How to Add GitHub Actions Secrets ?
Last Updated :
16 Apr, 2024
When it comes to safely managing sensitive data in your workflows—like access tokens, API keys, and other credentials—GitHub Actions secrets are essential. By using these tricks, you can securely access and save private information without exposing it to the source code of your repository. You may improve the security of your CI/CD pipelines and guarantee that confidential or sensitive data is kept safe during the development and deployment phases by making use of the secrets. We will go over how to add, manage, and use GitHub Actions secrets in this article to protect your projects and automate tasks to make your workflow more efficient. We can call and store the secrets in the pipeline by using the secrets. We can configure the secrets on GitHub by following the procedures listed below.
Steps To Configure Secrets in GitHub Actions
Step 1: Log in to the GitHub repository, click on the repository, and click on settings.
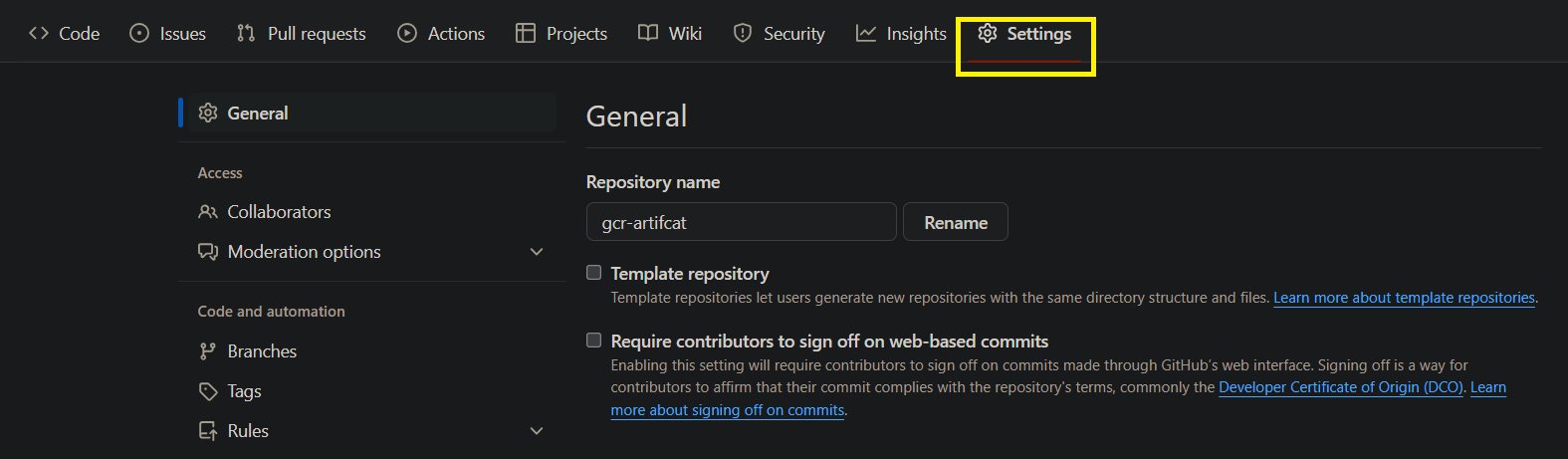
Step 2: Scrole down left side and click on secrets and variables and click on actions.
Step 3: Secret tokens and GitHub Actions
- In the left sidebar, select “Secrets.”
- Click on the “New repository secret” button.
- Provide a name for your secret, such as “SERVICE_ACCOUNT_KEY.”
- Paste the value of your secret into the “Value” field.
- Click on the “Add secret” button to save your new repository secret.

Step 4: GitHub Actions secret example
In this workflow, we are calling the secret SERVICE_ACCOUNT_KEY from the GitHub repository secrets. This key is crucial for authenticating with Google Cloud Platform (GCP) services during the CI/CD process. By referencing the secret directly within the workflow file, we ensure that sensitive credentials remain secure and inaccessible to unauthorized users. This practice adheres to best security practices and safeguards against potential security vulnerabilities.
name: <Respective name of cicd>
on:
push:
branches: [ <Branch Name> ]
jobs:
build-push-gcr:
name: Build and Push to GCP
runs-on: ubuntu-latest #Runner
env:
IMAGE_NAME: <Image-name>
PROJECT_ID: <Project-id>
steps:
#Checkout stage
- name: Checkout
uses: actions/checkout@v2
#Call the secert into action file
- uses: google-github-actions/setup-gcloud@v2
with:
service_account_key: ${{ secrets.SERVICE_ACCOUNT_KEY }}
project_id: ${{ env.PROJECT_ID }}
export_default_credentials: true
- Secrets Setup: The
google-github-actions/setup-gcloud action is used to set up Google Cloud SDK. It requires access to the SERVICE_ACCOUNT_KEY secret, which contains the service account key JSON file necessary for authentication.
- Accessing Secrets: The
service_account_key parameter of the setup-gcloud action fetches the secret value stored in the GitHub repository secrets.
- Secret Management: Secrets like
SERVICE_ACCOUNT_KEY are stored securely in GitHub repository settings, ensuring that sensitive information is not exposed in the workflow file.
