Find Real IP behind CloudFlare with CloudSnare
Last Updated :
02 Feb, 2024
Cloudflare is a company that provides content delivery network (CDN) services and cybersecurity protection for websites and applications. Cloudflare is one of the most popular CDN providers that offers a complete package of WAF i.e. Web Application Firewall and DDOS Protection (Distributed Denial of Service) for websites. In this article, we will see detailed steps to Find Real IP behind CloudFlare with CloudSnare.
Features of CloudFlare:
- Content Delivery Network (CDN): Cloudflare operates a global network of servers that caches and delivers website content from the nearest location to the end-user, reducing latency and speeding up page load times.
- Distributed Denial of Service (DDoS) Protection: Cloudflare provides robust DDoS protection, mitigating malicious traffic and ensuring that websites remain accessible during cyberattacks.
- Web Application Firewall (WAF): Cloudflare’s WAF protects websites from common web application vulnerabilities and exploits by filtering and monitoring HTTP traffic between a web application and the internet.
- SSL/TLS Encryption: Cloudflare offers free SSL/TLS certificates to secure the communication between users and websites, encrypting data in transit and providing a secure browsing experience.
- Always Online: In case your origin server goes down, Cloudflare’s Always Online feature serves a cached version of the website, ensuring that users can still access content even if the origin is temporarily unavailable.
What is CloudSnare Script ?
CloudSnare is a script or piece of code that can be inserted into a website to detect if the site is behind Cloudflare. It works by attempting to access special Cloudflare-specific resources or by detecting headers and properties that are unique to Cloudflare’s infrastructure. If the script successfully accesses these Cloudflare exclusive indicators, it indicates the website has Cloudflare enabled and active. Website owners often block or restrict access to the CloudSnare script to hide the fact they are using Cloudflare. But attackers use it to reveal if Cloudflare is present to plan further targeted probes for vulnerabilities or misconfigurations to try and bypass Cloudflare protections.
How to Configure Censys.io?
Before, finding Real IP behind CloudFlare with CloudSnare, we need to configure Censys.io. So follow the below specified steps to Configure Censys.io.
Step 1: Create the Account on Censys.io
Go to censys.io and sign up for a free account. You will need to provide your email address and create a password to register your account. Verify your account through the confirmation email received in your mailbox. Click on the verification link in the email to confirm and activate your Censys account. Once verified and activated, you can now log into your Censys account using the credentials you signed up with.

Creating Account on Censys.io
Step 2: Generating API and Secret Key.
Go to your Censys account profile by clicking on “My Account” in the top right corner of the page while logged into your Censys account. This will open up your account settings.

Navigating to My Account Section
Under the “API” tab/section, you will find your unique API ID and secret key. Copy or note down the API ID and secret value string displayed, as you will need to use these credentials for authenticating in order to access Censys programmatically through its API in your code. Make sure you store the API credentials securely for your account. Do not share them publicly. These keys act as your username and password to authenticate with the API.

