Cloud Native Applications are a new way of building software that takes advantage of the cloud and uses smaller, more focused pieces called microservices. Design patterns are important for building these applications because they provide guidelines and examples on how to solve common problems. In this article, we will focus on Event-Driven Architecture Patterns, which are patterns that help us build applications that can handle events in real time.
Important Topics for Event-Driven Architecture Patterns
Event-Driven Architecture Patterns
Event-driven architecture (EDA) is a way of building applications where events are used to trigger actions. Events can come from different sources and applications react to them. EDA is well-suited for Cloud Native Applications because it allows us to build applications that can scale and respond quickly.
In “request/response” architecture, in which services had to wait for a response before moving on to the next task, is replaced with this pattern. Events control the flow of event-driven architecture, which is built to react to them or take action in response to an event.
Event-Delivery Patterns
1. Publish-Subscribe (Pub-Sub):
In this pattern, events are sent by publishers to many subscribers. This allows components to communicate without having to know about each other.
.jpg)
The diagram illustrates the Pub-Sub pattern, where events are published by publishers and received by multiple subscribers. This decoupled communication pattern enhances flexibility in application architecture.
2. Message Queue:
Messages are stored in a queue and then delivered to the intended recipients. This pattern ensures that messages are reliably delivered and can handle large amounts of traffic.
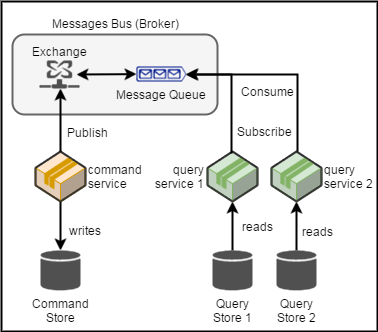
The diagram depicts a Message Queue pattern where messages are queued and delivered to consumers. This asynchronous approach ensures scalability and reliability in event processing.
State Management Patterns
1. Event Sourcing:
Events are the main source of information in this pattern. The application’s state is built by replaying these events. This allows us to have a complete record of all the actions that happened in the system.

The diagram showcases Event Sourcing, where events are stored and used to reconstruct the application’s state. It provides a historical view of all actions, facilitating data consistency.
2. CQRS (Command Query Responsibility Segregation):
CQRS separates the operations that change the state of the application from the ones that retrieve information. This allows us to optimize for performance and scale the different parts of our application independently.
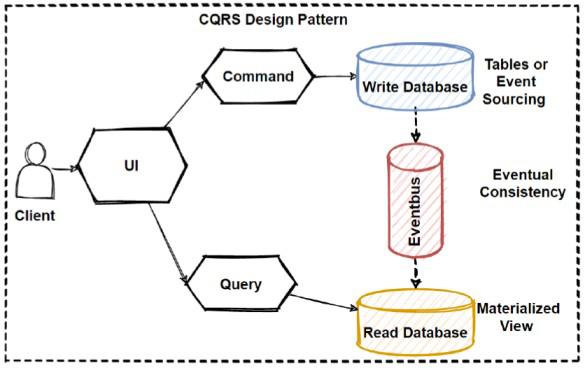
The diagram illustrates CQRS, which divides command and query responsibilities. This separation optimizes performance and scalability by enabling independent scaling of components.
Orchestration Patterns
1. Saga:
Sagas help us manage distributed transactions across multiple microservices. They consist of a series of events and actions that need to be performed in order to keep the data consistent.
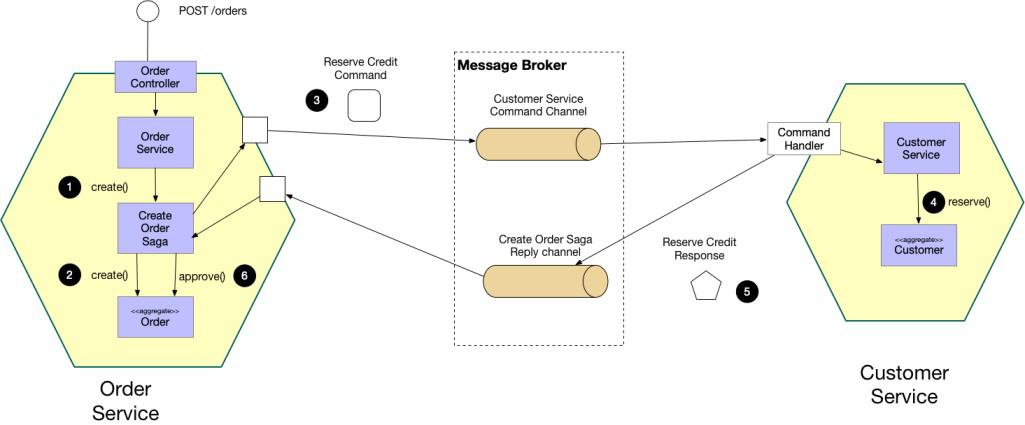
The diagram presents a Saga pattern, showcasing a sequence of events and actions across microservices. Sagas enable distributed transaction management for data consistency.
2. Choreography:
In choreography, microservices listen to events and react to them independently. This allows for more flexibility and allows services to evolve independently.
