Maintaining Access Tools in Kali Linux
Last Updated :
21 Aug, 2023
Maintaining Access is the 4th phase in the ethical hacking process. In this phase, the hacker installs software or makes changes to the target machine to access the target later in time. This allows the hacker to stay connected with the target machine, thus cutting the need of starting the process from scratch for the same target. This phase is also called persistence in the target system.


The various methodologies used in the ‘maintaining access‘ phase are as follows: –
- Backdoors: Backdoors are basically used to bypass login or authentication. This means that a hacker doesn’t need to undergo the same login procedure as a regular user of the system.
- Creating new users and escalating privileges: After exploiting the target, new users are created in it to be used by the hacker whenever required. The privileges of this particular user are then escalated to the super user level, thereby allowing the hacker to use the target machine just like the admin or root user.
- Rootkits: A rootkit is basically malware that has the power of a root user. It allows remote execution of code, modification of configuration files, and many other functions to be used by the hacker.
- Trojans: These are malware in disguise. They expose their original intention only after successfully penetrating through firewalls and other security features of the target system. Trojans are hard to detect, even with smart antivirus software.
- Exfiltration: This process involves transporting any kind of data from the target system to any other location as per the motive of the hacker. This leads to data breaches and leaks in the target machine.
Kali Linux Tools for Maintaining Access
Kali Linux is a Debian-based Linux distribution that is designed for the sole purpose of penetration testing. It comes with tons of pre-installed hacking tools for all phases of ethical hacking. Under the post-exploitation category, you can find several hacking tools that are meant for maintaining access. These tools can be broadly classified into the following classifications: –
- OS back doors
- Tunnelling and exfiltration
- Web back doors
In this article, we will discuss some of the important and popular maintaining access tools in Kali Linux.
Note
- Angular brackets ‘<>’ are used as place holders in the commands mentioned. Please replace the place holders with suitable content.
- If you get a ‘permission denied’ error while executing any of the commands, prefix the command with ‘sudo’ to execute the command as super user.
- The knowledge acquired through this article can be used for educational purposes only.
Tool 1: pwnat
pwnat is used to set up a proxy server that works behind a NAT (Network Address Translation) type of network that accepts connections from any number of clients behind NATs, without any 3rd party.
sudo apt install pwnat
Once the tool is installed in your Kali Linux machine, you can use the help option to get a list of available operations in this tool.
pwnat -h

We use pwnat in two ways: as a server and as a client. So that we will be able to understand the core usage of this tool. Let’s start by setting up a pwnat server using the command below.
sudo pwnat -s 8080
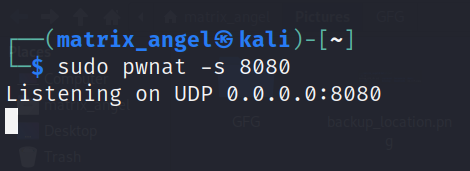
For simplicity, I’m running both the server and the client on the same machine. Now, open another terminal and initiate a pwnat client in order to connect to the server which is running already. Let’s connect to geeksforgeeks.org from our pwnat client, using the pwnat server as a proxy. The command to do the same is given below.
sudo pwnat -c 8080 127.0.0.1 geeksforgeeks.org 443

Once the connection is established, the server continuously displays status messages in the terminal.
sudo pwnat -s 8080

Explanation
- The flag ‘-s‘ stands for server and ‘-c’ stands for the client.
- The server is listening on port 8080. So, the client needs to connect to the same port. The IP address given for the client to connect to is called the loopback address, which is the address of the local machine.
- The domain name to send requests is provided along with the port number 443 which is dedicated to https traffic.
Tool 2: weevely
weevely is a built-in tool in Kali Linux that aims at generating payloads that can be used as back doors on targeted web servers. weevely also provides options to connect to the back door via the terminal and execute remote commands.
Enter the name of this tool in your terminal to check if it is installed on your machine.
weevely
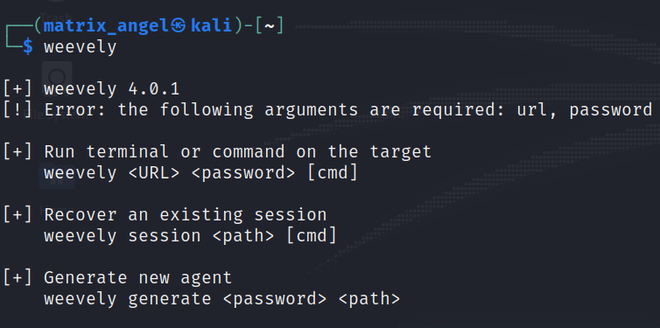
If you see this list of available options in the terminal, you have weevely already installed it. Else, enter the following command to install weevely.
sudo apt install weevely
Let’s now create a sample php web back door to learn the usage of this tool. In the above screenshot of weevely options, you can see the syntax for creating a new agent which is nothing but a new payload. We are going to use the same syntax here.
weevely generate GFG123 /home/matrix_angel/Desktop/backdoor.php
Explanation
- <password> is the argument where you will enter the password for the back door which you are going to generate. This is to ensure that only you will be able to access the back door.
- <path> argument specifies the directory path where your newly created payload is going to be saved.

