How To Configure SAML In AWS
Last Updated :
23 Apr, 2024
For enterprises configuring the SAML(Security Assertion Markup Language) is essential for providing an optimized and secured approach to user authentication and authorization. This article guides you in implementing the essential steps within the AWS ecosystem from making an understanding of SAML fundamentals to the AWS IAM console.
What is SAML?
Security Assertion Markup Language (SAML), is the term used by AWS to describe the integration of Single Sign-On (SSO) authentication based on SAML with AWS services. To transfer authentication and authorization information between parties, such as an identity provider (IdP) and a service provider (SP), SAML is an open standard based on XML. Through the use of SAML integration, enterprises may give their users secure access to AWS services without the need for additional AWS-specific credentials. This streamlines user administration centralizes identity management, and enhances security. To know more about AWS IAM.
What Is SSO?
Single Sign-On (SSO) is a simplified Authentication process that allows users in accessing multiple applications with a single set of credentials. It facilitates with single credentials sign in option removing the burden of remembering different usernames and passwords for each system. SSO centralizes the user authentication by provides the usage of secure identity provider, which helps in authenticating the users and issues tokens granting access to linked services. SSO is commonly used in modern IT systems to improve productivity and strengthen general security measures and simplify the user access management.
How Does SAML Authentication Work?
SAML Authentication provides the communication secure, XML based assertions with eash other through the use of SAML authentication. In order to verify the user’s identity and the access to requested resources, the identity provider produces a digitally signed assertion with user data. Now lets discuss on how to configure SAML In AWS.
How To Configure SAML In AWS? A Step-By-Step Guide
There are various steps involved to Configure SAML in AWS as follows :-
Step 1: Create A SAML Identity Provider (IdP) In AWS
.png)
- Access the AWS IAM (Identity and Access Management) service by navigating there.
.png)
- Searching IAM in control plane.

- Click on “Identity Providers” in the left-hand navigation pane, and then click the “Create Provider” button. Give it a name (such as “MyIdP” ) and choose “SAML” as the provider type.
- Upload the metadata document that your SAML identity provider provided in the “Metadata Document” section.
- This page includes details about your IdP, such as signing certificates and SAML endpoints. When finished, select “Next Step“.
Step 2: Create A SAML Role In AWS
- Go to “Roles” in the left-hand navigation plane of the IAM console.
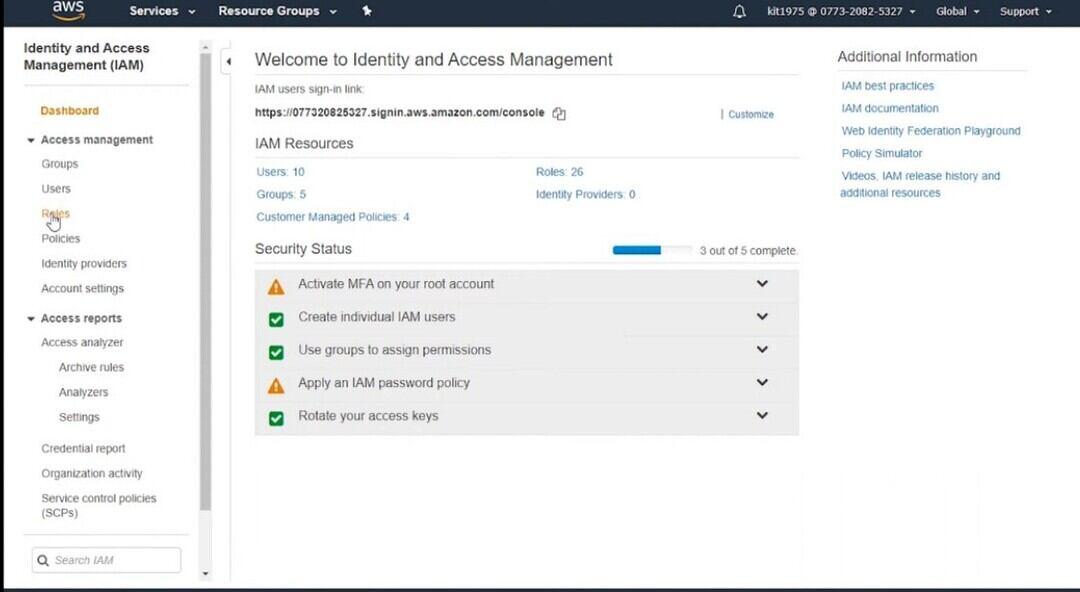
- Then, click on the “Create role” button.
.jpg)
- Select “SAML 2.0 federation” under “Select type of trusted entity.”
