s associated IP addresses, MX records, and other DNS-related data.
- IP Reverse Lookup: Users can reverse lookup an IP address to find associated domain names or hostnames.
- Admin Finder: “WhoUr” includes a feature for discovering admin pages or login panels on websites, which can be useful for security testing or reconnaissance.
- Dork Scanner: This feature helps users identify web pages that may be vulnerable to specific search queries (Dorks) and may reveal sensitive information. Users can input their own Dorks or use random ones from a predefined list.
- SQLI Vulnerability Scanner: “WhoUr” is equipped with a SQL injection (SQLI) vulnerability scanner that can identify potential SQL injection vulnerabilities in web applications.
- Custom Dorks: Users have the option to provide their own Dorks, allowing for customized and targeted scanning of websites.
- Save Vulnerable Sites: The tool enables users to save the found vulnerable sites to a text file, which can be helpful for documentation and follow-up actions.
Note: Make Sure You have Python Installed on your System, as this is a python-based tool. Click to check the Installation process: Python Installation Steps on Linux
Installation of WhoUr Tool on Kali Linux OS
Step 1: Use the following command to install the tool in your Kali Linux operating system.
git clone https://github.com/jopcode/whoUR.git

Installation on Kali Linux
Step 2: Now use the following command to move into the directory of the tool. You have to move in the directory in order to run the tool.
cd whoUR
Moving to Directory
Step 3: You are in the directory of the WhoUr. Now you have to install a dependency of the WhoUr using the following command.
sudo pip3 install -r requirements.txt

Installing Dependencies
Step 4: All the dependencies have been installed in your Kali Linux operating system.
python3 whoUR.py
The command python3 whoUR.py implies that you are using the Python 3 interpreter to execute a Python script named “whoUR.py.”
Executing Python Script
Working with WhoUr Tool on Kali Linux OS
Example 1: SQLi Scanner
Select Option 1
Here, “WhoUr” tool has a menu or user interface where you can make selections. Option 1 is for SQLi scanning. When we run the tool, it presents us with a menu, and we have choose this option to start the SQL injection scanning process.
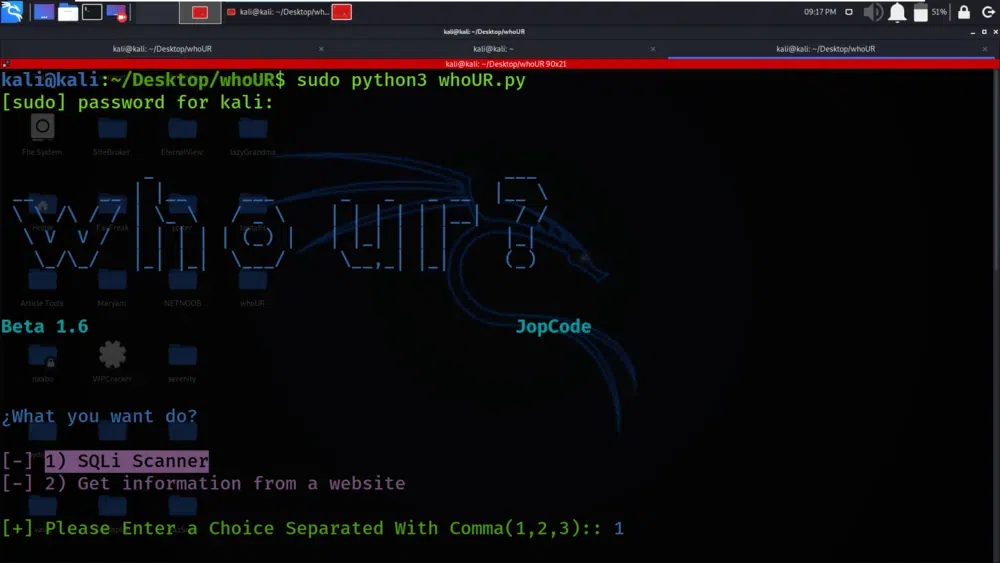
SQli Scanning
The below screenshot shows how the SQL injection scanning process works. It describes that the tool uses a “Google Dork” query. In the context of web security, a “Google Dork” is a specific search query designed to find vulnerable web pages. These queries are often used by security professionals to identify websites that might be susceptible to SQL injection attacks. The tool generates a random Google Dork query to search for potentially vulnerable web pages.

SQL Injection Process
After executing the Google Dork query, the tool scans URLs it finds and checks them for SQL injection vulnerabilities. If any URLs are identified as potentially vulnerable, the tool saves these URLs on the local disk of the computer running the tool. This step is important as it allows you to keep a record of potentially vulnerable sites for further analysis or action.