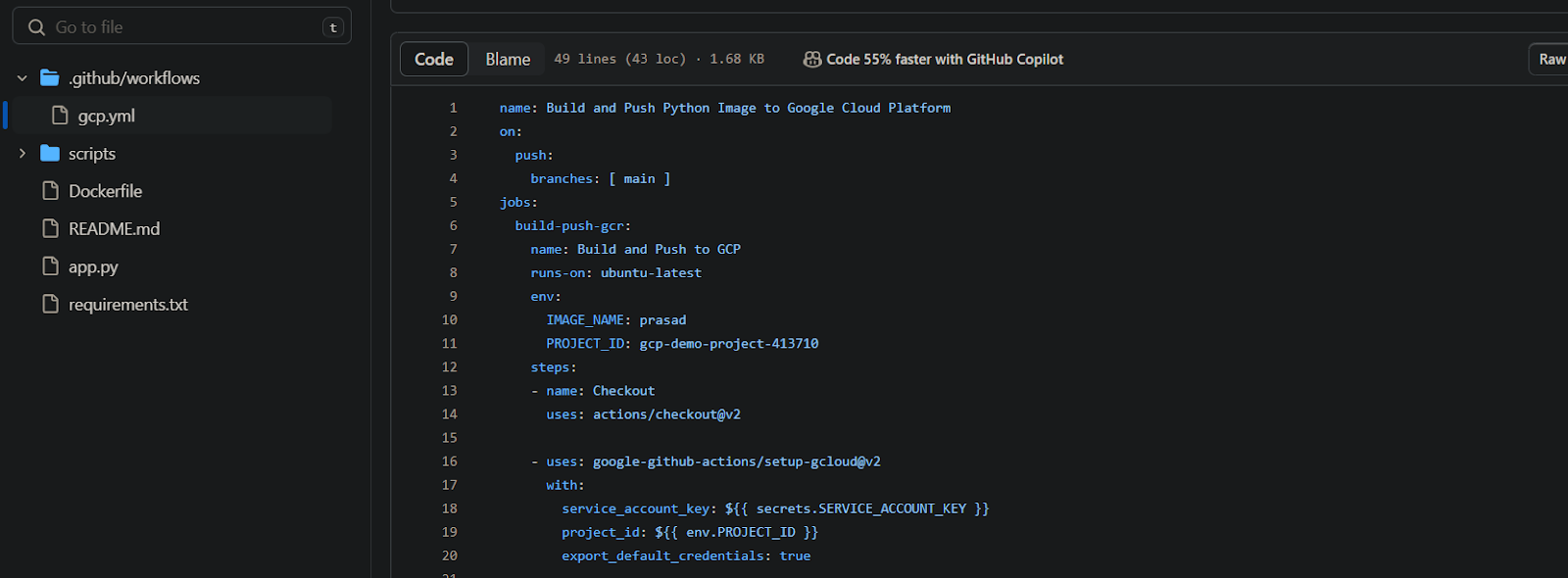
Step 5: Verify the console output of the github actions here the actions file calling the secrets from the secrets.

How To Log GitHub Actions Secret
We can utilize the env context to retrieve and publish the secret values in your workflow logs in order to log Git-Hub Actions secrets.
name: <Respective name of cicd>
on:
push:
branches: [main]
jobs:
log-secrets:
runs-on: ubuntu-latest
steps:
- name: Log GitHub Actions Secrets
env:
SECRET_USER: ${{ secrets.USER }}
SECRET_PASSW: ${{ secrets.PASSW }}
run: |
echo "Username: $SECRET_USER"
echo "Password: $SECRET_PASSW"
The echo command is being used to retrieve two secrets (USERNAME and PASSWORD) and print their respective values like here secrets and passwords.
GitHub Actions Secret Review
Enter into the your repositories on GitHub and select the “Settings” page in order to examine GitHub Actions secrets. Next, choose “Secrets” from the sidebar on the left. A list of all the secrets kept for your repository may be found here. Reviewing their names allows you to change or remove them as necessary. By following this step we can review the secret on github.
Conclusion
GitHub Actions secrets provide a strong way to handle private data safely in your processes. You may add, manage, and use secrets to protect your projects and expedite your automated processes with ease by following the instructions in this article. Do not forget to periodically evaluate your secrets to make sure that only individuals with permission can access private information. You can keep the integrity of your development and deployment workflows and improve the security of your CI/CD pipelines with Git-Hub Actions secrets. Uisng the above steps to configure the screts on github.
Add Github Actions Secrets – FAQ’s
How do I add a secret to a git repository?
To set secrets in GitHub Actions, navigate to your repository settings, select “Secrets” from the sidebar, and click “New repository secret” to enter a new secret key-value pair. Next, to refer to the secret in your workflow file, use ${{ secrets.YOUR_SECRET_NAME }}.
What is GitHub action secrets?
Access tokens and API keys, among other confidential data, can be securely stored and retrieved in your GitHub workflows with the help of GitHub Actions secrets, which are encrypted environment variables. They provide a secure way to manage confidential data without exposing it in your repository’s source code.
What is repository secrets?
Repository secrets are encrypted variables that let you safely handle and store private data in your GitHub repository, including passwords, access tokens, and API keys. Without disclosing private information within your codebase, these secrets can be utilized in GitHub Actions workflows to authenticate with third-party systems or access external services.
How do I read secrets in GitHub Actions?
You can use the ${{ secrets.SECRET_NAME }} syntax in your workflow YAML files or shell scripts to access and read secrets in GitHub Actions. To ensure secrecy, these secrets are automatically hidden in logs.
Share your thoughts in the comments
Please Login to comment...