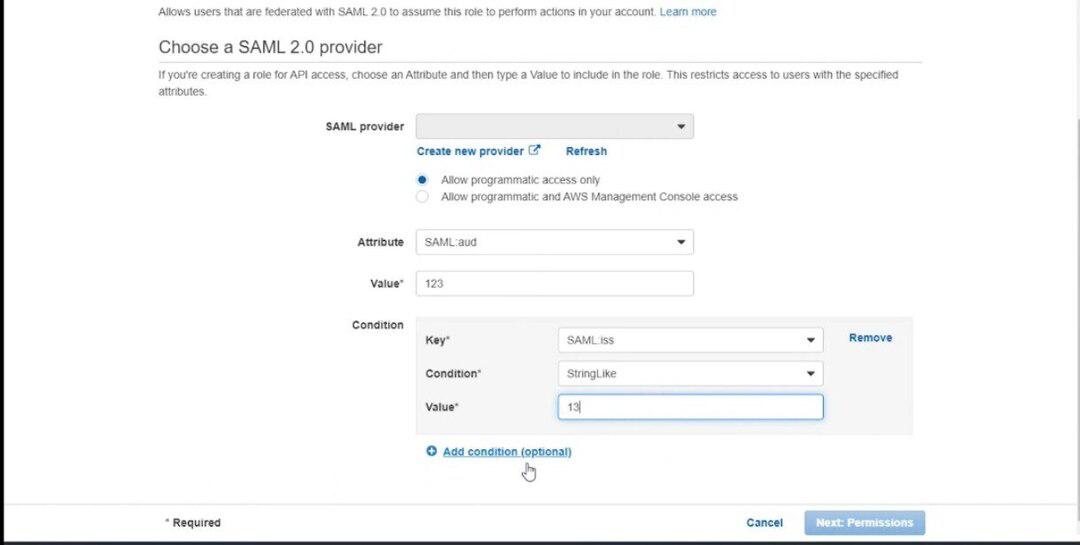
- From the drop-down list, choose the IAM identity provider you created in Step 1.
- Attach policies that outline the role’s access level in the “Permissions” section.
- Use pre-existing AWS policies or develop your own. Click on “Next: Tags” to add any necessary tags, or simply click on “Next: Review” if you don’t need to add tags.
- Provide a name for the role and a description. Review the settings, and then click on “Create role” to create the IAM role.
Step 3: Upload The IdP’s Metadata Document To AWS
- Use the administrator credentials for your AWS account to log in to the AWS Management Console.
- Access the IAM (Identity and Access Management) service by navigating there.
- Go to “Identity Providers” in the left navigation pane.
- To create a fresh Identity Provider (IdP), click the “Create Provider” button.
- Give it a name (such as “MyIdP”) and choose “SAML” as the provider type.
- Give your SAML Identity Provider’s (IdP) metadata document’s URL or XML contents in the “Metadata Document” box.
- When finished, select “Next Step”.
Step 4: Assign the SAML Role to Users
- Search for the SAML role you created in Step 2 in the “Roles” section of the left-hand navigation pane of the IAM console.
- To view the role details, click the role name.
- The “Entity ID” and “Metadata document” that you must give to your SAML identity provider to set up the federation are located under the “Trust relationships” page.
- You must transfer attributes from the SAML assertion provided by the IdP to the IAM role in order to apply the SAML role to users. Both “NameID” for the login and “Role” for the AWS role ARN are frequent attributes.
- Give your IdP administrator these attribute mappings so they may set them up on the IdP side.
Step 5: Test SAML SSO
- Testing the SAML SSO is essential before completing the configuration to make sure it is operating as intended.
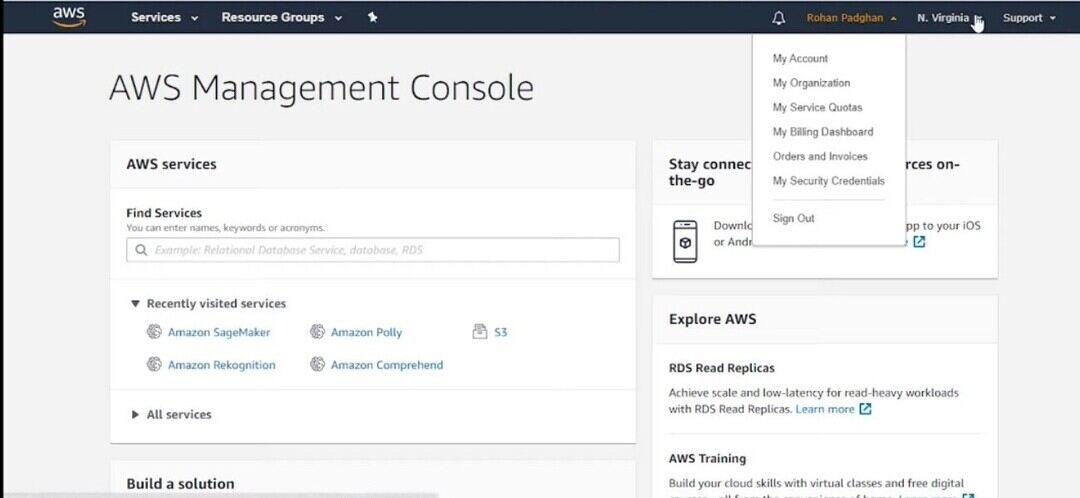
- If you are logged in, sign out of the AWS Management Console.
- access the IdP login page for your company.
- Using your IdP login information, log in.
- You should be directly taken to the AWS Management Console without having to log in again.
