How to Store and Manage Passwords By Using Azure Key Vault?
Last Updated :
22 Jul, 2023
Azure key vault is one of the Microsoft Azure offered services that enables users to easily store and manage sensitive information like keys, passwords, and certificates in a way that is easily accessible to authorized users and applications (RBAC). Azure key vault can be easily integrated with other Azure services like Azure Virtual Machines, Azure logic apps, Azure Functions, and much more using a secure authentication method. It provides us a centralized way for storing cryptographic keys, secrets, and certificates one of the areas that we use Azure key vault is generally while configuring the database we expose our database sensitive information like username, password, and other data in our code if anyone gets their hands on it they can alter the sensitive information so as to avoid that we will store these things in Azure Key Vault only users with authorization can access it. Another scenario would be Disks attached to the Azure Virtual Machines containing sensible information so that by default these disks are encrypted by Azure. But if we want we can encrypt it and store that cryptographic key in Key Vault only with the help of a cryptographic key we can decrypt that.
Azure Key Vault pricing is based on two factors one being the number of requests made to the service and the second one being the storage used for secrets, keys, and certificates based on the size and quantity being stored. And Azure provides a certain amount of free operations per month so that users can try them before choosing the Azure Key Vault for their purpose.
In this article let’s see how we can use Azure key vault to store and manage the passwords so do follow the steps mentioned below.
Store and Manage Passwords by Using Azure Key Vault
Storing passwords
Step 1: Inside the Azure portal, we would just type in key vaults and select it another way would be on the Azure portal home screen click on all services search for the Azure key vault, and open it.
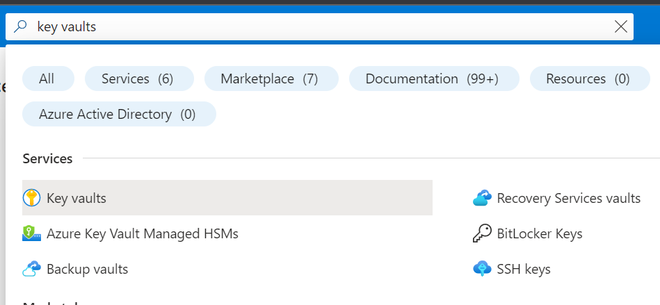
Step 2: Once you open the key vault click on create button to create a key vault and fill in the fields like the resource group to which you want to add your Azure key to. And the region of your choice and the name of your key vault. Then click on “Review + Create” to create a key vault it will take some time to create once it is done you will get a success notification.
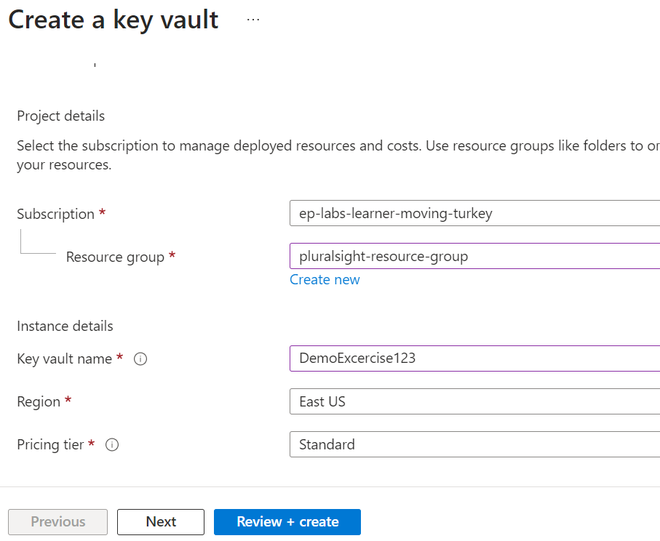
Step 3: Inside the Key vault “DemoExcercise123” click on “secret” and create one then enter the name of the secret and value review the fields and click on create.
