Cryptography in IoT (Internet of Things)
Last Updated :
15 Mar, 2024
Cryptography plays a vital role in securing information and data through the use of codes that transform the data into an unreadable format without a proper key thus preventing unauthorized access. In simple words, we can say that organizations use cryptography to secure communication channels.
What is IoT?
The Internet of Things (IoT) describes a network of physical devices, like appliances and vehicles, equipped with sensors, and software. These environmentally aware objects can gather data about their surroundings and communicate with other devices to share information. Sensors are a major part of any IoT application. Sensors gather real-time information from the environment such as temperature, pressure, and more. It is massively scalable and efficient with less power.
Let’s look at a real-world example, Modern refrigerators often come with in-built sensors that detect if the door has been left open for an extended period. These sensors trigger an alert system, such as an audible beep to notify the user to close the door so that optimal temperature and energy efficiency can be maintained.
Why Do We Need Cryptography in IoT?
IoT devices pump out large amounts of sensitive data which is not safe in this digital world. Hackers can easily steal valuable information that they shouldn’t have access to. Even worse, they might hijack these devices and use them to spread misinformation or perform malicious attacks. Cryptography can keep IoT devices and the data they transfer secure. Messages come with a special key and they can only be decoded with that particular key.
Here comes the role of encryption that significantly reduce the potential entry points for hackers that target the data between IoT devices which result application incomplete. Although most data undergoes in-transit encryption during web transmission thus centralized encryption are often lacking due to resource limitations.
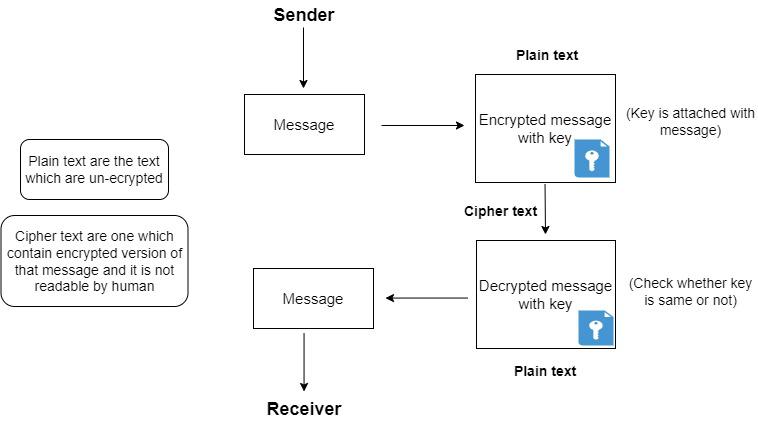
Diagrammatic Representation of Symmetric Key Encryption in Cryptography
Role of Cryptography for Security
With each new IoT device added to the network for data gathering the potential attack for unauthorized access exponentially increases, and which possess a security challenge. Deploying also increases hacking risks because data exists in different Locations. To minimize those risk is where cryptography plays an important factor.
The main task of cryptography is to secure communication channels. For example, developers can use cryptographic Transport Layer Security protocol which encrypts the data to ensure that information remains secured and confidential. This confidentiality allows only the intended recipient to unlock the message and access the information.
There are also other options to secure data by single-key or symmetric-key encryption algorithms such as the Advanced Encryption Standard (AES). In this same key is used for encryption and decryption and necessary to share between sender and reciver.
Whereas there is asymmetric-key encryption which is unlike symmetric. It has two keys that are public key and private key. Public keys can be shared publically but private key can only be accessible to the one who has matched paired key.
Lightweight cryptography is split into two types symmetric and asymmetric Block cipher and stream cipher. Symmetric ciphers use reduce key length.
Advantages of Cryptography in IoT
- Security: Cryptography ensures security by encrypting the data and this make it unreadable to unauthorized person. Layer of protection on data is been added. We can think of it as an financial transaction that is need to be secure and safe.
- Integration of data: To ensure that data reaches to right person and that too without any changes is critical concern in IoT. Cryptography plays a vital role in addressing this challenge as it arrive wuth techniques such as digital signature and message authentication codes to prevent data integration during transmission.
- Authentication of the user: Proper user or device authentication is important in IoT to prevent unauthorized access and safeguard sensitive data. Malicious attacks can exploit and steal information. This is evident in smart home system where authentication ensures only to authorized individuals like homeowner, as he/she can unlock the door using fingerprints or password scanners.
Limitations of Cryptography in IoT
- Encrypted key loss: One challenge with encryption lies in managing the encryption keys. Losing a private key can render the corresponding data inaccessible even to owner also. This highlights the importance to secure key by preventing it from permanent data loss.
- Complexity: Securing and restoring encrypted data in IoT environments presents a significant challenge due to the complexity of the process as we use symmetrical key encryption and with this the chances of attack are higher.Alternative to this is using asymmetrical encryption where data can be prevented but complexity increases.
- Maintenance: It requires high expenses to upgrade and maintain the system.
Frequently Asked Questions on Cryptography in IoT – FAQs
What is Cryptography and why is it important?
Cryptography is a technique that is used to secure the data or the information. The prefix “crypt” means “hidden” and the suffix “graphy” means “writing”. A real-life example of cryptography is WhatsApp’s end-to-end encryption which ensure that the message you send and receive should not be scrambled and readable only to you. It is important because it secure communication channels between two or more devices.
What is IoT?
IoT stands for Internet of Things. It refers to an ecosystem of physical objects with built-in sensors that can gather information from the environment. IoT aims to increase human interconnectedness by allowing individuals to interact with things.
Cryptography is further classified as?
Symmetric Encryption: Single key used for both encryption and decryption. The sender use the secret or the private key to encrypt the message during encryption (plain text to cipher text) and that same is to be used by receiver. AWS and DES are some of the example.
Hash Function: Another method of cryptography that converges numerical data to another compressed numerical value. This function emphasizes gradually increase in levels of complexity and difficulty. Bitcoin, which is the largest cryptocurrency uses a hash function to verify the transaction and secure network.
Asymmetric Encryption: Two different keys (a public key and a private key) are used to encrypt and decrypt the data. The senders use the public key to encrypt the message and it is distributable among other also. The receiver with the paired private key is the authorized person to decrypt the message. Rivest Shamir Adleman (RSA) encryption is a well-known example.
Share your thoughts in the comments
Please Login to comment...