API ID and Secret ID
How to Find Real IP behind CloudFlare with CloudSnare Python Script?
As in the above section, we have configured Censys.io. Now, we can follow the below steps to Find Real IP behind CloudFlare with CloudSnare Python Script.
Step 1: Download CloudSnare Script
Download the CloudSnare script, which is a Python-based script, from its GitHub repository to your local desktop computer. Open the downloaded Python script file in a code editor of your choice.
Python3
import censys.certificates
import censys.ipv4
from sys import argv
UID = "**CHANGE**"
SECRET = "**CHANGE**"
def is_cloudflare(dn):
if "cloudflaressl.com" in dn or "cloudflare.com" in dn:
return True
return False
def find_certificates(target):
print("Certificates:")
certificates = censys.certificates.CensysCertificates(UID, SECRET)
fingerprints = []
fields = ["parsed.names", "parsed.extensions.subject_alt_name.dns_names",
"parsed.fingerprint_sha256", "parsed.subject_dn"]
for cert in certificates.search("%s and tags: trusted" % target, fields=fields):
if not is_cloudflare(cert["parsed.subject_dn"]) and target in cert["parsed.names"]:
fingerprints.append(cert["parsed.fingerprint_sha256"])
print("\tHost: %s\n\tFingerprint: %s" % (' '.join(cert["parsed.names"]), cert["parsed.fingerprint_sha256"]))
return fingerprints
def find_hosts(target):
print("Hosts: %s" % target)
hosts = censys.ipv4.CensysIPv4(UID, SECRET)
fields = ["ip"]
for host in hosts.search(target):
print("\tFound host: %s" % (host["ip"]))
def main():
if len(argv) != 2:
print("Usage: %s <host>" % argv[0])
else:
target = argv[1]
fingerprints = find_certificates(target)
for fp in fingerprints:
find_hosts(fp)
if __name__=="__main__":
main()
|
Update the script by replacing the default API ID and secret key values with your actual Censys API ID and secret token that you copied in the previous step. Save your changes after inserting your credentials into the script file so they remain populated for when you run the script.

Pasting API and Secret Key from Censys.io
Step 2: Install the Censys Python Module
Install the Censys Python module on your Linux system to allow the CloudSnare script to interact with the Censys API by entering the following command in your terminal:
pip install censys

Installing the Censys Python Module
Step 3: Run the CloudSnare Script
Run the CloudSnare.py script file that you downloaded and updated with your credentials. Navigate to the directory path location you have saved the CloudSnare.py file on your desktop using the command line. Execute the script by running the following command:
python CloudSnare.py geeksforgeeks.org
In the results, we can see that, we have got the IP Address which is behind the Cloudflare.
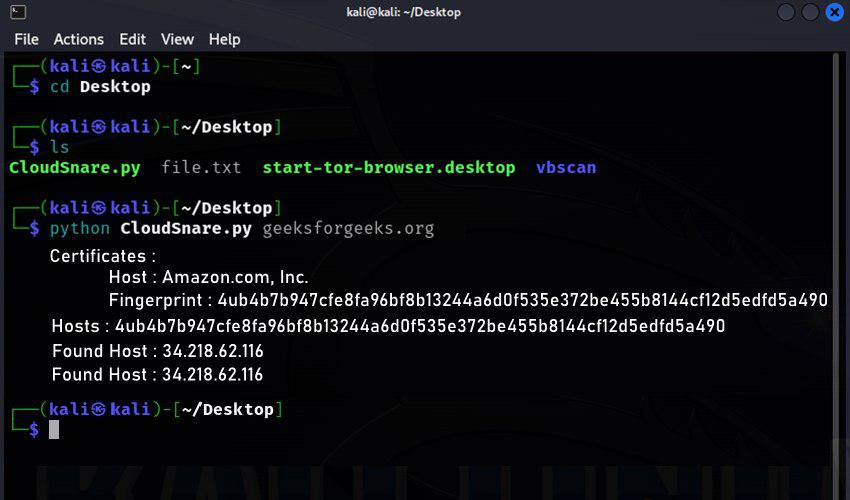
Result of the CloudSnare.py Script
Conclusion
In conclusion, Cloudflare is a popular service that provides CDN, security, and performance benefits for websites. Many site owners enable it. Censys allows searching details on globally scanned servers and websites, including real IP addresses hidden behind Cloudflare. CloudSnare is a script that checks if Cloudflare is functioning on websites by detecting unique identifiers. By using Censys API credentials in CloudSnare, you can programmatically check if Cloudflare is proxying and protecting a website. Attackers use these tools to bypass protections, while website owners try restricting them to hide their stack. In summary, CloudSnare combined with the Censys search engine can reveal when the Cloudflare network is being utilized by examining for proprietary tells in website traffic and responses.
Share your thoughts in the comments
Please Login to comment...