wireshark sniffing and spoofing
Last Updated :
29 Jan, 2024
Wireshark is an open-source packet analyzer that enables real-time data inspection. It enables network sniffing, which analyzes traffic for device communication insights. The ethical and legal implications of network sniffing are discussed, emphasizing responsible usage. Spoofing, a manipulation of network data, can compromise network security through techniques like ARP, DNS, and IP spoofing.
Prerequisites
- Wireshark is installed on your computer.
- Access to the network where you suspect ARP spoofing.
- Linux Machine
What is Sniffing?
The process of intercepting and capturing network traffic is referred to as sniffing. A network sniffer, packet sniffer, or network analyzer, is a tool or piece of software that captures and analyzes data packets as they transit over a network. Sniffing is frequently used for valid reasons such as network troubleshooting, monitoring, and analysis. Sniffers can be used by network administrators to diagnose network problems, optimize performance, or investigate security vulnerabilities. It can, however, be abused for nefarious reasons.
How to Perform Sniffing in Wireshark?
In this section, we will see a detailed step-by-step process to perform Sniffing in Wireshark Tool.
Step 1: Open Wireshark Window
Open your Wireshark tool in a new window or a Linux virtual machine. and begin network capture. Assume we are capturing wireless fidelity (Wi-Fi Traffic).
Opening Wireshark Tool
Step 2: Start the Wireless Fidelity
Open Wireshark, select your Wi-Fi interface and start capturing packets. Engage in network activities, stop the capture, and analyze the captured packets for network insights.
.png)
Starting Wireless Fidelity
Step 3: Filter the HTTP Packets
Wireshark has recorded some packets, but we’re looking for HTTP packets in particular. So we use some command in the display filter bar to find all of the captured HTTP packets—the green bar in the image below shows where we applied the filter.
http
-(1).png)
Filtering HTTP Packets
Step 4: Filter other Vulnerable Packets
Apply Wireshark filters to focus on specific vulnerable packets: filter by Telnet, TCP, UDP, HTTP, SMTP, NNTP, POP, or FTP protocols to identify and analyze potential security issues in the captured network traffic.
tcp.port == 80 || udp.port == 80
.png)
Filtering TCP and UDP Packets
In the below output screenshot, you can see that we have filtered FTP packets.
ftp
.png)
Filtering FTP Packets
What is Spoofing?
Spoofing is fooling or tricking a system, device, or network by using false information. This could include assuming a false name, IP address, or other identifying characteristics to obtain illegal access, change data, or launch attacks. Spoofing is frequently related to cyber attacks in which the attacker attempts to conceal their identity or obtain unauthorized access to a system or network.
Types of Spoofing:
- IP spoofing: IP spoofing is the practice of forging a packet’s originating IP address to make it appear to come from a trusted source.
- MAC spoofing: MAC spoofing is the practice of changing a network interface’s Media Access Control (MAC) address to imitate another device on the network.
- Email spoofing: Email spoofing is the practice of forging the sender’s email address to make an email appear to come from a reputable source.
- DNS spoofing: DNS spoofing refers to the manipulation of the Domain Name System (DNS) to redirect a user to a fake website.
How to Perform Spoofing in Wireshark?
In this section, we will perform the detailed step-by-step process to perform Spoofing in Wireshark Tool.
Step 1: Capture ARP Traffic
Open Wireshark, and choose the network interface. Start capturing by clicking the interface and selecting “Start.”
.png)
Capturing Wireless Fidelity
Step 2: Filter for ARP Traffic
Apply the ARP filter in the display filter bar to focus on ARP packets.
arp
.png)
Filtering ARP Packets
Step 3: Analyze ARP Requests and Replies:
Observe normal ARP traffic—devices asking for and receiving MAC addresses.
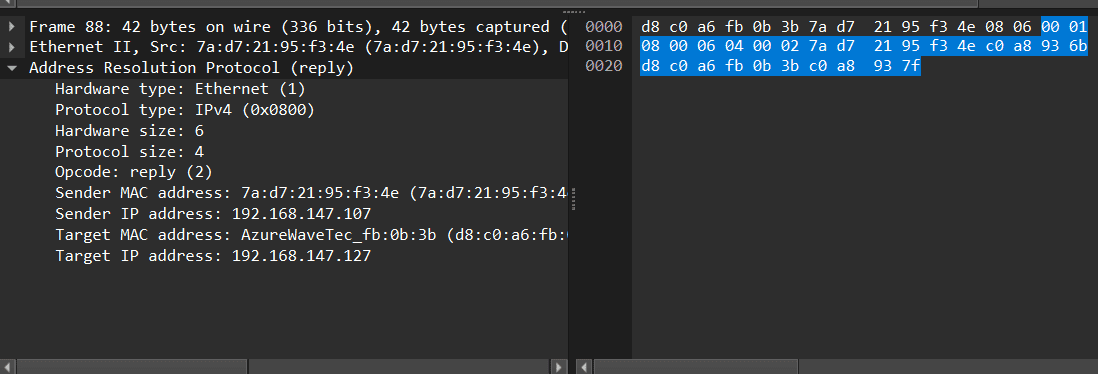
Analyze ARP Packet requests
- Identify Inconsistencies: Look for anomalies like multiple devices responding to one ARP request or multiple MACs for one IP.
- Check Gratuitous ARP: Detect gratuitous ARP packets—devices announcing MAC for an IP without prompting.
- Compare with Network Topology: Understand legitimate devices and MAC addresses; compare with observed ARP responses.
Frequently Asked Questions on Wireshark Sniffing and Spoofing – FAQs
What is Wireshark sniffing, and how does it work?
Wireshark sniffing involves capturing and analyzing network traffic. It works by enabling the network interface’s promiscuous mode to capture all packets in the network segment.
What is IP spoofing, and how can Wireshark detect it?
IP spoofing involves forging source IP addresses in network packets. Wireshark helps detect it by analyzing packet headers, identifying inconsistencies like unexpected source IP addresses or unusual traffic patterns.
How does Wireshark detect ARP spoofing?
Wireshark detects ARP spoofing by analyzing Address Resolution Protocol (ARP) packets. In a spoofing attack, abnormal ARP responses may be observed, such as multiple devices claiming the same IP or MAC address, which Wireshark helps identify.
Conclusion
In conclusion, Wireshark is an open-source network protocol analyzer that enables real-time data inspection on computer networks. Sniffing, a process of intercepting and capturing network traffic, is used for troubleshooting, monitoring, and analysis. It can diagnose problems, optimize performance, and investigate security vulnerabilities. However, it can also be abused for nefarious purposes, such as spoofing, which involves using false information to gain access, change data, or launch attacks.
Share your thoughts in the comments
Please Login to comment...