Automated Secure Code Review
Last Updated :
02 Nov, 2020
Static application security testing (SAST) review source code of applications to identify security flaws that can make applications susceptible to breaches. It is considered as white box testing. SAST tools finds security flaws in an application (with lots of false positives) however it just serves as an aid for a cybersecurity analyst to help them zero in on security relevant areas of code so they can find vulnerabilities more efficiently.
How to perform Code Review Assessment via available SAST tools ?
Here we will be learning how to review reports generated by security assessment tools for code review. The report format is similar across various tools and we will discuss some main factors to be considered during assessment.
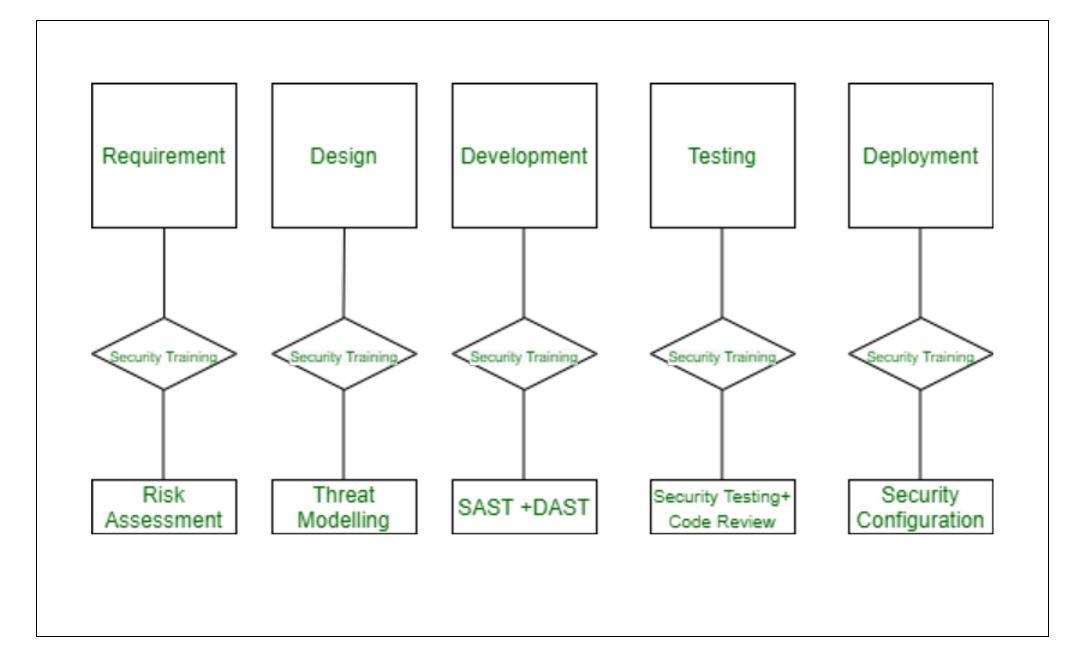
Vulnerabilities may exist in application due to insecure code, design or configuration. Automated security analysis can be carried on code to identify vulnerabilities through either of following two options :
- Static code scanner scripts based on a pattern search (in-house and open source).
- Static code analyzers (commercial and open source).
How SAST tools work ?
SAST tools examine code without attempting to execute it. They are integral part for Descopes strategies and hence a lot of research and POC is done to identify an apt tool for an organization.
Advantages of SAST tool :
- Reduction in manual analysis efforts by an analyst.
- Effective and efficient in identifying all the instances of a particular vulnerability.
- Elaborate automated reporting format.
Disadvantage of SAST tool :
- Business logic flaws remain undetected.
- Security controls implemented in the application specific to its features and design are often undetected.
- Great number of false positives are detected.
So anyone hoping that secure code checking can be automated completely by running SAST tool at end of build will be disappointed as there is still a deal of manual intervention required by security analysts.
While all tools almost have similar functionality, you should understand and work on any one tool and would be able to use any SAST tool. You can always find a guideline on how to use a particular tool on websites.
What to focus on analyzing the report generated from SAST tool?
- Focus on vulnerability identified and on number of instances it is reported for. Vulnerability details, mitigation and references are always available in report for better understanding.
- Always look through vulnerability graph to see what is source(entry point of vulnerability) and sink (vulnerability execution point) for better understanding.
For eg : if we have input validation issue reported for a text box we need to see where value is being entered and where entered value will be executed. We need to check what values are allowed for this parameter and if we have validation in place or not. If validation is missing we will check if this value can execute as Cross-site scripting payload or will this value be stored in database and can act as SQL injection payload (there can be more scenarios related to it).Based on such analysis, vulnerability is marked as a false-positive or a true positive
- After a vulnerability is identified assign severity based on CVSS. Severity provided by automated tools are generally incorrect and should be reviewed by a security analyst. Share reported vulnerability with developer suggesting them mitigation steps.
Generally automated tools generate a lot of false-positives so it is important for a Security Analyst to go through each instance of vulnerability being reported and verify. Due to high number of false positives, a security analyst intervention is always required for refining report and sharing true positives with developers.
Here is a list of some popular SAST tools that can be used for Secure Code Review Assessment :
| Commercial |
Open-Source |
| Fortify Static Code Analyzer |
Reshift Security |
| Checkmarx CxSAST |
Brakeman |
| Coverity Scan |
Findbugs |
| Veracode |
JsHint |
| AppScan |
CodeWarrior |
Share your thoughts in the comments
Please Login to comment...