How to restrict a user’s login to certain times of the day or week in linux?
Last Updated :
06 Mar, 2024
In this article, we explore the significance of time-based user login restrictions in Linux as an important security measure. By leveraging Pluggable Authentication Modules (PAM) and time configuration files, administrators can define specific periods when users are allowed or denied access. This detailed article outlines the step-by-step process, consisting of the importance of such restrictions for security enhancement, compliance, resource conservation, and user accountability. Additionally, we touch upon the integration of banner messages to notify users during SSH login attempts, contributing to a robust and secure Linux environment.
How to restrict a user’s login to certain times of the day or week in Linux?
In this section, we will explore the detailed steps to restrict a user’s login to certain times of the day or week in a Linux environment. So, follow the below-specified steps with proper command execution.
Step 1: Open the Time Configuration File
Launch the terminal and execute the command vim /etc/security/time.conf to access the critical file for specifying time-based access rules in the Linux system.
vim /etc/security/time.conf
 Step 2: Set Time-Based Rules
Step 2: Set Time-Based Rules
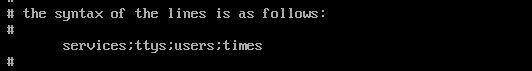
Uncomment the line in the “time.conf” file that follows the format “service;ttys;user;time;” where you define service (e.g., sshd for SSH), ttys (terminals or devices, * for all), user (specific user or * for all users), and time (e.g., Al1900-2300 for a specific time range). This line establishes the parameters for time-based login rules.
<service>;<ttys>;<users>;<times>
<service>: Mention the PAM service (e.g., sshd for SSH) for which you are setting the rules.<ttys>: Specify terminal lines or devices; use * to indicate all terminals.<users>: Define the user or users to whom the rule applies; * implies all users.<times>: Specify the time range using a format like Al1900-2300 for a certain period, indicating access is allowed during 1900 to 2300 hours.
Step 3: Modify “time.conf” File
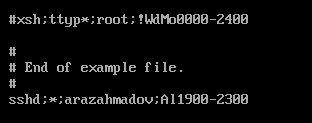
Open the “time.conf” file using the command vim /etc/security/time.conf and append the line sshd;*;username;Al1900-2300 to the end. This specific line restricts the user “username” from accessing the SSH service during the time range from 1900 to 2300 hours. Adjust the username and time range as needed.
vim /etc/security/time.conf
Step 4: Save and Exit
After adding the desired rules to the “time.conf” file, save the changes and exit the text editor. In Vim, you can achieve this by pressing Esc to enter command mode, typing :wq to write changes and quit, then pressing Enter.
Step 5: Modify “/etc/pam.d/sshd” Configuration
Open the “/etc/pam.d/sshd” file using the vi command:
vi /etc/pam.d/sshd
Add the following line at the end of the file:
account required pam_exec.so /usr/bin/test -r /etc/security/time.conf && /usr/bin/egrep -q "sshd;[^;]+;arazahmadov;Al1900-2300" /etc/security/time.conf
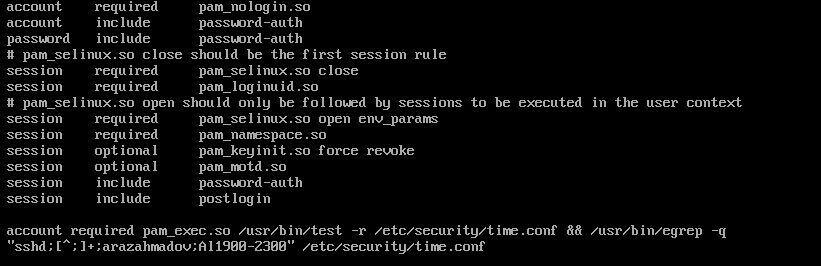
This PAM configuration line checks if “/etc/security/time.conf” file is readable, and if so, it further checks if the specified pattern exists in that file. If both conditions are met, it likely means that access is not allowed for the specified user during the mentioned time range.
Step 6: Restart the SSH Service to Apply Changes
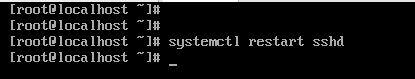
Execute systemctl restart sshd to activate the configured time-based login restrictions. This restart ensures that changes made in the PAM configuration for SSH take effect immediately.
systemctl restart sshd
Step 7: Restricting User
Attempt to log in during the restricted time period to verify that the configured time-based access restrictions are functioning as intended. If successful, users will be denied access outside the specified time range.
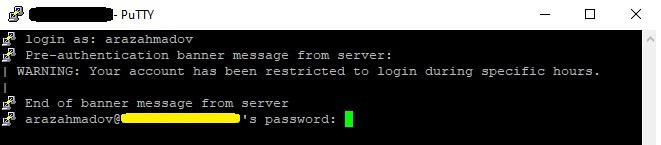
To display a banner message when a user tries to access a server via SSH (using PuTTY or any other SSH client), you can modify the SSH configuration file on the server. The configuration file is typically located at “/etc/ssh/sshd_config”. So, before modifying the mentioned file, you’ve to create a specific banner message file.
Conclusion
In conclusion, implementing time-based user login restrictions in Linux through PAM and time configuration files is crucial for enhancing security, ensuring compliance, conserving resources, and maintaining user accountability. Integrating banner messages during SSH login attempts further contributes to a robust and secure Linux environment. Following the outlined steps, administrators can establish effective controls, limiting user access to specific time periods and reinforcing the overall security posture of the system.
Share your thoughts in the comments
Please Login to comment...