End to End Encryption (E2EE) in Computer Networks
Last Updated :
15 Oct, 2018
What is Encryption?
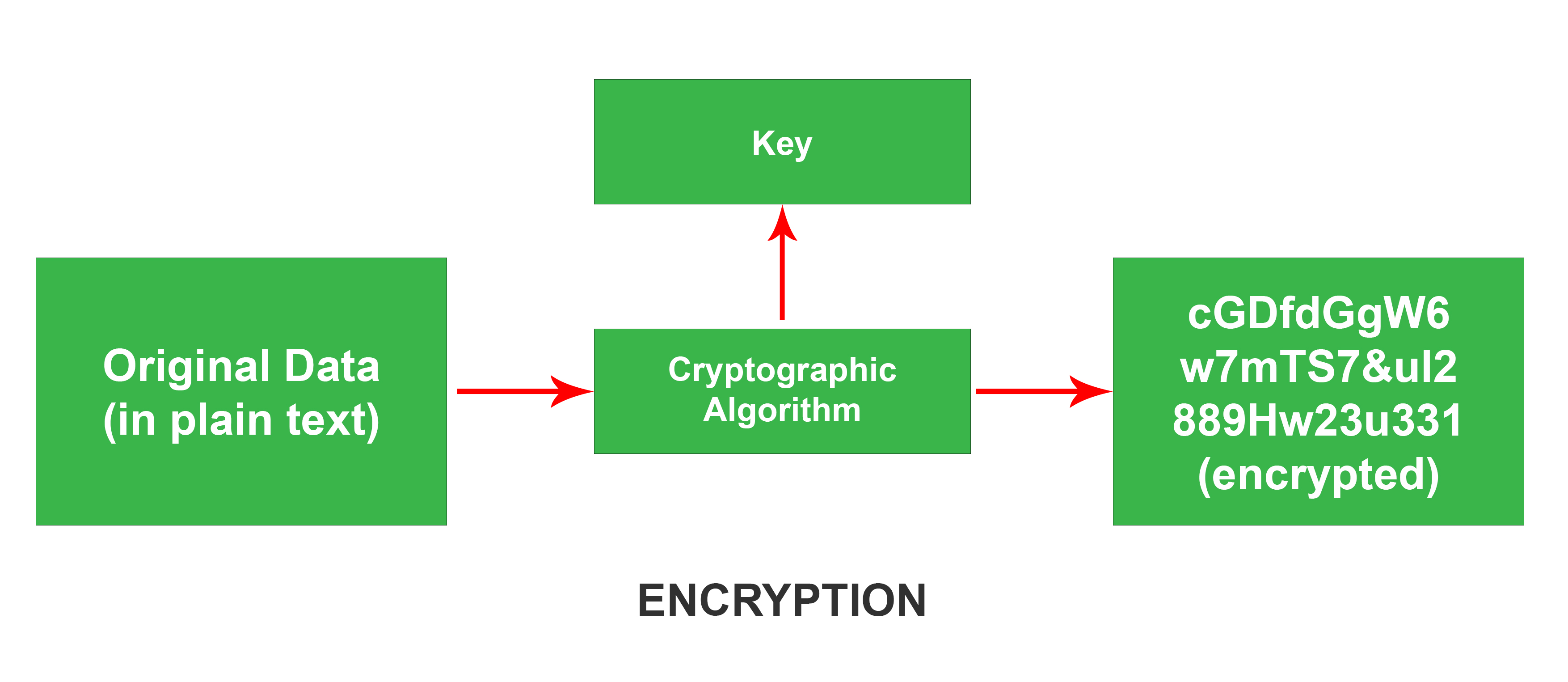
Have you ever wondered how our emails, texts, photos, videos are sent over the Internet? Whenever you send anything over the Internet, it passes through a lot of servers, routers, and other devices where anyone can intercept it and get access to your private information. Thus, to tackle such mishap, encryption was introduced. In encryption, the sent data is modified into such a form that it is impossible to read in between the users. Encryption is basically the modification of data into some unreadable form. When the data reaches the receiver, the data is again modified to its original form. This process called Decryption. A key is required to decrypt the encrypted data called the encryption key. Only the parties that have this key are able to get access to the data.
What is E2EE?