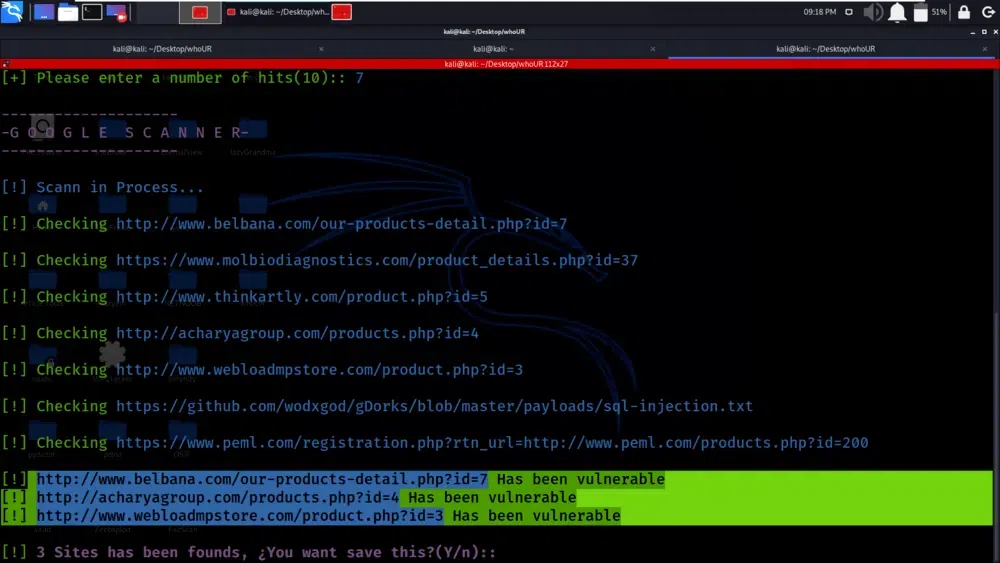
SQL injection vulnerabilities
This statement specifies where the results of the SQL injection scanning process are stored. The identified vulnerable URLs are saved in a file named “sites.txt.” This file is for log or record of the vulnerable sites, making it easy for us to review and take necessary actions based on the results.
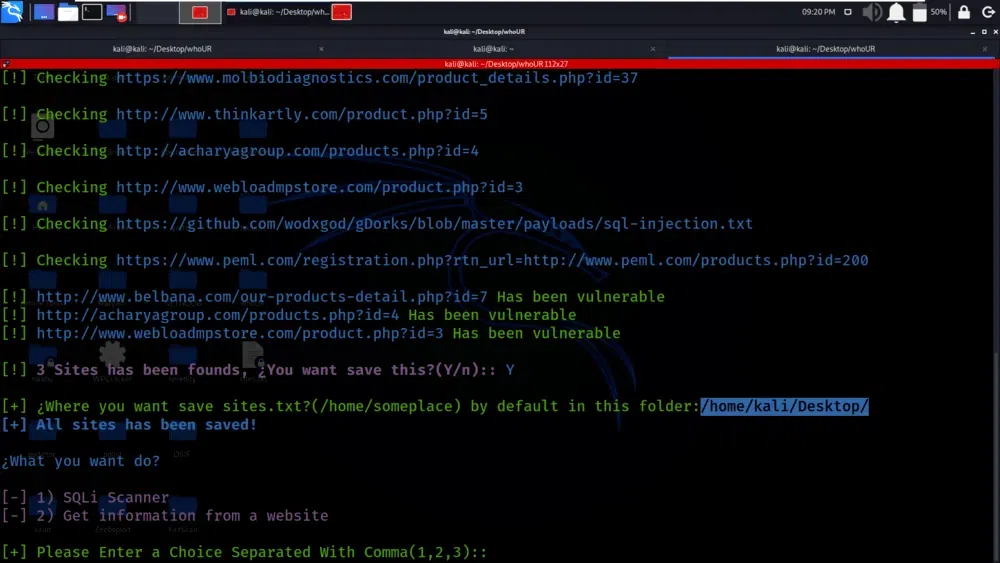
results of the SQL injection scanning process
The “WhoUr” tool has completed its SQL injection (SQLi) scanning process and found some potentially vulnerable URLs, the results are not only saved in a file named sites.txt but are also displayed or shown to the user.

sites.txt
Example 2: Get information from a website
Select Option 2
This step shows that tool has the menu or user interface when running the “WhoUr” tool. In this menu, we need to choose Option 2. This option is for getting information from a specific website or domain.

