What is Network Traffic Analysis in Cybersecurity?
Last Updated :
26 Apr, 2024
Network traffic analysis (NTA) is a way of monitoring network availability and activity to identify anomalies, such as security and operational issues. Network Traffic Analysis in Cybersecurity means monitoring the data that goes through a computer network. It helps to detect and prevent bad things from happening in the network like hackers trying to get in or viruses trying to spread.
What is Network Traffic Analysis?
Network Traffic Analysis (NTA) is a process of monitoring the data that moves through a computer network. This helps us understand how the network behaves, performs, and stays secure. By checking the patterns, protocols, and volume of data, you can see how devices on the network communicate with each other. NTA lets network administrators and security professionals keep an eye on network performance, find security risks, solve network problems, understand how the network is used, and collect data for compliance and auditing. This article will focus on how NTA is used in cybersecurity.
How to Implement Network Traffic Analysis?
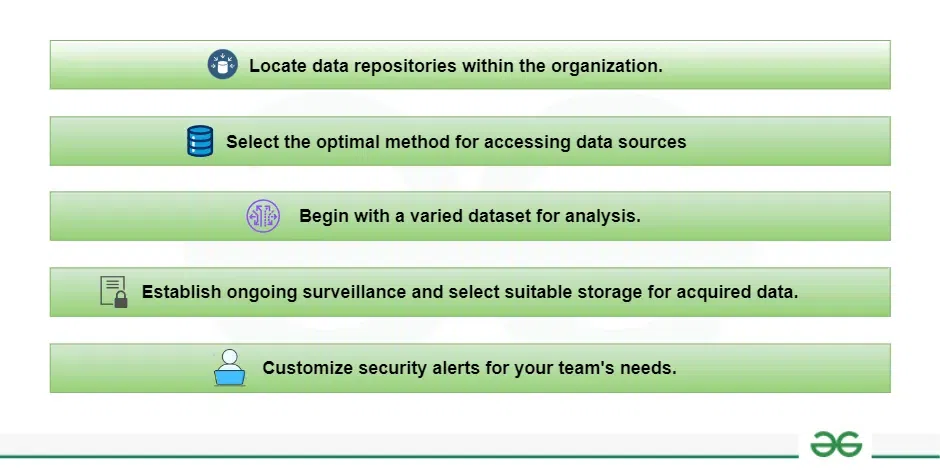
Network Traffic Analysis
Benefits of Network Traffic Analysis in Cybersecurity
- Better Understanding: You gain clearer insights into which devices are connecting to your network.
- Legal Compliance: It helps you meet legal requirements.
- Problem Solving: You can investigate and fix operational and security issues more effectively.
- Quick Responses: With detailed information and extra context about your network, you can respond to issues faster.
What is the Purpose of Monitoring Network Traffic in Cybersecurity?
- Identifying Issues: Network traffic analysis helps in identifying problems related to how data moves across your network. This includes spotting large file downloads, streaming activities, and any suspicious incoming or outgoing traffic.
- Enhanced Visibility: By monitoring traffic at various points in your network (like firewalls), you can track specific actions back to individual users or devices. This helps in understanding who is doing what on your network.
- Threat Detection: Network Traffic Analysis in Cybersecurity provides a deeper insight into potential threats beyond just looking at individual devices. This is crucial as more devices like mobiles, IoT devices, and smart TVs connect to networks. Regular firewall logs may not capture all relevant information during an attack.
- Use Cases: Monitoring network traffic helps in various scenarios such as detecting ransomware attacks, keeping an eye on data leaving your network (data exfiltration), tracking file or database access, understanding user behaviors maintaining an inventory of network assets, identifying causes of network performance issues, and providing real-time dashboards and reports for network and user activities.
How Does Network Traffic Analysis Enhance Your Security?
- Network understanding: Network Traffic Analysis solutions can help businesses improve security by providing improved insight into their networks and identifying unusual network activity that could suggest a potential attack.
- Threat Identification: Network Traffic Analysis can assist an organization in detecting threats, allowing for the identification of cyberattacks.
- Troubleshooting: Network Traffic Analysis solutions can help identify when a system is down and provide information that can be useful for diagnosing and correcting the problem.
- Investigation Support: Network Traffic Analysis systems capture network traffic data for analysis and can save it for later use.
- Threat Intelligence: Once a threat has been identified, an NTA solution can extract distinct features, such as IP addresses, to create indicators of compromise (IoCs).
The Importance of Network Traffic Analysis in Cybersecurity
- Spotting Bad Behavior: Think of network traffic analysis as a security guard for our computer networks. It watches all the data going in and out of our systems. If it sees anything strange or suspicious, it raises an alarm. This helps us catch hackers before they can do any damage.
- Preventing Attacks: Sometimes, hackers try to sneak into our systems by pretending to be normal traffic. Network traffic analysis can uncover these sneaky attempts and stop them before they cause trouble. It’s like having a super-smart detective that can see through disguises!
- Identifying Patterns: Hackers often have patterns in the way they attack. They might use similar techniques or target the same parts of our networks. Network traffic analysis looks for these patterns and warns us if it sees anything fishy. This helps us stay one step ahead of the bad guys.
- Protecting Data: Our networks hold lots of important information, like passwords, financial data, and personal details. Network traffic analysis helps us keep this data safe by watching who’s trying to access it and making sure only the right people get in.
- Staying Updated: Cyber threats are always changing and evolving. Network traffic analysis helps us stay on top of these changes by constantly monitoring our networks for new tricks and tactics used by hackers. This way, we can adapt our defenses to stay safe.
Why Companies Need network Traffic Analysis Solution to Strengthen Cybersecurity
- Flow-enabled devices: Check if your network has devices that can generate the specific data flows needed by certain NTA tools (like Cisco Netflow). DPI tools, on the other hand, can work with raw traffic from any managed switch, making them more flexible.
- Data sources: Different tools gather data from different places in your network. Make sure the tool you choose collects the data that’s most important for your needs.
- Monitoring points: Decide if you need a tool that uses agents or not. Also, start by monitoring key areas in your network where data comes together, such as internet gateways or critical server VLANs.
- Real-time vs. historical data: Consider if you need to analyze past events or if real-time data is enough. Some tools may not keep historical data, so check this before deciding.
- Full packet capture: DPI tools can capture and store all data packets, but this can be costly and complex. Some tools focus on extracting key details from packets, reducing data volume while still providing valuable insights for both network and security teams. Choose based on your needs and budget.
Conclusion
Network Traffic Analysis in Cybersecurity is a vital practice for keeping computer networks safe from threats. It involves monitoring and analyzing data moving across networks to detect and prevent malicious activities. By understanding normal traffic patterns, anomalies can be identified and addressed promptly, helping to prevent cyberattacks and protect sensitive information.
Frequently Asked Question on Network Traffic Analysis – FAQs
Why is Network Traffic Analysis important?
Network Traffic Analysis is important because it helps to identify abnormal activities on networks, allowing organizations to detect and prevent cyberattacks before they cause harm.
How does Network Traffic Analysis work?
Network Traffic Analysis works by monitoring data packets as they move across networks, analyzing patterns and behaviors to identify potential security threats.
What are the applications of Network Traffic Analysis?
Network Traffic Analysis can be used for various cybersecurity purposes, including intrusion detection, network performance monitoring, and identifying unauthorized access attempts.
What are the pros and cons of Network Traffic Analysis?
Pros include early detection of cyber threats, improved network performance, and better understanding of network activity. Cons may include false positives, resource-intensive analysis, and the need for skilled personnel to interpret results.
Share your thoughts in the comments
Please Login to comment...