Scanning and identifying live hosts on a network is one of the crucial activities for an ethical hacker or expert. One of the powerful tools in Kali Linux, a popular penetration testing distribution, is Nmap which has a variety of host scanning techniques. To gather valuable information about targets, detect vulnerabilities, and ultimately secure systems and networks, one needs these scanning commands. Mastering these commands would not only provide beginners with basic knowledge for doing their network reconnaissance effectively but would also help professionals conduct better security assessments on networks.
What is Host Scanning?
In Simple words, it is like finding out which houses have people living in them on your street. Essentially, when you want to scan a network, you are knocking at the doors of different IP addresses and seeing if there’s an active computer or device behind that responds. The purpose of host scanning is to generate a map of all alive hosts on the network before any additional analysis is performed. It will help you know which devices are connected and what IP addresses need concentrating on.
Since host scanning provides valuable information about actual active and reachable targets, it is typically among the first stages of network reconnaissance and penetration testing. It’s one of the basic tools used by cybersecurity professionals and ethical hackers to evaluate network security.
15 Most Useful Host Scanning Commands – Kali Linux
1. Active Reconnaissance with Nmap Command
The Following command is used to perform a ping scan on the specified target to determine which hosts are online or active. So when you run this command, Nmap will send ICMP Echo (ping) requests to all IP addresses in the specified target range. The hosts that respond to these ping requests are considered alive or active, and their IP addresses will be displayed in the output.
Command :
sudo nmap -sn -PE <target>
Output :

2. Find Alive Hosts with Netdiscover
The following command is used to scan for active devices or hosts on the local network using ARP requests. When you run this command, netdiscover will continuously send ARP requests to all IP addresses within the specified target range. Any active device on the network that receives the ARP request will respond with its MAC address and IP address.
Command :
sudo netdiscover -r <target>
Output :

3. Find Top 10 Open Ports with Nmap (Fast Scan)
The Following nmap command is used to perform a quick scan on the specified target to identify the top 10 most commonly used open ports. When you run this command, Nmap will scan the specified target(s) and check the 10 most commonly used ports (such as 21, 22, 23, 25, 80, 110, 143, 443, 3306, and 3389) to see if they are open or listening for incoming connections. The output will display a list of the open ports found on the target(s), along with some basic information about the associated services or applications running on those ports.
Command :
nmap <target> –top-ports 10 –open
Output :

4. Scanning with Unicornscan
The Following command is a combination of two separate commands using the “unicornscan”. At, first It will Scan the specified target IP range for open TCP ports at a rate of 3000 packets per second, with verbose output, retrying up to 3 times for each port. After the TCP scan finishes, it will scan the same target IP range for open UDP ports, also at 3000 packets per second, with verbose output and up to 3 retries.
Command :
sudo us -mT -Iv <target>:a -r 3000 -R 3 && us -mU -Iv <target>:a -r 3000 -R 3
Output :

5. TCP Syn Scan with Nmap
The Following nmap command is used to perform a stealthy TCP scan and service/version detection on the specified target, with increased speed. When you run this command, Nmap will perform a SYN scan on the specified target(s) to find open TCP ports. For each open port, it will then try to determine the service or application running on that port, along with its version information.
Command :
sudo nmap -sS -sV -T4 <target>
Output :

6. Scanning with HPING3
The following hping3 command will –scan known <target> is used to perform a basic TCP scan on the specified target using the hping3 utility in Kali Linux. When you run this command, hping3 will send TCP connection requests to all well-known ports (ports 1-1024) on the specified target. The output will display the open ports found on the target system.
Command :
hping3 –scan known <target>
Output :

7. Port Scanning with Netcat
The following nc command is used to perform a TCP port scan on the specified target using the nc (netcat) tool in Kali Linux. When you run this command, nc will attempt to connect to each TCP port in the range 1-1024 on the specified target. If a port is open and accepting connections, nc will report it as “open”. If the port is closed or filtered, it will report it as “closed”.
Command :
nc -nvz <target> 1-1024
Output :