Option 2
After selecting Option 2, the tool will prompt us to provide a target domain or website that we want to gather information about. In this example, “geeksforgeeks.org” is used as the target domain, but we would replace it with the domain or website we want to test.
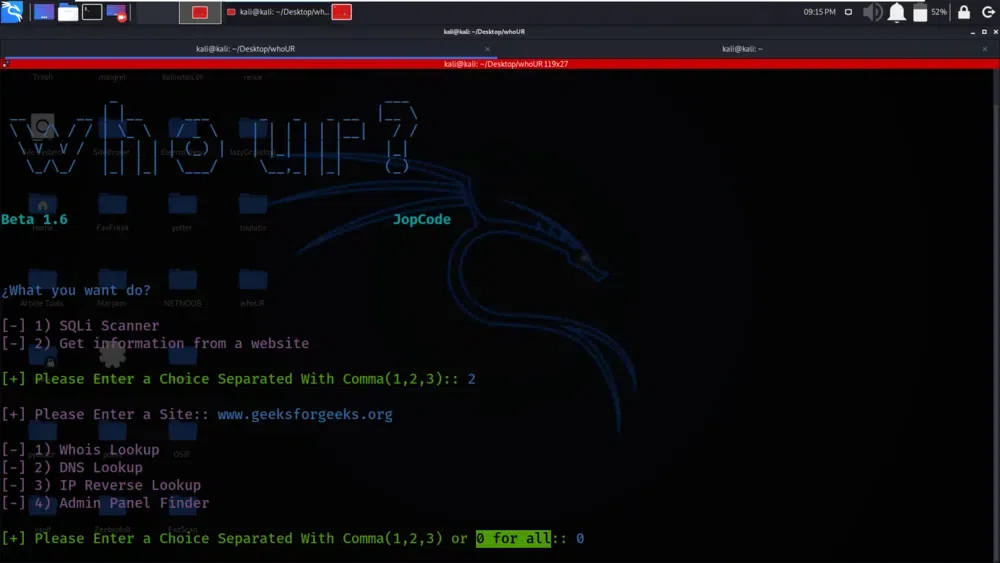
target domain or website
In the below screenshot, we have got information about the domain’s associated Domain Name System (DNS) records. DNS records include details such as the domain’s IP address, MX records (used for email), and other DNS-related data. This information helps you understand the domain’s infrastructure.
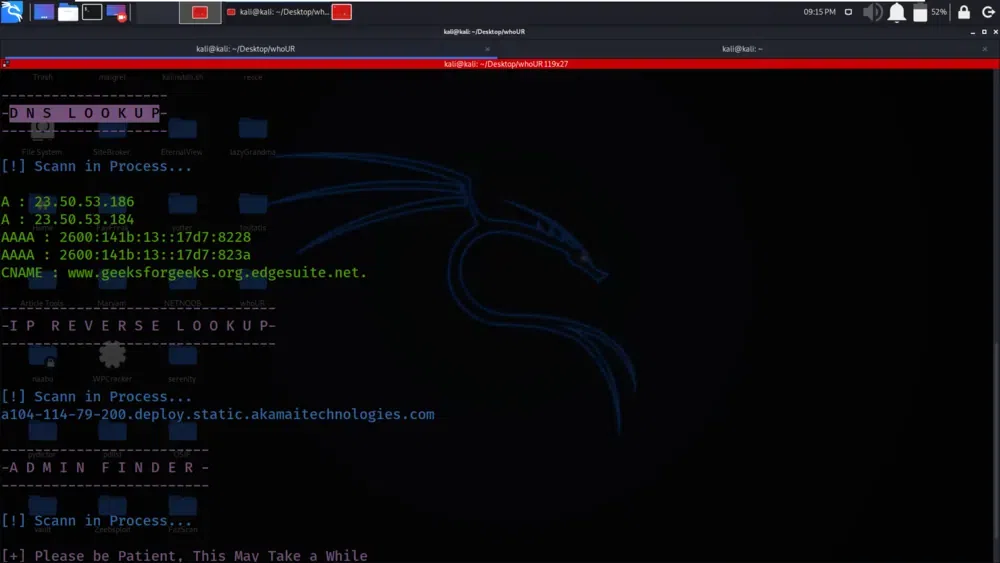
domain’s associated Domain Name System (DNS) records
We have got the IP Reverse Lookup data about geeksforgeeks.org. IP reverse lookup is the process of finding associated domain names or hostnames for a given IP address. The tool will provide data about the domain names or hostnames associated with the IP address of the specified domain geeksforgeeks.org.