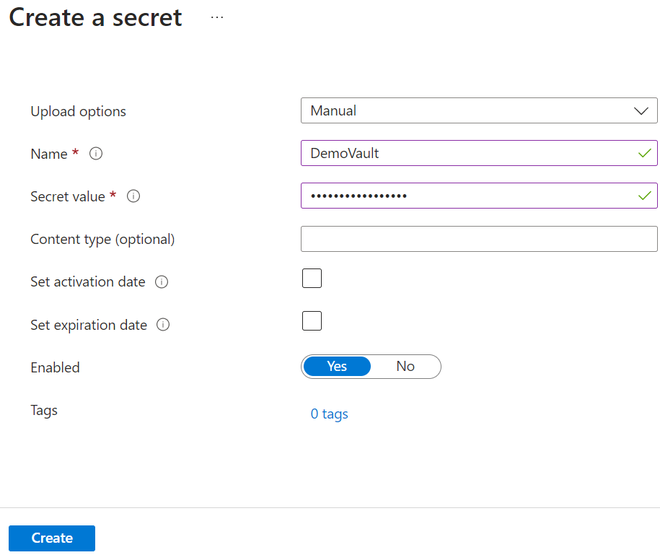
Secret
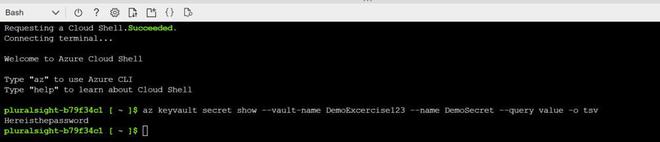
Step 4: Let’s see how we can retrieve the “Secret value” using Azure cloud shell with 2 different approaches. Once you are done with the above steps open your Azure cloud shell select bash and click on create storage then type in the following command and hit enter you will get the following output.
Approach 1
Bash: Az keyvault secret show –vault-name DemoExcercise123 –name DemoSecret –query value -o tsv
If you are using PowerShell then type in the following commands to get the secret value from the key vault. In the below commands if you have different versions of secrets you can mention the secret version also if required but it was optional in this case.
PowerShell: $secretName = DemoSecret
$secret = Get-AzKeyVaultSecret -VaultName DemoExcercise123 -Name $secretName
$secretValue = $secret.SecretValueText
Output:
Approach 2
Now we will see how we can retrieve the “Secret value” using Azure Python SDK the reason we are using Python is that it was already preinstalled and available for us within Azure if you want to use any other SDKs (like Azure Java SDK, Azure C# SDK) either create a service principal for Authentication and Authorization or make use of the Azure CLI. Use the same Azure bash to create a text editor then we will save it with the “.py” extension so as to run our Python script. We can use either the “nano” or “vi” to do that. Before you open the editor install the required Azure libraries(azure-identity and azure-key vault-secrets) to install them type the following commands.
pip install azure-identity azure-keyVault-secrets
Once you are done with the installation type the below command to open the editor here I am saving the file with the name “myscripts”. Make sure that you save the file before closing it to save the file press Ctrl + S to close the editor press Ctrl + X.
nano myscripts.py
Now using the “azure-identity” and “azure-key vault-secrets” we can retrieve the secret value take the key vault name and secret name store it in variables the Default Azure Credential will authenticate as we pass it as a parameter to the Secret Client. The “.get_secret” method will get the value and we were printing it on the console to run the Python script and type the following command.
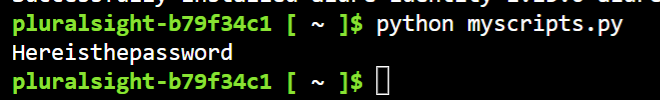
python myscripts.py
Python
from azure.identity import DefaultAzureCredential
from azure.keyvault.secrets import SecretClient
key_vault_name = "DemoExcercise123"
secret_name = "DemoSecret"
credential = DefaultAzureCredential()
secret_client = SecretClient(vault_url=f"https://{key_vault_name}.vault.azure.net/", credential=credential) secret_value = secret_client.get_secret(secret_name).value
print(secret_value)
|
Output:
Managing Passwords
It is important for us to manage our passwords to keep them more secure in order to do that Azure key vault provides us with different options to manage our passwords
- Rotating Passwords: Azure provides us the facility to rotate our passwords regularly by setting up an Azure policy or we can do it manually as well this will keep our passwords more secure. By doing this Azure will automatically create a new version you can view your new password by clicking on the newest version.
- Activity Log: By checking the Activity Log we can see who and when a user accessed the password in our vault we can check the activity log by going to the key vault click on the activity log on the left side of the panel.
- Monitoring and alerts: By setting up monitoring and alerting mechanisms to detect any unusual activities we can do that by using the Azure monitor or Azure security centers to provide us with an alert if any unauthorized access is attempted. Constantly analyze and review the logs to proactively respond to threats.
Share your thoughts in the comments
Please Login to comment...