Basics of Cryptographic Algorithms
Last Updated :
21 Mar, 2024
Cryptography is a process of hiding transmitted information by the sender such that it may be read only by the intended recipient. In this article, we will learn more about various cryptographic algorithms. Cryptography is widely used in various fields such as end-to-end messaging, banking and finance, secure web communication, and access control.
What are Cryptographic Algorithms?
A cryptographic algorithm is a set of steps that can be used to convert plain text into cipher text. A cryptographic algorithm is also known as an encryption algorithm.
A cryptographic algorithm uses an encryption key to hide the information and convert it into an unreadable format. Similarly, a decryption key can be used to convert it back into plain-readable text.

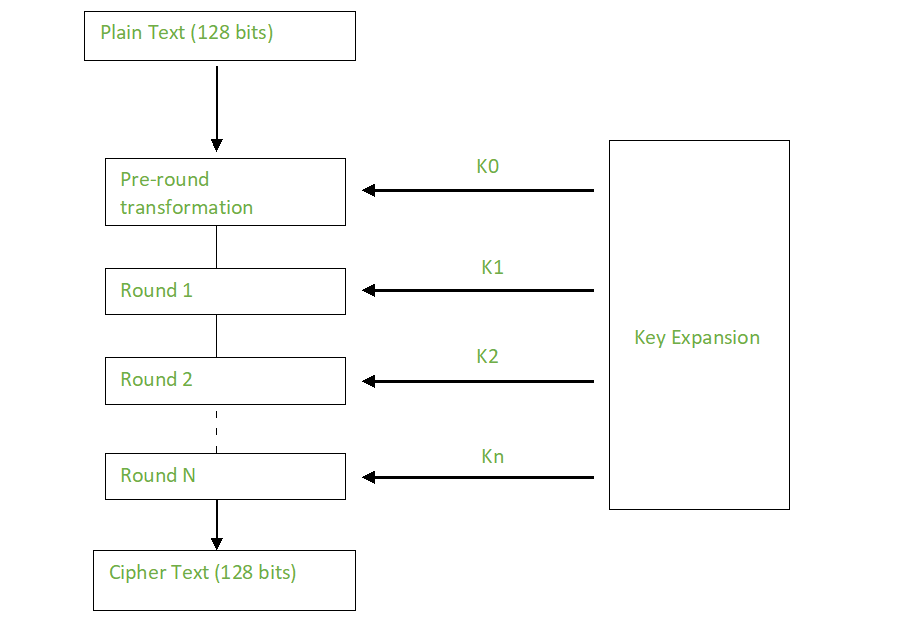
Process of Cryptography
Types of Cryptographic Algorithms
To protect sensitive data and conversations, cryptography uses complex algorithms. These mathematical formulas enable the encryption, decryption, signature, and verification processes that protect secret data during transmission and storage.
There are various types of cryptographic algorithms but in this article we will be discussing the 4 major types of cryptographic algorithms.
1. Advanced Encryption Standard (AES)
AES (Advanced Encryption Standard) is a popular encryption algorithm which uses the same key for encryption and decryption It is a symmetric block cipher algorithm with block size of 128 bits, 192 bits or 256 bits. AES algorithm is widely regarded as the replacement of DES (Data encryption standard) algorithm, which we will learn more about later in this article.
There are many types of AES depending on the rounds:
- AES-128 uses 10 rounds
- AES-192 uses 12 rounds
- AES-256 uses 14 rounds
The more rounds there are, the safer the encryption. This is why AES-256 is considered the safest encryption.
Characteristics of AES Algorithm
- Many key sizes: Three key sizes available: 128, 192, and 256 bits
- Security: Strong security measures to protect against threats
- Versatile: It is versatile because it can be used for both hardware and software
- Wide applications: Widely adopted in various applications, including:Google Cloud, Facebook and Password managers.
2. Data Encryption Standard (DES)
DES is an older encryption algorithm that is used to convert 64-bit plaintext data into 48-bit encrypted ciphertext. It uses symmetric keys (which means same key for encryption and decryption). It is kind of old by today’s standard but can be used as a basic building block for learning newer encryption algorithms.
Characteristics of DES
- Same symmetric key: DES uses symmetric-key algorithm and therefore, encryption and decryption can be done by single key using same algorithm.
- Easier Implementation: DES was designed for hardwares rather than software and shows efficiency and fast implementation in hardwares.
- Cipher technique: Transposition and substitution cipher is used: This algorithm uses both transposition cipher and substitution cipher technique.
- Building block: DES technique acts as a building block for other cryptographic algorithms.
3. RSA Algorithm (Rivest, Shamir, Adleman Algorithm)
So, RSA is an basic asymmetric cryptographic algorithm which uses two different keys for encryption. The RSA algorithm works on a block cipher concept that converts plain text into cipher text and vice versa.
RSA algorithm is an asymmetric cryptography algorithm. Asymmetric actually means that it works on two different keys i.e. Public Key and Private Key. As the name describes that the Public Key is given to everyone and the Private key is kept private.
Characteristics of RSA Algorithm
- Security: Many consider the RSA method to be highly secure and widely used for transmitting data
- Fast Speed: The RSA approach is known for its speed. Can be implemented swiftly when cryptography needs arise.
- Different keys: In the RSA technique two separate keys are utilized for encrypting and decrypting data. The public key is used to encrypt the information while the private key is employed for decryption.
- Key exchange: With the RSA method secure exchange can be achieved, enabling two parties to swap a key without transmitting it over the network.

4. Secure Hash Algorithm (SHA)
SHA is used to generate unique fixed-length digital fingerprints of input data known as hashes. SHA variations such as SHA-2 and SHA-3 are commonly used to ensure data integrity and authenticity. The tiniest change in input data drastically modifies the hash output, indicating a loss of integrity. Hashing is the process of storing key value pairs with the help of a hash function into a hash table.
Characteristics of Secure Hash Algorithm (SHA)
- Security: The SHA 256 is highly recognized for its robust security features, among hashing algorithms. It effectively prevents collision attacks ensuring that different inputs do not produce the hash value. Websites prioritize user privacy by storing passwords in a format.
- One-way hashing: Using SHA algorithms for one way hashing enables the storage of information like passwords. Data hashing into a fixed length output simplifies indexing and comparisons. Even a minor change in the message results, in a hash when using SHA algorithms facilitating the identification of corrupted data.
- Avalanche effect: A small change in the input value, even a single bit, completely changes the resultant hash value. This is called the
- Variable input length and fixed output length: SHA algorithm consits of a variable input length (meaning the length of input is dynamic) and a fixed output length.
Conclusion
In conclusion, there are 4 major types of cryptographic algorithms namely AES, DES, RSA & SHA. Cryptographic algorithms are use to implement cryptography in its real world application while Cryptography is the study of these algorithms. Cryptography is very important for secure data transmission and preventing various data leaks.
Frequently Asked Questions on Basics of Cryptographic Algorithms – FAQs
What is the most secure cryptographic algorithm?
AES 256-bit encryption is the strongest and most robust encryption standard that is commercially available today. It is mostly impossible to crack and can provide a secure solution to your system.
Is hashing an encryption algorithm?
Yes, hashing can be regarded as an encryption algorithm since it supports one-way encryption process in which a hash value cannot be reverse engineered.
Is cryptography and encryption the same?
Encryption is a part of cryptography, while cryptography is the study of learning how to implement encryption and decryption to a plain and ciphertext respectively.
Share your thoughts in the comments
Please Login to comment...