AWS VPC Design Best Practices
Last Updated :
21 Mar, 2024
Designing a Virtual Private Cloud (VPC) on Amazon Web Services (AWS) is fundamental for associations trying to leverage cloud infrastructure efficiently. A VPC serves in as the foundation of AWS cloud environments, giving a secure and isolated network space where different AWS resources can be deployed. Understanding the prescribed procedures for planning an AWS VPC is crucial to ensure scalability, reliability, and security for cloud-based applications and services. By sticking to these best procedures, organizations can advance resource usage, improve network performance, and moderate potential security risks.
This far reaching guide expects to investigate the fundamental parts of AWS VPC configuration, covering terminology, step by step processes, diagrams, and useful models. Through careful planning and implementation, associations can tackle the maximum capacity of AWS VPC to create strong, high-performing cloud architectures that meet the unique requirements of current organizations. Whether sending web applications, databases, or microservices, a very much planned AWS VPC foundation for a strong and agile cloud infrastructure.
Understanding Of Primary Terminologies
- VPC (Virtual Private Cloud): A Virtual Private Cloud is a logically isolated segment of the AWS Cloud where you can send off AWS resources in a virtual network that intently looks like a traditional network setup. It allows you to characterize a virtual network environment, including IP address ranges, subnets, route tables, and network gateways, giving you full command over your network configuration.
- Subnet: A Subnet is a divided part of an IP network within a VPC. It isolates the VPC’s IP address range into smaller, reasonable blocks, allowing you to sort out resources and apply different network designs, for example, access control policies and routing rules, to each subnet.
- Route Table: A Route Table is a bunch of decides that decide how organization traffic is coordinated inside a VPC. It indicates the ways (or courses) for traffic leaving or entering subnets, characterizing whether traffic should to be route locally inside the VPC, to a internet gateway for outside access, or to other network passages for explicit objections.
- Internet Gateway: A Internet Gateway is an evenly scaled, redundant gateway that permits communication between resources inside a VPC and the web. It fills in as the passage and leave point for internet bound traffic, empowering instances in public subnets to get to the internet and permitting external users to get to resources hosted in the VPC.
- NAT Gateway: An Network Address Translation (NAT) Gateway is an managed service that empowers instances in private subnets to start outbound internet traffic while keeping up with security by keeping inbound associations from the internet. It permits private cases to get to programming updates, patches, and other outside administrations without uncovering their private IP addresses.
- Security Group: A Security Group goes about as a virtual firewall for controlling inbound and outbound traffic to AWS assets, for example, EC2 occasions, inside a VPC. It comprises of inbound and outbound principles that determine which kinds of traffic are permitted or denied in light of IP addresses, port reaches, and protocols.
- Network Access Control List (NACL): An Network Access Control list is a discretionary layer of security that works at the subnet level in a VPC. It goes about as a stateless firewall, permitting you to control traffic entering and leaving subnets in view of client characterized rules. NACLs give an extra layer of safety past security groups, permitting you to filter traffic in view of IP addresses and conventions.
What Is VPC?
A Virtual Private Cloud (VPC) is a virtual network environment inside the Amazon Web Services (AWS) cloud platform that permits users to launch and manage AWS resources in a logically isolated section of the AWS Cloud. Basically, a VPC goes about as a virtual data center in the cloud, empowering users to define a virtual network topology that intently looks like a conventional network setup.
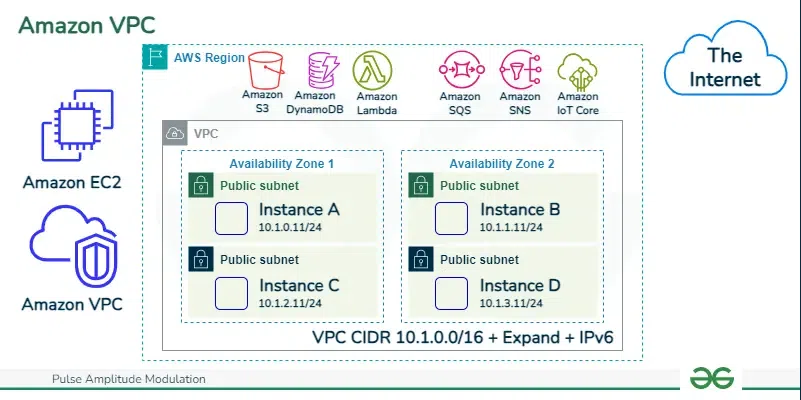
Key Features Of AWS VPC
The following are the key features of AWS VPC:
- Isolation: Each VPC gives logical isolation from other VPCs inside a similar AWS account as well as from the internet. This isolation users to have unlimited control over their network settings, including IP address ranges, subnets, route tables, and network gateways.