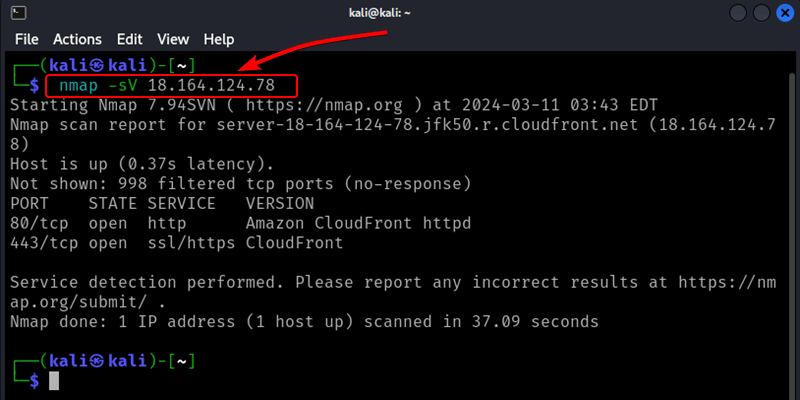
8. Version Scanning with Nmap
The following nmap command is used to perform service and version detection scanning on the specified target using the Nmap tool in Kali Linux. When you run this command, Nmap will first perform a TCP connect scan on the specified target(s) to find open ports. For each open port, it will then try to determine the service or application running on that port and its associated version information.
Command :
nmap -sV <target>
Output :
9. Firewall Bypass
The following nmap command is used to perform a fragmented packet scan on the specified target using Nmap in Kali Linux. When you run this command, Nmap will split its scanning packets into smaller fragments of 512 bytes or less and send them to the target system. This can sometimes allow the scan to bypass certain firewall rules or intrusion detection systems that may be configured to block or detect larger, unfragmented packets.
Command :
sudo nmap -f –mtu=512 <target>
Output :

10. Scanning with Masscan
The following command is used to perform a fast TCP port scan on the specified network or IP range, targeting port 80 (HTTP), and capturing banner information while spoofing the source IP address. When you run this command, masscan will rapidly scan the specified network range, sending TCP connection requests to port 80 on each IP address. If port 80 is open on a target system, masscan will capture and display any banner information returned by the service running on that port.
Command :
masscan <network> -p80 –banners –source-ip <target>
Output :

11. Specific Port Scanning
The following command is used to perform a TCP port scan on the specified target system, specifically targeting port 80 using the Nmap tool in Kali Linux. When you run this command, Nmap will send TCP connection requests to port 80 on the specified target(s). If port 80 is open and accepting connections, it will be reported as “open” in the scan results. If port 80 is closed or filtered, it will be reported as “closed” or “filtered” respectively.
Command :
nmap -p 80 <target>
Output :

12. Open Ports Scanning
The following command is used to perform a TCP connect scan on the target IP address and only show the ports that are open or listening for incoming connections. When you run this command, Nmap will scan all 65,535 TCP ports on the target IP address using a TCP connect scan, which is the most reliable way to determine if a port is open or closed.
Command :
nmap --open <target>
Output :

13. Active Remote Hosts Scanning
The following command is used to perform a ping scan on the specified network range using the Nmap tool in Kali Linux. When you run this command, Nmap will send ICMP (ping) requests to all IP addresses within the network range. It will then report back a list of IP addresses that responded to the ping requests, indicating that those hosts or devices are online and active on the network.
Command :
nmap -sn <target/port>
Output :

14. OS fingerprinting
The following command is used to perform remote operating system detection on the target system with the IP address using the Nmap tool in Kali Linux. When you run this command, Nmap will send a series of specially crafted packets to the target IP address and analyze the responses it receives. Based on these responses, Nmap will attempt to fingerprint the target system and determine the operating system (OS) it is running.
Command :
nmap -O <target>
Output :

The following command is used to perform an aggressive scan on the target system with the IP address using the Nmap tool in Kali Linux. When you run this command, Nmap will perform a comprehensive scan on the target IP address, combining various scanning techniques to gather as much information as possible about the target system. Specifically, the -A option enables the following :
- 1. OS Detection: Nmap will attempt to detect the operating system running on the target system.
- 2. Version Detection: Nmap will probe open ports to determine the service/version information of the applications running on those ports.
- 3. Script Scanning: Nmap will run a collection of default scripts designed to gather additional information about the target system, such as detecting vulnerabilities or collecting system data.
- 4. Traceroute: Nmap will perform a traceroute to determine the network path to the target system.
Command :
nmap -A <target>
Output :

Conclusion
Host scanning is an essential technique used by cybersecurity professionals and ethical hackers to identify live systems or devices on a network. Kali Linux provides various powerful scanning tools, with Nmap being the most versatile and widely used. With practice and understanding of these scanning commands, you can effectively map out network environments, identify potential vulnerabilities, and improve your overall cybersecurity skills.
Share your thoughts in the comments
Please Login to comment...