What is Dynamic ARP Inspection?
Last Updated :
25 Oct, 2023
There are various ways in which an attacker tries to enter the network to steal confidential information, or they try to choke the network by flooding it with unwanted requests. A network security administrator works to provide security to the network. ARP spoofing is one of the ways in which attackers poison the network. Dynamic ARP inspection is used to provide security. In this article, we are going to learn about ARP spoofing and dynamic ARP inspection in detail.
ARP Spoofing Attacks
It is a type of cyberattack in which attackers send an ARP packet that spoofs the MAC address of the victim’s device on the local area network (LAN). So, the switching device sends the packet to the attacker’s device (spoofed address) instead of sending the packet to the authorized device. ARP is spoofing the type of man-in-the-middle (MITM) attacks. It can lead to various security threats like session hijacking, DoS (Denial of Service) attacks, network eavesdropping, and DNS cache poisoning.
Terminologies Definition
- ARP: The acronym ARP stands for Address Resolution Protocol, which is one of the most important protocols of the data link layer in the OSI model. It is responsible for finding the hardware address of a host from a known IP address.
- LAN: The acronym LAN stands for Local Area Network. It is a type of connection in which computers are interconnected to the network in limited areas, such as home, office, or within a building.
- DoS is a type of cyber attack in which the attacker makes the network unresponsive for the authorized user by flooding multiple irrelevant requests.
- DHCP: DHCP is the short form of Dynamic Host Configuration Protocol. The DHCP server maintains the legitimate mapping between the IP address and the MAC address on the network.
Working of the ARP Spoofing Attack
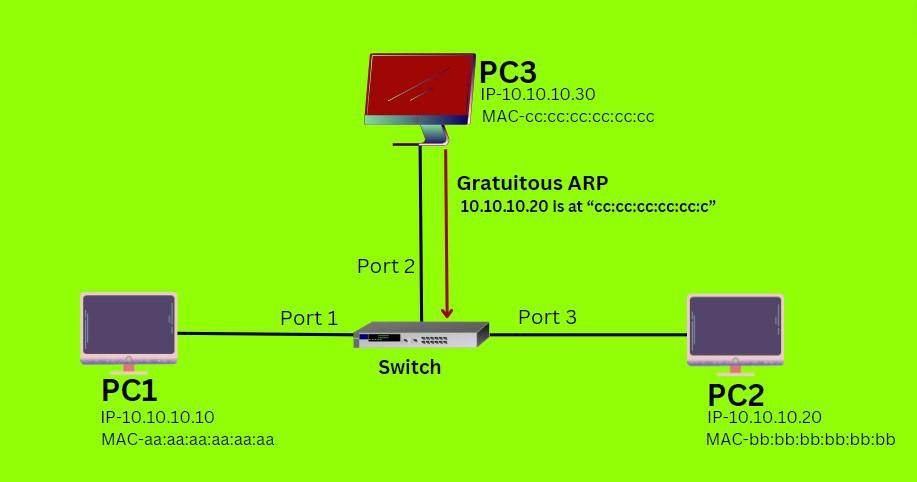
ARP spoofing
Consider a small network (as shown in the diagram) PC1(10.10.10.10) with MAC-aa:aa:aa:aa:aa:aa, PC2 (10.10.10.20) with MAC-bb:bb:bb:bb:bb:bb, PC3 (10.10.10.30) with MAC-cc:cc:cc:cc:cc is connected to the switch. PC3 belongs to the attacker, and PC2 belongs to the victim.When PC1 wants to communicate with PC2, it broadcasts an ARP request to determine the MAC address associated with the IP address of PC2. When PC2 replies to its MAC (cc:cc:cc…), the switch and PC1 maintain their ARP cache by binding the MAC address and IP address of PC3.
Initiation of Spoofing: Attackers send a malicious ARP packet to PC1 claiming that IP address 10.10.10.20 exists on the MAC. Now PC1 and Switch update their ARP cache by binding the victim (PC2) IP-10.10.10.20 and attacker (PC2) MAC-cc:cc:cc:cc:cc:cc. When PC1 sends the packet to PC3, it will be flooded to PC3 (the attacker) instead of PC2, as PC1 and the switch ARP table maintain the attacker’s MAC address with the victim’s (PC2) IP address. Now attackers have entered the network. Attackers can easily steal the data, and then send a packet to PC2 (the victim). Attackers can easily manipulate the data or launch the next attacks on the victim or network as it has the MAC addresses of both the PC1 and PC2.
Working of DIA
When a device (Host A) wants to resolve the MAC address of another device (Host B), it broadcasts an ARP request to the network, and Host B replies with the MAC along with it’s IP address. The DHCP server records the ARP request and response and maintains a table mapping IP and MAC. This DHCP server maintains the legitimate mapping between the IP address and the MAC address on the network. When DAI intercepts an ARP packet (either a response or a request), it verifies the information in the packet, i.e., the source IP address, the source MAC address, the destination IP address, and the destination MAC address, against the record on the DHCP server. If the information in the ARP packet matches the entry of the binding table in the DHCP server, then it is allowed to flood towards the destination. If DIA detects that the information in the ARP packets does not match the entry on the DHCP server, then it will take various actions, like a DROP log and rate limiting, to prevent the potential ARP spoofing attack.
Frequently Asked Questions
Q.1: What action does DAI take if an ARP packet matches the trusted binding table?
Answer:
Generally,DAI used to drop the Packet.
Q.2: Can DAI be disabled?
Answer:
DAI can be enabled and disabled but it recommended not ot disable.
Q.3: Can DAI prevent all ARP-related attacks?
Answer:
It almost prevents all ARP-related attacks but it not an absolute solution.
Q.4: Is DAI useful for only large or small networks?
Answer:
It is useful for both large and small networks.
Q.5: Drawbacks of Dynamic ARP Inspection
Answer:
DIA needs additional monitoring and configuration.
Share your thoughts in the comments
Please Login to comment...