IP Reverse Lookup data
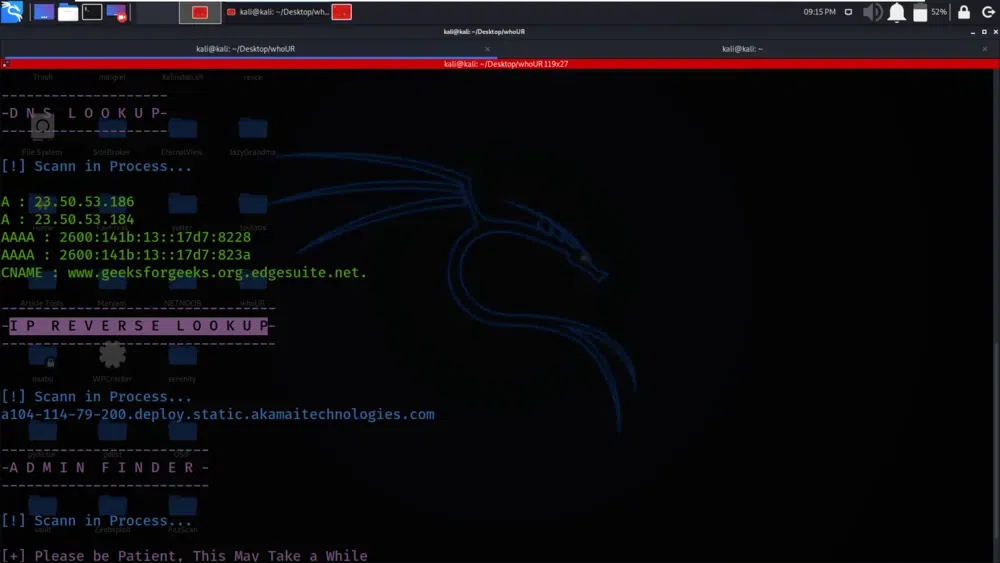
We have got the URL links which contains the admin login strings geeksforgeeks.org. Here the URLs or links associated with admin login pages on the specified domain are retrived. Identifying these links can be useful for security testing or reconnaissance, as it allows you to locate entry points that may require further investigation or analysis.
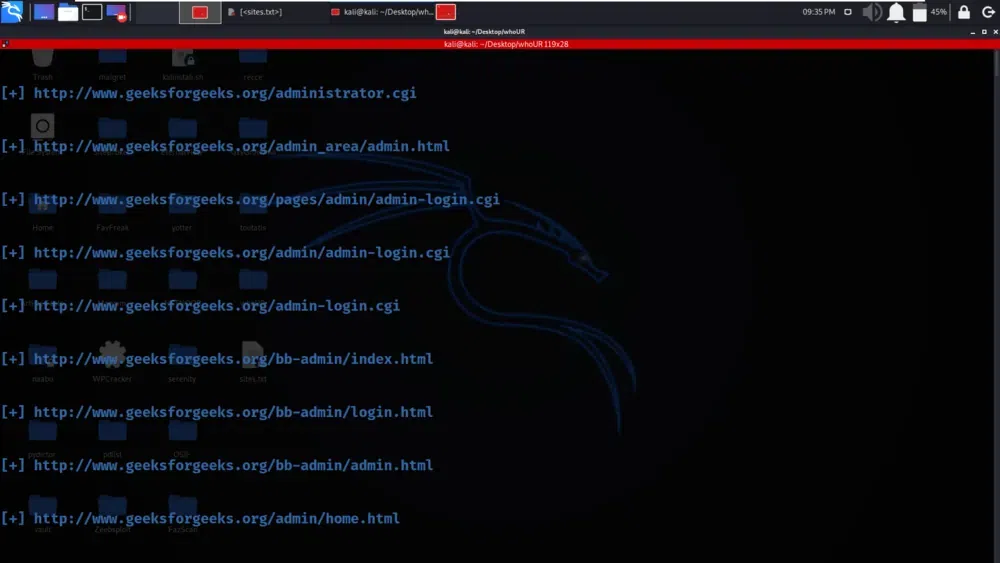
URL links which contains the admin login strings
Conclusion
In conclusion, “WhoUr” is a Python tool designed for website information gathering and vulnerability scanning, particularly focusing on SQL injection vulnerabilities. The tool provides several features, including Whois information retrieval, DNS lookup, IP reverse lookup, admin page finder, Dork scanning, and SQLI vulnerability scanning. Users can input their own Dorks or select random ones from a predefined list. The tool is relatively fast but may not be as powerful as some other established tools in the field. It’s worth noting that “WhoUr” is described as being under construction, which means it may still be in active development to improve its capabilities and features.
Share your thoughts in the comments
Please Login to comment...