Social Engineering Techniques in Metasploit
Last Updated :
23 Dec, 2022
The Social-Engineer Toolkit (SET) was developed to coincide with the release of social-engineer.org. The purpose of SET is to fill a gap in the penetration testing community and bring awareness to social-engineering attacks. the toolkit attacks human’s weaknesses, exploiting curiosity, and simple human stupidity. Social-Engineering Attacks are at an all-time high and have always been a large risk for any organization.
Social-Engineering is nothing but one person trying to coax another person to perform acts that he normally wouldn’t do is called social engineering. Many security communities believe that social engineering is one of the biggest risks that an organization can face. SET categorizes attacks by attack types(web, email, and USB-based). It uses email, spoofed websites, and other vectors to reach human targets and trick individuals to compromise sensitive information.
SET heavily uses Metasploit Framework, because of the social nature of the attacks themselves.
To install SET in a Linux environment you can refer to how to install social engineering toolkit in kali linux .
There are many techniques in SET as listed in the image below:
root#-/ setoolkit
1. Spear-Phishing Attack vectors: These attack vectors are mainly focused on Mass email attacks through which a target system can be acquired easily. In this attack attacker first, prepare a Clone of the website of a utility that is used by the majority of users like social media websites or eCommerce websites, then within these email either payloads are attached or the links are set to listen at some fake port so that attackers get the details of the user whenever they click the link or go over website. This attack uses HTML based approach to perform most of the attacks because these attacks are delivered by email, which makes the email service the most common way for phishing attacks like this. even these days we all receive lots of spam emails regarding different offers, bank claims, etc. active groups of attackers rely on it for credential theft, ransomware, and other forms of financial gain.
many options come with this attack vector:
- Perform a Mass Email Attack: with this option attacker can perform an attack on a large number of emails in a single instance, this attack is used when the attacker wants to target a large number of targets or just want a hit and trial to get a victim.
- Create a File Format Payload: a file payload allows an attacker to push files to Android devices for access by other applications on the device. the file delivered will consist of a payload sent to an external SD card location by default.
- Create a Social-Engineering Template: with this method, an attacker can create a new template with multiple additions and customize the attack’s whole process.
2. Website Attack Vectors: Web attack vectors are probably one of the most advanced and exciting methods/ option that comes with SET because they are specifically made to be believable and enticing to the target. SET can clone websites that look identical to trusted sites, like social media websites, and other websites where a user is required to fill in the authentication details, and this will help to ensure that the target will think he/she is visiting a legitimate site.
Web Attack vectors also offer different types of attacks:
- Java Applet Attack Method: the java applet attack is one of the most successful attack vectors in SET. The applet itself was created by one of the SET developers. with this attack comes a malicious Java Applet that does smart browser detection so that the exploit work without any problem and delivers a payload to the target system. When the target browses a malicious website, he is presented with a warning asking if he wants to run an untrusted java applet. because java allows you to sign an applet with any name you choose. so you could call the publisher of any string you choose like Google, Microsoft, or any other.
- Metasploit Browser Exploit Method: SET can also use client-side web exploits. A client-side exploit is directly imported from Metasploit and used to attack the targeted system. To use this attack you must rely on your prior reconnaissance or hope that the user is susceptible to a specific vulnerability.

- Credential Harvester Attack Method: Through this attack, an attacker can harvest or get the credentials of users, SET can create a clone of the Gmail website and then automatically rewrite the POST parameters’ of that website to the SET server which will end up redirecting the user to the legitimately cloned website.
- Web Jacking Attack Method: this method allows an attacker to create a website clone, where the target is presented with a link stating that the website is moved. when the target hovers over the link, the URL is presented in the real URL, Not the attacker’s URL. and when the target clicks the link it opens but it is quickly replaced with the attacker’s malicious web server. This attack uses a Time-based iframe replacement.
3. Infectious Media Generator: The infectious media generator is a relatively simple attack. with this, SET creates a folder that you can either burn to a CD/DVD or store on a USB drive. The autorun inf file is used, which when you insert it into the target machine, will get execute whatever you specify during attack creation.
4. Create a Payload and Listener: This option is used to create an executable payload and a listener. The SET will use Metasploit to create an executable file that can do several defined malicious actions to the victim’s computer. The listener is used to monitor or control the activities of the payload and with this listener setup you have all the access to the target machine, you can control files, manipulate them and even control the webcam and microphones while sitting far away on your chair with a shell.
- An attacker needs to physically install this executable on the target machine and run it, this can be done by plunging the malicious USB drive that contains the payload.
- While this method is effective but not favorable because it is hard to get hold of the target computer/machine sometimes and install or run the executable.
5. Mass Mailer Attack: This attack is used to send emails to the targeted person which contain phishing links to the websites, and are further used to steal and gain access to the valuable information of the victim. It is called mass mailer attacks because it allows you to send emails with phishing links in a bulk, which means you can even send these emails to hundreds of victims in one shot.
