Secure Software Development Life Cycle (SSDLC) ensures that computer programs are built with security in mind right from the beginning. It involves planning, designing, coding, testing, deploying, and maintaining software while consistently addressing security concerns at each step. SSDLC is crucial to identify and fix security issues early, reducing the risk of cyber threats. By integrating security measures throughout the development process, SSDLC aims to create safer and more trustworthy software applications. It is an essential practice in the ever-changing landscape of cybersecurity.
.jpg)
Secure Software Development Life Cycle
What is Secure Software Development Life Cycle (SSDLC)?
The entire development process is mapped out by the software development life cycle (SDLC) framework. Planning, design, development, release, maintenance, updates, and retirement or replacement of the application when necessary are all included.
Secure Software Development Life Cycle
This process is expanded upon by the secure SDLC (SSDLC), which integrates security throughout the entire lifecycle. An SSDLC is frequently used by teams making the switch to DevSecOps. The procedure entails safeguarding the development environment and implementing security best practices alongside functional aspects of development.
Importance of Secure SDLC (Secure Software Development Life Cycle)
Making sure software is secure is important, and that’s where Secure Software Development Life Cycle (SSDLC) comes in. In the past, people didn’t pay enough attention to security when creating software, which led to problems and potential breaches. With SSDLC, security is thought about from the very beginning to the end of making the software. This is a proactive way of dealing with security risks, finding and fixing them early so that the chances of cyber-attacks are minimized. By including security right from the start, companies can make their software more reliable, follow rules better, and gain the trust of the people using their software. So, Secure SDLC is a must for creating strong and secure software in today’s world of online threats.
Evolution of Secure SDLC(Secure Software Development Life Cycle)
The development of the Secure Software Development Life Cycle (SDLC) has come a long way, evolving from a time when people didn’t give much attention to security in software creation. Initially, the main focus was on making sure the software worked well and was fast, with security often taking a backseat. As cyber threats grew in complexity, the realization dawned that addressing security late in the game wasn’t effective. Over time, the evolution of SDLC shifted towards making security a fundamental part right from the beginning of the development cycle. This change was driven by the understanding that dealing with security issues later on was not a good strategy. The evolution also involved figuring out best practices and principles, emphasizing things like secure coding, assessing risks, and continuously keeping an eye on security.
The development of Secure SDLC was also influenced by rules and regulations, along with a greater awareness of the serious consequences of security breaches. Today, it’s a comprehensive framework that covers all aspects of development, ensuring security is considered at every step.
In simple terms, the evolution of Secure SDLC shows how people have learned to think about security right from the start, moving from reacting to problems to being proactive and making sure software is robust and secure.
Key Principles of Secure SDLC(Secure Software Development Life Cycle)
The key principles of Secure Software Development Life Cycle (SDLC) lay out the fundamental ideas guiding the process of creating secure software. These principles help developers and teams understand how to approach security in each stage of development.

Key Principles of Secure SDLC
- Security by Design: This principle highlights the need to think about security right from the start of creating software. It means including security requirements in the initial planning and design stages of development.
- Continuous Monitoring: Continuous monitoring is an ongoing process of regularly checking and ensuring the security of the software at every step of its development. It’s not a one-time thing but a continuous effort to find and fix security issues throughout the entire development process.
- Risk Assessment: This principle involves evaluating and understanding potential security risks early in the development process. It includes identifying vulnerabilities and deciding which risks need the most attention and quick action to reduce potential threats.
- Education and Training: Education and training are essential to make sure everyone involved in creating the software, especially developers, knows about security issues. It emphasizes providing the necessary training so that individuals have the skills to handle security concerns effectively.
- Collaboration: Collaboration is a crucial principle that stresses the importance of teamwork. It involves encouraging collaboration between different teams, like developers, operations, and security teams. This ensures that everyone is working together, sharing knowledge, and coordinating efforts to achieve common security goals during the software development process.
Phases of Secure SDLC(Secure Software Development Life Cycle)
Phases of Secure Software Development Life Cycle (SDLC) refer to the different stages involved in building secure software. These phases guide the step-by-step process from the initial planning to the ongoing maintenance of the software.

Phases of Secure SDLCPhases of Secure SDLC
Phases of Secure SDLC:
- Planning: In the planning stage, the main focus is on figuring out the security requirements for the software. This includes identifying possible risks and creating a plan for how to make the software secure from the beginning.
