What is E2EE(End to End Encryption)?
Last Updated :
10 May, 2020
E2EE or End to End Encryption refers to the process in which encryption of data are being done at the end host. It is an implementation of Asymmetric encryption and hence ensures a secure way of data communication. It is the most secure way to communicate privately and securely as data can be read-only by the sender and the receiver. No one else can encrypt the data including government or even by the server through which data is passing.

Types of Encryption
Based on the type of keys being used, encryption is of two types:
- Symmetric Encryption:
In Symmetric Encryption the same key is used both at the sender and receiver side to encrypt and decrypt the messages. So it may require sending the key from one side to another, thereby exposing it to be compromised. It is therefore less effective as compared to asymmetric encryption.
- Asymmetric Encryption
In Asymmetric encryption two types of keys are used, one public key and one private key. The sender and the receiver both have public key and private key. The Public Keys are available to both end and both sender and receiver can share public keys before communication to start. Sender uses the receiver’s public key to encrypt the messages to be sent and the receiver uses both its public and private keys to decrypt the messages. The private key to the receiver is available only with the receiver and no one else.
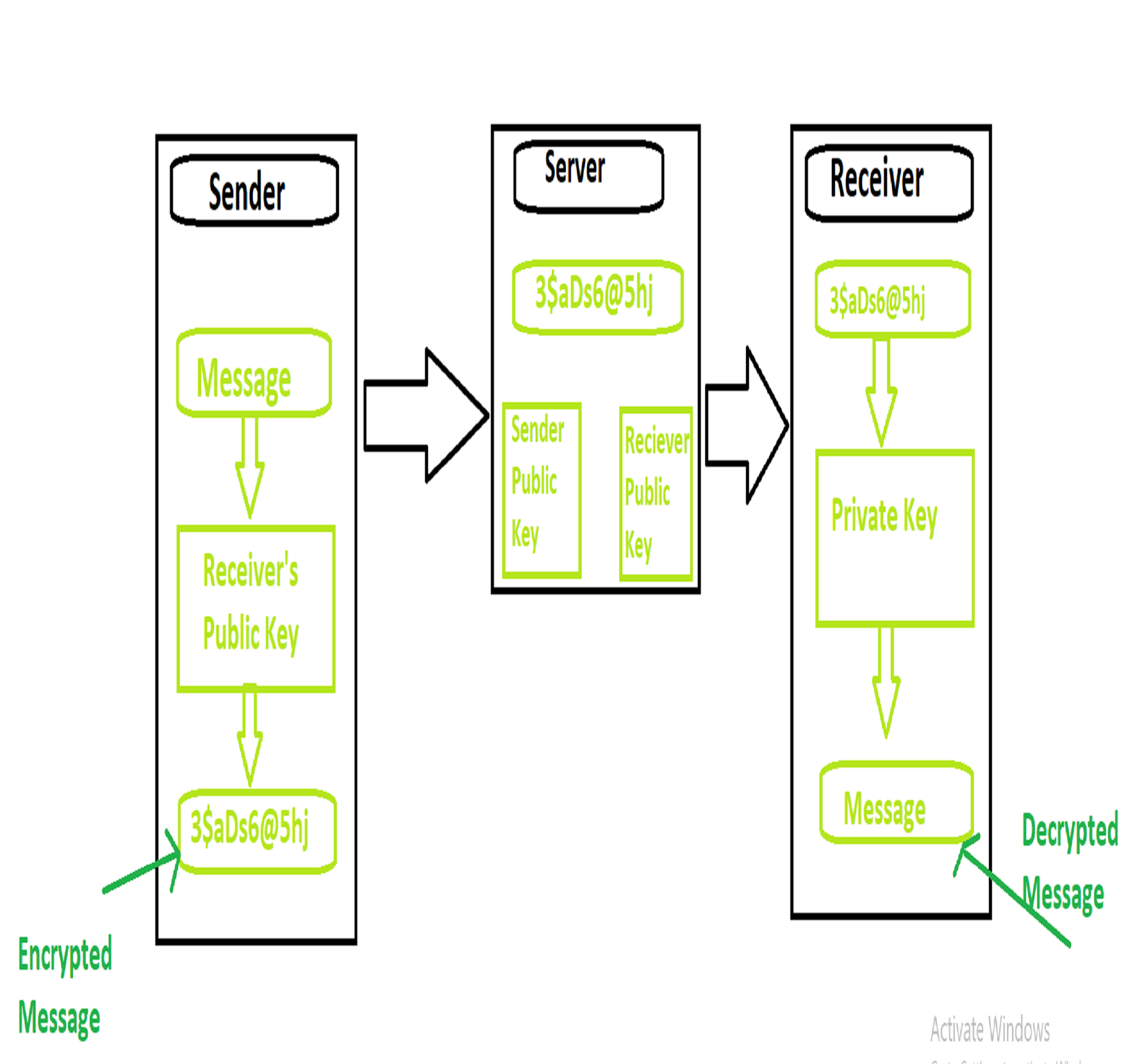
Working of End to End Encryption
- It uses asymmetric encryption technique for data communication between sender and receiver
- Sender pulls down receiver’s public key from the server
- Sender then encrypts the messages to be sent using the public key of receiver
- Sender then send the encrypted messages to the server
- Receiver then receives the encrypted messages from the server
- Receiver then using its private key decrypt the messages
- Receiver the reads the messages
Applications
This method has very high importance in the areas where privacy is very important such as:
- Negotiation and Communications that are very much important and are under threat of being hacked
- Military information that needs to be protected and where the each and every communication needs to be secured
- Areas which involve sensitive issues like health, information about minors, etc
Advantages
- Communication method is highly secure when data travels from sender to receiver
- It provides greater flexibility to the user as it allows to them to decide which data to encrypt.
- It also allows user to decide who has authority to read his messages.
- The end-to-end encryption process consumes less resources and time and the file size is generally small.
Disadvantages
- Some special devices are required for storing the keys.
- It does not protect your data on endpoints
- Insecure encryption algorithm
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...