- With these attacks, attackers can get the credentials like bank details, credit card details, and much more information without being suspicious.
let’s see how this attack is being done, follow up the commands mentioned below:
root#-/ setoolkit
root#-/ setoolkit
set> 1
set> 5
set> 1
set:phishing> send email to: iamunknown0208@gmail.com
set: phishing>1
set: phishing> your Gmail email address: lucifer24hours@gmail.com
set: phishing> The from name the user will see: lucifer2411
email password: *********
Choose from the options available, like attach a file yes or no, set this message a priority yes or no, and when you are done type END and press enter.
you can see that the victim received the mail from the attacker.
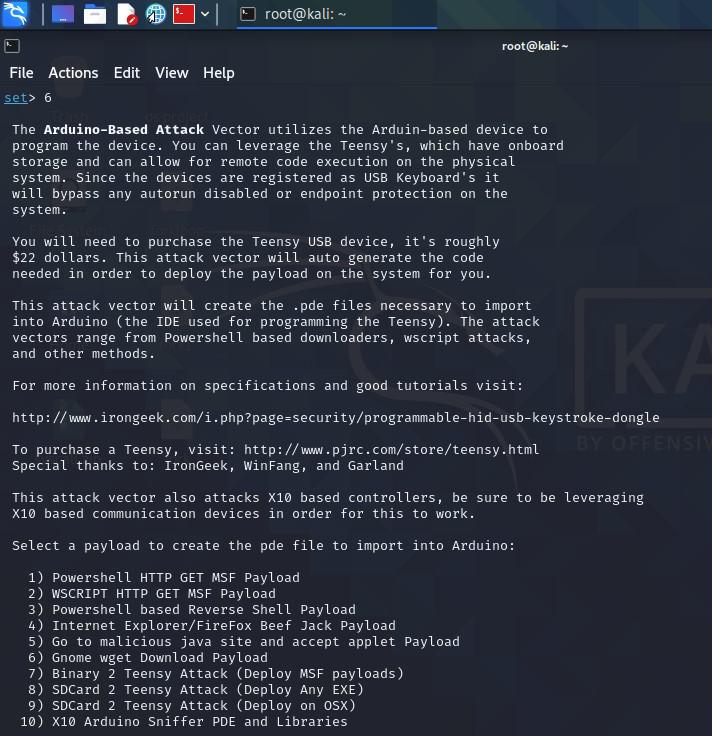
6. Arduino-based attack Vectors: In this attack, the vector attacker uses the Arduino-based device to program the device. This attack basis on the IoT category, it will auto-generate the code needed to deploy the payload on the system for you. to import the necessary files into the Arduino it uses the ide called Teensy, the files are created with .pde extensions. These attacks are useful when you are targeting IoT devices like a Home automation system or some devices that have sensors like fingerprinting, biometric bypass, etc.
7. Wireless Access Point Attack vectors: This attack uses modules to create a fake access point for your wireless card and redirect all DNS queries to you. with the use of SET, you can create a fake wireless access point with a DHCP server and perform DNS Spoofing to redirect all the traffic to your machine from the victim’s computer, this will help you to monitor the network traffic. This uses external exploitations software which you can download easily like AirMon-NG, DNSSpoof, dhcpd3, etc.
8. QRcode Generator Attack Vectors: As the name suggests it generates a QR code with a URL of your own choice. when you have the QR code generated, you can easily select an attack from SET and deploy this QR code to your victim.
9. PowerShell Attack Vectors: last by not least, the PowerShell attack vectors allow the creation of PowerShell-specific attacks. this attack will allow you to use PowerShell which is by default available in all operating systems, like windows vista, XP, and others. It provides an interface to deploy payloads and functions that do not get triggered by preventative or security technologies.
it also has a bunch of options available:
1. Powershell Alphanumeric Shellcode Injector
2. Powershell Reverse Shell
3. Powershell Bind Shell
4. Powershell Dump SAM Database
Conclusion:
Additional SET features:
- One tool of note is the SET Interactive Shell, which can be selected as a payload instead of a meterpreter. another feature is RATTE (Remote Administration Tool Tommy Edition) is a full HTTP tunneling payload. it relies on HTTP-based communications. RATTE is particularly useful when the target uses packet inspection rules that can detect non-HTTP traffic.
- Two other tools include the SET WEB-GUI and wireless attack vectors also. to run set web-GUI enter the command ./set-web. From set home folder. this web GUI is written in python programming language and is a great way to perform attacks from the web interface. The wireless attack vector creates an access point on the attacker’s machine and whenever the target connects to the access point, any website visiting target is redirected to the attacker’s machine. after which multiple SET attacks
Share your thoughts in the comments
Please Login to comment...