- Design: During the design phase, the plan for security is put into action. This involves making decisions about how to build security features into the software. The goal is to ensure that the design can handle potential security problems.
- Implementation: In the implementation phase, developers start building the software using secure coding practices. This means writing code in a way that reduces the chances of security problems. Code reviews are done to catch and fix any security issues.
- Testing: Testing is all about checking how secure the software is. Different tests are done, like trying to break into the software to find vulnerabilities, scanning the code for potential problems, and making sure the software can handle different security threats.
- Deployment: Deployment is when the software is released. Here, the focus is on making sure the release process is secure, taking precautions to avoid any security issues during this stage.
- Maintenance: Maintenance is an ongoing process where the software is continuously looked after. This involves keeping an eye on security and regularly updating the software to deal with new threats, making sure it stays secure over time.
Examples of a Secure SDLC (Secure Software Development Life Cycle):
The following are a few instances of well-known frameworks for creating safe software development lifecycles:
The National Institute of Standards and Technology (NIST), which is also responsible for maintaining the National Vulnerability Database (NVD), which keeps track of publicly known software vulnerabilities, developed the secure software development framework (SSDF).
A secure SDLC can be realized with the aid of the software development techniques defined by the SSDF. Documents outlining and recommending standards, principles, and software development processes are included in the framework. Prominent behaviors consist of:
- Giving edevelopers instruction in secure code to guarantee security right away
- Security issues can be identified as near to the point of remedy as feasible by automating and integrating security tests.
- Security libraries and open source components used in projects
The safe software development framework developed by NIST aims to lessen the amount of vulnerabilities in software that is released into production environments and to lessen the potential for vulnerabilities that go ignored and undiscovered to be exploited. In addition to addressing the underlying causes of vulnerabilities, the architecture can stop them from recurring in the future.
MS Security Development Lifecycle (MS SDL):
Microsoft introduced MS SDL to provide reliable security considerations to support the contemporary development workflow. A selection of procedures selected specifically to support security assurance and compliance needs are included in the SDL. The SDL can help developers cut down on the quantity and seriousness of vulnerabilities in their codebase, as well as the expenses and delays associated with late-stage remediation.
OWASP Comprehensive, Lightweight Application Security Process (CLASP):
Best practices for security are implemented by the rule-based components that make up CLASP. It can assist developers in implementing security in a systematic and repeatable manner and securing apps early in the development cycle.
In order to create CLASP, real-world development teams were examined, their development lifecycles dissected, and the best way to include security procedures into their routines was determined. In addition to discussing how to improve currently in place processes, CLASP assists teams in addressing particular vulnerabilities and coding flaws that may be used to cause significant security breaches.
SDLC Process vs SSDLC Process:
.webp)
SDLC Process vs SSDLC Process
| Primarily on delivering functional software. |
Emphasizes security considerations throughout the process. |
| Meeting business requirements and functionality. |
Integrating security measures to protect against vulnerabilities. |
| Typically includes phases like planning, analysis, design, implementation, testing, deployment, and maintenance. |
Incorporates security-related phases, such as threat modeling, secure coding, and continuous monitoring. |
| Security is addressed mainly during the testing phase. |
Security is considered at every stage, from design to deployment. |
| Security testing is often a separate phase. |
Security testing is integrated into each phase of development. |
| Documentation focuses on functionality and features. |
Comprehensive documentation on security measures, threat models, and risk assessments. |
| Emphasizes timely delivery of software features. |
May involve slightly longer development cycles due to added security considerations. |
| Generally more adaptable to changes in business requirements. |
May require more effort to incorporate changes due to the stringent security focus. |
The Benefits of SSDLC(Secure Software Development Life Cycle)
- SSDLC helps catch security issues early in the software development process, reducing the chances of problems surfacing after deployment.
- By making security a priority, SSDLC builds trust among users and stakeholders, creating a reliable reputation for the software.
- Adhering to SSDLC practices ensures compliance with regulations, meeting industry-specific security standards.
- Identifying and fixing security issues during development is more cost-effective than dealing with breaches post-deployment.
- Secure software development enhances the organization’s reputation, fostering user confidence and loyalty.
- Users feel more secure with products developed using SSDLC, resulting in higher satisfaction and trust.