- Customization: User can modify their VPC setup to meet the particular necessities of their applications or jobs. This incorporates defining IP address ranges for the VPC and its subnets, making subnets in numerous Availability Zones for high Availability, and designing organization network control policies.
- Security: AWS VPC provides worked in security highlights, for example, Security Groups and Network Access Control Lists (NACLs) to control inbound and outbound traffic to resources inside the VPC. Users can define granular security rules to limit access in based of IP addresses, port ranges, and protocols.
- Connectivity: VPCs can be connected with one another or to on-premises networks utilizing Virtual Private Network (VPN) connections or AWS Direct Connect. This takes into account crossover cloud deployments and consistent integrating among cloud and on-premises environments.
- Scalability: AWS VPCs are profoundly scalable and can accommodate many responsibilities, from limited scope applications to huge enterprise deployments. Clients can easily increase their VPC resources or down based on demand, without the requirement for manual intervention.
Components Of AWS VPC
The following are the key components of AWS VPC:
- Subnets: Subnets are portions of the VPC’s IP address range where users can put AWS resources. Subnets are related with explicit availability zones and can be either public or private. Subnets are like breaking a large network into sub-networks. Maintaining a smaller network is easy as compared to maintaining a large network.
- Route Tables: Route tables characterize how organization traffic is coordinated inside the VPC. They determine the ways (or courses) for traffic leaving or entering subnets, internet traffic to internet gateways, virtual private gateways, NAT gateways, or other network destinations. Route table can be understood as a table that contains rules for routing traffic within and outside a subnet. The route table is also used to add Internet Gateway to the subnet. There can be multiple route tables in a VPC.
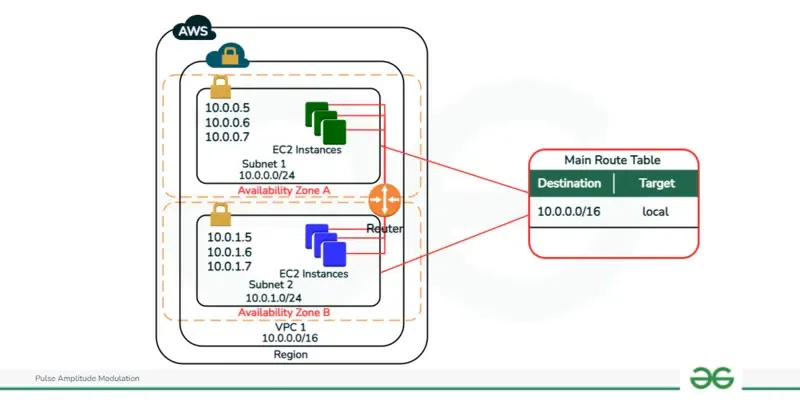
- Internet Gateway (IGW): A Internet Gateway empowers correspondence between instances inside the VPC and the internet. It fills in as the section and leave point for internet bound traffic and is connected to the VPC. Internet Gateway allows instance to connect to the internet. It allows the user to make the subnet pubic by providing a route to the internet. With the help of Internet Gateway, an instance can access the internet and the resources outside instance can access the instance.

- NAT Gateway/NAT Instance: Network Address Translation (NAT) Gateways or NAT Instances allow instances in private subnets to start outbound internet traffic while keeping inbound traffic from reaching them. They work with internet availability for resources in private subnets.

- Elastic IP Locations (EIPs): Elastic IP addresses are static IPv4 addresses designed for dynamic distributed computing. They can be related with instances or organization interfaces and give a tireless public IP address that can be remapped to different instances.