Key Features Of SAML
The following are the key features of SAML:
- User Authentication: The AWS service serves as the service provider (SP) and leads users who try to access AWS services to the defined identity provider (IdP) for authentication.
- Identity Provider (IdP) Authentication: A SAML assertion, which is an XML-based security token containing details about the user’s identity and authentication status, is created once the IdP successfully authenticates the user (using techniques such as username/password, multi-factor authentication, etc.).
- SAML Assertion Exchange: The user’s web browser is used by the IdP to communicate the SAML assertion back to the AWS service (SP).
- AWS SAML Validation: AWS verifies the SAML assertion’s signature and determines whether a reputable IdP issued it. It then retrieves the user’s identity and, using the permissions linked to that identity in the AWS Identity and Access Management (IAM) service, allows access to the required AWS services.
Benefits Of AWS SAML Usage
The benefits of using SAML with AWS are as follows:
- Centralized Identity Management: Organizations can use SAML to integrate with their current identity provider (IdP) and centralize identity management. As administrators can manage user authentication and permissions from a single area.
- Single Sign-On (SSO) Experience: Users benefit from a flawless Single Sign-On experience thanks to SAML. Users can access various AWS services and applications after successfully authenticating with the IdP without needing to provide unique credentials for each one.
- Enhanced Security: Organizations can use better authentication techniques, such as multi-factor authentication (MFA), offered by the IdP, by utilizing SAML-based SSO. This improves general security and serves to guard against illegal access.
- Improved User Productivity: The login procedure is made simpler by SSO using SAML, which boosts user productivity and happiness. Without constant login prompts, users can swiftly access AWS resources, which enhances their overall experience.
Alternatives Of SAML
The following are the alternative services for SAML:
- OpenID Connect (OIDC): Like SAML, OIDC enables users to log in only once with the identity provider before being able to access a variety of services without having to enter their credentials again.
- AWS Cognito: Amazon Cognito is a fully managed service that provides user authentication and access control for web and mobile applications. It supports a variety of identity sources, such as OIDC providers, SAML-based IdPs, and social identity providers (such as Google and Facebook).
- Shibboleth: It is an open-source federated identity solution facilitates in securing single sign-on (SSO) across organizations. It fcous on attribute-based access control improving user’s administration permissions at high level. Through the support of shibboleth it makes possible for users without repeated authentication.
- Kerberos: The network authentication protocol is well know for providing strong security to the client-server applications. Kerberos facilitates with safe communication between many realms or domains by supporting cross-realm authentication. Kerberos facilitate strong authentication making reliable base for network environment security.
Best Practice Of Configuring AWS SAML
The following are the best practices for configuring AWS SAML:
- Security: When creating, deploying, and maintaining your AWS resources, security should always come first. Enable Multi-Factor Authentication (MFA), specify fine-grained access controls, encrypt data in transit and at rest, and periodically evaluate security settings with AWS Identity and Access Management (IAM).
- Least Privilege: Use the least privilege principle by only giving users and programs the rights necessary to complete their responsibilities. IAM policies shouldn’t be extremely lenient.
- Regular Backups: Implement regular backups for critical data and configurations. Use services like Amazon S3 for data backups and AWS Config for managing configurations.
- Integration With Identtiy Providers (IdPs): It simplifies the user identification and authorization procedures by integrating AWS SAML with reputable identity providers (IdPs).
- AuditSAML Assertions And Logs: It regularly check the security of SAML assertions and logs to monitor the user activities, Identifying potential security issues and maintaining the compliance.
Conclusion
The procedure of setting up SAML on AWS using the AWS Management Console has been described in detail in this article. Businesses may improve security, streamline user management, and make the AWS environment login process simpler by implementing SAML-based authentication. Adopting SAML and other authentication techniques makes the AWS environment more secure, scalable, and user-friendly, which supports a successful and effective cloud strategy.
Configure AWS SAML – FAQ’s
Does AWS Use SAML For SSO?
Yes, AWS supportss SAML(Security Assertion MarkUp Language) for Single Sign-On (SSO) facilitating users in accessing AWS resources using their existing credentials.
What Is SAML2.0?
SAML2.0 is the modern version of SAML. It is a often used XML based protocol for secured authentication and authorization in SSO systems.
Is SAML And SSO The Same?
No, SSO is a more general concept whereas SAML is a protocol. SSO refers to the user’s ability for accessing multiple systems or applications with a single set of credentials.
What Is SAML And Why It Is Used?
SAML is an XML-based standard used to exchange authorization and authentication information between parties. It is commonly utilized in web services and applications that support secure Single Sign-On (SSO).
What Is The Difference Between SAML And Oauth2?
Eventhough both are used for same permission and authentication, SAML and OAuth2 have different functionalities. OAuth2 is focused on authorization supporting third-party apps to access a user’s resources on a service whereas SAML is used for Single Sign-On (SSO) between multiple systems Eg: social network login.
Is SAML A Form Of SSO?
Yes, SAML is mostly used for the implementation of SSO solutions. It facilitates with the exchange of authentication and authorization of data between Identity and service providers. It allows users to access multiple applications with single set of credentials.
Share your thoughts in the comments
Please Login to comment...