Now you can list out the contents of the directory using the ‘ls‘ command to find the payload present in it.
ls

Since this procedure is a part of post-exploitation, We assume that you have already found a way to upload this payload to the target web server. Once the upload is completed, you will be able to open a session with the web server and access its data.
powersploit is a collection of Microsoft PowerShell modules that are used for a wide range of assessments that can be done after exploiting a machine, by an authorized penetration tester. Basically, it is a collection of executable scripts. It can be used to do the following assessments:
- Code execution
- Script modification
- Persistence
- Antivirus bypass
- Exfiltration
- Mayhem
- Privilege escalation and
- Reconnaissance
This tool is on our list of maintaining access tools due to its capability to achieve persistence in the target machine.
Simply enter ‘powersploit‘ in the terminal and hit ‘enter’ to change the directory to where powersploit is located.
powersploit

Each of these listed directories consists of various scripts to be utilized by a penetration tester. Let’s take a look at a command that uses powersploit scripts to find and exploit a vulnerability.
Get-NetWMIObject -Class win32_service -Filter "name='msftpsvc'" -ComputerName <TargetHostName> | Invoke-MS17-010
Explanation
- The ‘Get-NetWMIObject’ script queries the WMI (Windows Management Instrumentation) service running in the target machine for the availability of ‘msftpsvc‘ which stands for Microsoft FTP service.
- If a vulnerability is found in this service, the script ‘Invoke-MS17-010’ executes and attempts to exploit the vulnerability.
Tool 4: sbd
sbd stands for Shadow integer Backdoor. It is Netcat-clone which is designed to enhance portability and security. It implements AES-CBC-128 + HMAC-SHA1 which is a strong encryption algorithm. If you are not familiar with Netcat, it is a simple tool that can be used to read and write data across a network. Basically, sbd acts as an OS backdoor and helps to connect to a victim’s machine at any time on a specific port and send commands remotely,
This tool is built-in in Kali Linux. You can use the below command to check if the tool is available on your machine.
sbd -h
This command will return a list of options available in this tool. After successfully exploiting the target machine, you can set up a sbd server in the target machine which acts as a backdoor and keeps listening for incoming connection requests. The syntax for the command to setup a sbd server is given below: –
sbd -l -p 7986 -c off -P "GFG_Ethical_Hacker" -H

Explanation
- The ‘-l’ flag stands for listen, as this is a server.
- The ‘-c‘ option is used to set encryption on or off.
- The ‘-H‘ flag is used to highlight and differentiate the message received from the client.
Now, let’s connect to the listening sbd server via telnet. The command to use can be seen below.
telnet localhost 7986

Explanation
- You need to provide the IP address of the target machine where the sbd server is running. Since I’m experimenting within a private environment, I’m connecting to localhost.
- Specify the same port number in which the server is listening to connections, which is 7986 in my case.
We have successfully connected to the target machine via telnet. We could also execute programs like bash by using the ‘-e’ option while setting up our server.
Conclusion
The ‘maintaining access’ phase is a crucial stage in the ethical hacking process as it determines the availability of access to the target in the future. If this phase gets failed, the whole process needs to be started from the beginning. The built-in tools of Kali Linux for maintaining access provide a handy way to successfully complete this phase with ease. This is one of the many features of Kali Linux that makes it a sophisticated OS for ethical hacking and penetration testing.
Share your thoughts in the comments
Please Login to comment...