Top Tools and Techniques For Banner Grabbing
Last Updated :
17 Oct, 2023
Banner grabbing may be a technique employed by attackers and security researchers to recognize information about a few computing systems on a network and services running on its open ports. In this post, we will be discussing Banner Grabbing, the trending tools, techniques, and prevention methods for Banner Grabbing.

What is Banner Grabbing?
A banner may be a text displayed by a number server containing details like software type and version running during a system or server. Banner grabbing involves getting software banner information, like the name and version of the running server or system. Hackers can perform banner grabbing manually or automatically using an OSINT (Open Source Intelligence Tool). Grabbing a banner is one of the primary phases in both offensive and defensive penetration testing circumstances.
One of the primary points of banner grabbing is that this process is used only by the administrator. There are many protocols that are used for the banner-grabbing process, some of the protocols are stated below:
To read more about it, refer to: What Is Banner Grabbing?
Banner Grabbing Techniques
Let’s explore the various sorts of banner-grabbing techniques.
1. Active banner grabbing
This is the foremost popular sort of banner grabbing, basically sending packets to the remote host and expecting their response to research the knowledge. Active banner-grabbing techniques involve opening a TCP (or similar) connection between an origin host and a faraway host. It is often considered active, as your relationship is visiting and being logged within the remote system. This will be the foremost risky approach to banner grabbing as some IDS often detect it.
2. Passive banner grabbing
On the choice hand, passive banner grabbing enables you to urge a piece of equivalent information while avoiding a high level of exposure from the origin connection. Different intermediate software and platforms are often used as a gateway to prevent a rapid connection and still allow you to urge the knowledge you want. Using 3rd party network tools or services like search engines, Shodan, or sniffing the traffic to capture and analyze packets can assist you in identifying software versions. Passive Banner Grabbing can also record all the data available on the system, and this method is much less risky than the Active Banner Grabbing Technique.
Top 5 Tools to Perform Banner Grabbing
Here, we have discussed the top 5 tools that you can use for Banner Grabbing.
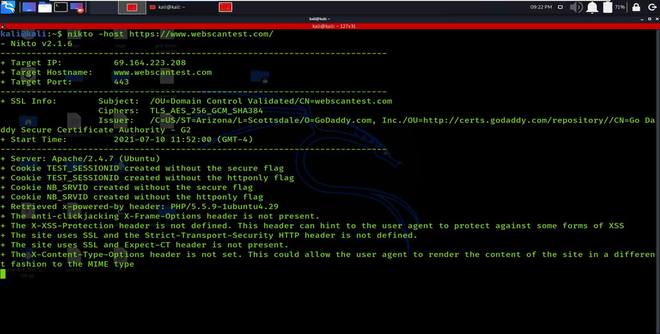
1. Nikto
Nikto is an open-source web application scanner, which we’ll use to grab a banner of a website running on any server. Type the following command to grab the installed web server – its version, the configuration index files, the HTTP server options, and a list of other valuable details. It also can fingerprint the server using favicon.ico files present within the server. Nikto is not designed to be mainly a stealth tool; rather than it is intended to be fast and time-efficient to complete the task in very little time. Due to this, an internet admin can easily recognize that its server is being scanned by looking into the website’s log files. It can also show some items that do not have security problems but are info only, which shows how to make full use of it to secure the webserver more appropriately.
nikto –host https://www.webscantest.com/
2. Nmap (Network Mapper)
Nmap is a network mapper that has risen together with the leading popular, free network discovery tools on the market. Nmap or Network Mapper is the most useful tool that is used by many administrators to monitor the network. Nmap is mostly used for finding the live host and on this host perform the port scanning, Operating System detection etc task. Nmap is simple to use, and most of the tools it provides are familiar to system admins from other programs. The advantage of Nmap is that it brings a good range of those tools into one program instead of forcing you to skip between separate and discrete network monitoring tools. To use Nmap, you would like to be conversant in command-line interfaces. Most advanced users can write scripts to automate everyday tasks, but this is unnecessary for essential network monitoring.
nmap -sC -sV www.webscantest.com

From the above screenshot, you can read the version of the server being detected: “Apache httpd 2.4.7”.
3. Dmitry
Dmitry (Deepmagic operation Tool) can find the maximum number of information possible from a few hosts. Base functionality can collect possible subdomains, email addresses, uptime information, TCP port scan, whois lookups, and much more. Dmitry is a segment of a subset of data gathering tools included in Kali Linux. Dmitry is best for revealing information through search engines about the owner and a web page host. The information which is collected through this tool can be used by malicious persons to do the attack like social engineering. It can also help the attacker seem more likely if they give information about the online page or domain that the owner is using.
dmitry -w www.webscantest.com

4. Netcraft
Netcraft is one of the most operatable information gathering web-interface which helps us check the technologies and the infrastructure of the web applications. Netcraft is an internet monitoring company, their most notable services are monitoring uptimes and providing server operating system detection. Netcraft is often wont to indirectly determine web servers’ information, including the underlying OS, web server version, uptime graphs, etc. So we are using a demo website over Netcraft to grab some service banners and capture all the possible information.
Netcraft Website Link : https://sitereport.netcraft.com/

5. Curl
Curl is a command-line tool to that is used to sending the data to or from a the server, using any pf the supported protocols liek (HTTP, FTP, IMAP, POP3, SCP, SFTP, SMTP, TFTP, TELNET, LDAP, or FILE). Curl is powered by libcurl. This tool is preferred for automation since it’s designed to figure without user interaction. Curl can transfer multiple files directly. cURL offers equivalent features to fetch remote banner information from HTTP servers.
curl -I webscantest.com
The -I parameter will show the header of all the requested pages, and eventually, we grep out the output to fetch the software information.

Prevention From Banner Grabbing
You can follow the following pointers to stop banner grabbing:
- Keep your server and systems up so far to secure your applications against known server exploits.
- Shut down extra or optional services running on network hosts
- You can override your server’s default banner behavior to cover version information. System administrators can customize default banners, configure the network host’s application or OS to disable the flags or remove information from the banners that would give an attacker a leg up.
- Restrict access to services on the network
Conclusion
Banner grabbing is one of the most popular techniques used in the reconnaissance and foot printing process during the initial phases of any penetration testing or actual attack scenario.If you’re new to the penetration testing environment, you’ll find these tools and techniques bring an excellent start to your red team tasks. From a blue team point of view, these are helpful tricks to spot revealed essential data about software running on your server. You’ll be well-equipped to stop cybersecurity incidents within the end.
Share your thoughts in the comments
Please Login to comment...