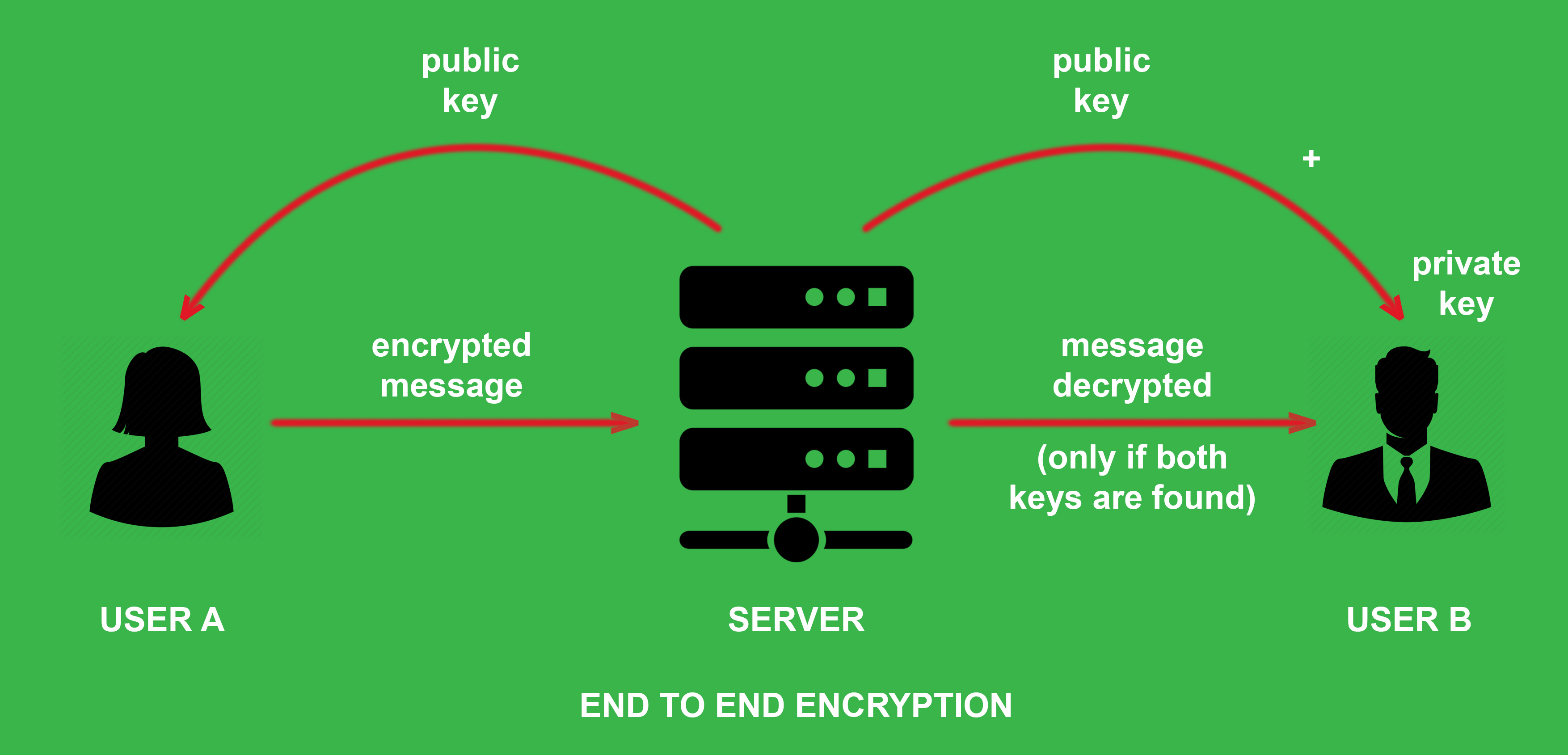
It is a type of asymmetric encryption. In this type of encryption, both the parties have two keys, public and private. The public key is available to each party and to anyone sitting on the server. The private key is known only to the owner and no one else, not even to the party on the opposite end. Both public and private keys are required to decrypt the scrambled data. Suppose Ronaldo is sending a text to Messi. The public key is known to both and to the server also. But both of them has a private key, which no one has any idea about. Thus the text sent by Ronaldo can’t be read by the server (as it doesn’t have the private key). The private key of Messi with the public key is required to decrypt the original text by Ronaldo (I hope it says, ” We both are legends!!! “). In this encryption, the middle party in no way can get access to the data.
All this encryption, decryption, generating keys, etc are handled by web mechanisms, the software, and algorithms. We need not worry about the enabling of the end to end encryption. Just sit back and relax because it is the most secure way of sending information till now. Although there is not a hundred percent surety about its vulnerability. Maybe in near future, there will be some better encryption method than this. But E2EE is the most efficient encryption at present.
Share your thoughts in the comments
Please Login to comment...