- Security Groups: Security Groups go about as virtual firewalls for controlling inbound and outbound traffic to EC2 instances, RDS instances, and different resources inside the VPC. They comprise of decides that characterize permitted or denied traffic in view of protocol, port, and source/destination IP address.
- Network Access Control Lists (NACLs): NACLs are stateless, discretionary firewalls that control traffic at the subnet level. They allows users to define rules to allow or deny traffic in view of IP addresses, port reaches, and protocols.
AWS VPC Design Best Practices
The following are the AWS VPC Desing best practices:

- Properly Plan IP Address Space: Design the IP address range for the VPC in view of future versatility. Designate CIDR blocks efficiently and stay away from cross-over with on-premises networks.
- Use Multiple Availability Zones: Deploy subnets across various Availability Zones for adaptation to internal failure and high accessibility. Appropriate resources equitably to keep away from failure.
- Separate Resources With Public And Private Subnets: Place internet facing resources (like web servers) in public subnets and backend resources (like databases) in private subnets. This division upgrades enhances by security isolating resources from the web.
- Implement Least Privilege Security Groups: Follow the principle of least privilege while arranging Security Groups. Just open vital ports and conventions for inbound and outbound traffic and limit admittance to resources in view of specific prerequisites.
- Monitor And Audit Network Traffic: Empower VPC Flow Logs to catch data about inbound and outbound traffic coursing through network interfaces inside the VPC. Use CloudWatch Logs or third-party monitoring tools to break down and review network movement for security and consistency purposes.
- Utilize AWS Managed Services: Leverage AWS Managed Services like NAT Gateways, AWS Transit Gateway, and VPC Peering to improve on network availability and management tasks. These services give scalable and dependable solutions for routing, availability, and network traffic management.
- Regularly Review And Update Design: Continuously review and update your VPC design to line up with advancing business requirements, best practices, and new AWS features. Consistently review security configurations and advance resource usage for further developed execution and cost efficiency.
Conclusion
Designing a Virtual Private Cloud (VPC) on Amazon Web Services (AWS) with best practices is fundamental for accomplishing ideal execution, security, and scalability in cloud architectures. By observing the guidelines framed in this guide, organizations can ensure their VPCs are robust and well-architected.
Powerful VPC configuration includes contemplations like legitimate subnetting, routing, security group setups, and multi-Availability Zone deployment to upgrade security, reliability, and accessibility. These practices empower associations to safeguard their assets from unapproved access, relieve dangers of personal time because of failures, and scale their infrastructure to satisfy developing needs.
Utilizing AWS Managed Administrations like NAT Gateways and Travel Gateway improves on network availability and management tasks, smoothing out activities and lessening intricacy. Constant observing and streamlining of VPCs utilizing apparatuses like VPC Flow Logs and CloudWatch measurements permit associations to distinguish and cost inefficiencies.
AWS VPC Design – FAQ’s
Could I Change The IP Address Range Of A Existing Vpc?
No, the IP address scope of a VPC is permanent whenever it’s made. You want to make another VPC to change the IP address range.
What Number Of VPCs Could I Create In My Aws Account?
By default, you can make up to 5 VPCs per AWS region. You can demand a limit increase on the off chance that you want to make more VPCs.
Could I Peer VPCs In Various AWS Accounts?
Yes, you can lay out VPC peering connections between VPCs in various AWS accounts as long as the two players support the peering request.
What Is The Difference Between A Public Subnet And A Private Subnet?
A public subnet has a route to a internet gateway, permitting resources inside it to have direct admittance to the internet. A private subnet, then again, doesn’t have an direct route to the internet and regularly has backend services or databases that should not be directly open from the internet.
How Would I Troubleshoot Network Issues Inside My VPC?
You can utilize VPC Flow Logs to catch data about the IP traffic going to and from network interfaces in your VPC, which can assist with diagnosing connectivity issues. Also, you can utilize devices like AWS CloudWatch Logs and VPC endpoint monitoring to monitor network performance and troubleshoot issues.
Share your thoughts in the comments
Please Login to comment...