- Proactive security measures minimize downtime by preventing and addressing security incidents promptly.
- SSDLC safeguards sensitive data, providing protection against unauthorized access and potential breaches.
- Securely developed software has a longer life cycle, adapting to evolving security threats and technology changes.
- Organizations gain a competitive edge by prioritizing security through SSDLC, attracting users who value the safety of their data and transactions.
Key Security Challenges in Secure Software Development Life Cycle (SDLC):
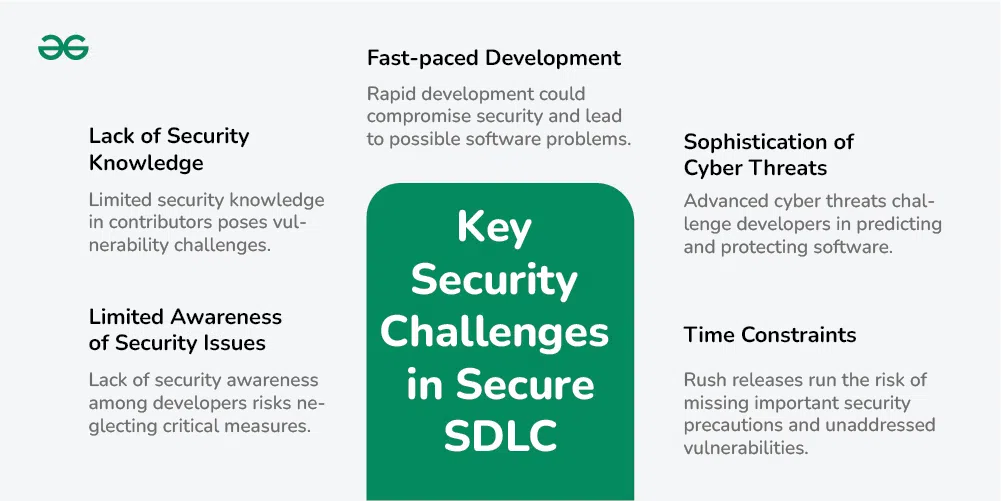
When it comes to making software, there are some big challenges with keeping it secure.
Key Security Challenges in Secure Software Development Life Cycle (SDLC)
- Lack of Security Knowledge: One of the main problems is that not everyone involved in making software knows enough about keeping it secure. This can lead to mistakes and weaknesses in the software.
- Fast-paced Development: Developers often have to work really quickly to meet deadlines. Because of this rush, they might not have enough time to focus on making the software secure, which can be a problem.
- Sophistication of Cyber Threats: Cyber threats are getting more advanced and tricky. This makes it harder for developers to predict and protect the software from these evolving risks.
- Limited Awareness of Security Issues: Sometimes, the people working on the software may not know all the security issues that can come up. This lack of awareness can mean that important security measures get missed.
- Time Constraints: The pressure to finish and release software on time can lead to missing out on important security steps. Quick development might mean not catching potential problems that could be used by bad actors.
How to Ensure SSDLC(Secure Software Development Life Cycle)?
Ensuring Secure Software Development Life Cycle (SSDLC) involves practical steps to integrate security effectively into the software development process.
- Education and Training: Train the development team on security best practices to increase awareness and equip them with the skills needed to address potential security threats.
- Use Security Tools: Implement security tools such as code analyzers, vulnerability scanners, and penetration testing tools. These tools help identify and fix security issues at various stages of development.
- Regular Audits: Conduct routine security audits to assess the entire software development process. This helps in identifying any weaknesses or gaps in the security measures.
- Collaboration Between Teams: Encourage collaboration between development, operations, and security teams. This ensures that everyone is aligned on security goals and measures.
- Continuous Improvement: Regularly review and update the SSDLC process. Learn from past experiences, incorporate improvements, and stay informed about emerging security threats and best practices.
Implementing these steps collectively ensures a proactive approach to security, reducing the chances of vulnerabilities and enhancing the overall security of the developed software.
5 Secure Secure Software Development Life Cycle (SSDLC) Best Practices
Implementing Secure Software Development Life Cycle (SDLC) best practices is crucial for creating robust and secure software applications. These practices are practical guidelines that help developers and teams integrate security measures effectively throughout the development process.