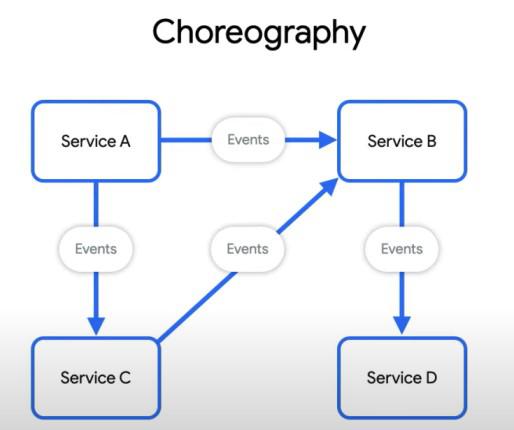
The diagram demonstrates Choreography, where microservices communicate through events without central coordination. This approach offers flexibility and autonomous service evolution.
Technologies for Event-Driven Architecture
There are several technologies that support Event-Driven Architecture in Cloud Native Applications:
- Apache Kafka: A platform that helps us handle event streams efficiently.
- RabbitMQ: A message broker that ensures reliable event delivery.
- AWS Lambda: A serverless service that can be triggered by events.
- Kubernetes: It is a platform that helps manage and organize containers that run applications in a cloud environment.
Testing
When testing cloud-native applications that rely on events, there are specific approaches you can take:
Integration Testing:
Integration testing is a critical step in ensuring the reliability of cloud-native applications that rely on events. It focuses on verifying that events are correctly published, delivered, and received within the application ecosystem. Integration tests validate the interactions between various components, including event publishers, message queues, event processors, and subscribers.
End-to-End Testing:
- End-to-end testing takes a broader perspective, confirming that the entire event-driven process functions seamlessly from start to finish. It simulates real-world scenarios and user interactions to validate that events are not only technically sound but also fulfill the intended business processes.
- End-to-end tests encompass the entire event flow, from event creation and propagation to final actions taken by microservices. This type of testing helps identify potential bottlenecks, data inconsistencies, or issues related to event handling.
Security
Security is crucial in event-driven architectures:
Authentication and Authorization:
- Authentication ensures that entities interacting with the event system are who they claim to be, preventing unauthorized access.
- Authorization defines access control policies, ensuring that only authorized users or services can publish or consume specific events.
Note: Effective authentication and authorization mechanisms are essential for safeguarding sensitive data and maintaining data integrity within the event-driven ecosystem.
Encryption:
Encryption plays a pivotal role in securing event-driven communication. It involves encoding data in such a way that it becomes unreadable to unauthorized parties during transmission. By encrypting event data, you ensure that even if intercepted, it remains confidential and protected. Encryption safeguards against data breaches and eavesdropping attacks, adding an extra layer of security to event-driven architectures.
Observability and Monitoring
Observability and Monitoring are important for maintaining and troubleshooting event-driven applications:
Logging:
Logging is the practice of recording detailed event information, including timestamps, event sources, and relevant metadata. In an event-driven system, logging helps to track the flow of events, providing insights into event processing and system behavior. It aids in troubleshooting issues, diagnosing errors, and auditing events for compliance purposes. Comprehensive logging enhances visibility and allows for historical event analysis.
Metrics:
Metrics involve collecting and analyzing quantitative data related to event-driven system performance. Key metrics may include event throughput (the rate at which events are processed), event latency (the time it takes for events to traverse the system), and error rates (the frequency of event processing failures). Monitoring these metrics provides real-time insights into the health and efficiency of event-driven processes, enabling proactive issue resolution and performance optimization.
Distributed Tracing:
Distributed tracing allows for the tracing of events across different microservices and components within an event-driven architecture. It creates a visual representation of the path events take as they traverse the system. This capability is particularly valuable for debugging complex scenarios, identifying bottlenecks, and understanding the sequence of events during distributed transactions. Distributed tracing enhances observability by providing a holistic view of event flows.
DevOps
DevOps practices are vital:
Continuous Integration/Continuous Deployment (CI/CD):
CI/CD practices are integral to managing event-driven applications efficiently.
- Continuous Integration: It involves automating the integration of code changes into a shared repository, where automated tests are executed to catch integration issues early.
- Continuous Deployment: Extends this process by automatically deploying code changes to production or staging environments after successful testing.
In the context of event-driven applications, CI/CD ensures that event-driven code changes are tested, integrated, and deployed seamlessly, facilitating rapid development cycles and reducing the risk of errors.
Infrastructure as Code (IaC):
IaC is a practice that involves defining and managing infrastructure configurations through code, rather than manually configuring servers and resources. In event-driven architectures, IaC allows for consistent and repeatable provisioning of infrastructure components, such as message queues, event processors, and microservices. By defining infrastructure as code, changes can be version-controlled, automated, and tracked, ensuring that the event-driven ecosystem remains consistent and resilient across different environments.
Conclusion
In the realm of cloud-native applications, event-driven architecture patterns are essential. They provide the necessary flexibility, scalability, and responsiveness for modern software systems. By understanding and applying these patterns, along with the right technologies, testing strategies, security measures, and DevOps practices, developers and architects can build resilient, high-performance, and cloud-native applications that meet the demands of today’s dynamic digital landscape.
Share your thoughts in the comments
Please Login to comment...