5 Secure SDLC(Secure Software Development Life Cycle) Best Practices
- Threat Modeling: One important best practice is threat modeling, which involves identifying and analyzing potential threats to the software during the design phase. This proactive approach helps in understanding and addressing potential security risks early in the development process.
- Code Reviews: Conducting regular code reviews is another key practice. This involves team members reviewing each other’s code with a specific focus on security. It helps in identifying and rectifying security issues in the code before it gets integrated into the larger software system.
- Automated Testing: Implementing automated testing tools is critical for identifying vulnerabilities efficiently. These tools can include static code analyzers, dynamic application security testing (DAST), and other automated testing mechanisms. Automated testing provides a systematic and consistent way to assess the security of the code.
- Incident Response Planning: Developing and testing incident response plans is a best practice for effectively handling security incidents. This involves having a clear plan in place to respond to and recover from security breaches. Regular testing ensures that the response plan is well-understood and can be executed promptly in case of an incident.
- Secure Coding Guidelines: Establishing and enforcing secure coding guidelines is essential for promoting consistent security practices across the development team. These guidelines provide developers with specific instructions on how to write secure code, covering areas such as input validation, authentication, and encryption.
DevOps and Security Integration in Secure Software Development Life Cycle
Integrating DevOps and security is about bringing together the practices of software development and IT operations, with a focus on ensuring a secure and efficient development process. DevOps promotes collaboration and communication between development and operations teams to deliver software more quickly and reliably. Adding security into this mix means making sure security measures are part of the entire development process. It involves finding and fixing security issues early, automating security testing, and making sure that everyone shares the responsibility for security. This integration allows for ongoing security monitoring, quick identification of problems, and timely responses to potential threats. By connecting development, operations, and security, organizations can create a more seamless and secure software development cycle.
Automation in Secure Software Development Life Cycle (SSDLC)
Automation in Secure Software Development Life Cycle (SDLC) means using tools and processes to make security measures more efficient throughout the software development. This includes automating security tests, code scans, and vulnerability assessments. Automated tools can efficiently find and fix security issues, reducing the manual work needed. By bringing automation into the SDLC, organizations can consistently apply security measures at different stages, ensuring a proactive approach to managing risks. Automation also helps with continuous monitoring, allowing for real-time identification of potential security threats. Overall, adding automation to Secure SDLC not only makes security practices more efficient but also helps in timely detection and fixing of vulnerabilities, improving the overall security of the developed software.
Conclusion: Secure Software Development life cycle
In summary, making sure to follow Secure Software Development Life Cycle (SDLC) practices is crucial for creating software that’s secure and trustworthy. By including security measures right from the start and keeping them in place throughout, organizations can lower risks and gain user confidence. Things like checking for threats, reviewing code, and using automation play a part in staying ahead of security issues. When DevOps and security work together, it makes the overall security even stronger. Following these practices ensures that software can stand up to potential cyber threats, supporting its ongoing success and reliability.
FAQs on Secure Software Development Life Cycle( SDLC):
Software development is defined as the process of designing, creating, testing, and maintaining computer programs and applications. This diverse field combines creativity, engineering expertise, and problem-solving abilities to produce software that satisfies particular requirements and goals. Software developers, also known as programmers or coders, use a variety of programming languages and tools to create solutions for end-users or businesses
What is Secure Software Development Life Cycle (SSDLC)?
SSDLC is an approach to software development that integrates security practices throughout the entire software development process. It focuses on identifying and mitigating security vulnerabilities at each stage of development to create more resilient and secure software.
How does SSDLC differ from traditional SDLC?
While traditional SDLC primarily focuses on delivering functional software, SSDLC places a strong emphasis on integrating security considerations at every phase of development. It aims to proactively address security issues rather than treating security as a separate or post-development concern.
What are the key components of SSDLC?
The key components of SSDLC include threat modeling, secure coding practices, security code reviews, security testing, incident response planning, security training and awareness, continuous monitoring, and adherence to compliance standards.
Why is threat modeling important in SSDLC?
Threat modeling helps identify potential security threats and vulnerabilities early in the development process. It involves analyzing the system architecture and design to understand and address security risks effectively.
How does SSDLC address secure coding practices?
SSDLC promotes secure coding practices by training developers to write code with security in mind. It includes guidelines and best practices to prevent common vulnerabilities, such as SQL injection, cross-site scripting (XSS), and buffer overflows.
Share your thoughts in the comments
Please Login to comment...