Secure Shell and TLS
Last Updated :
05 Jan, 2021
Secure Shell :
Secure Shell is designed to be very simple and cost-effective for secure network communications. SSH Client and server applications are widely available for most operating systems.
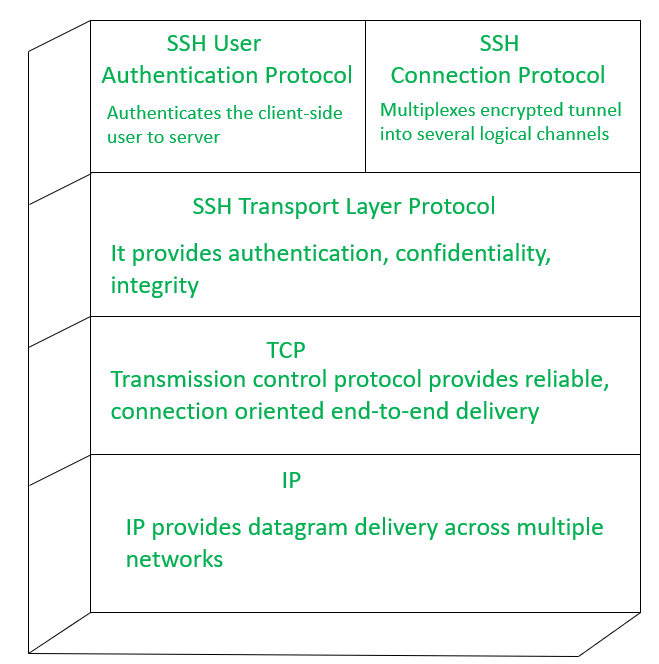
SSH runs on top of TCP and has three protocol stacks as follows.
- SSH Transport Layer Protocol –
This is mainly used for providing server authentication, data integrity, confidentiality. Compression is provided optionally.
- SSH User Authentication Protocol –
This protocol is used for authenticating users to the server.
- SSH Connection Protocol –
It multiplexes multiple logical communications channels over a single SSH connection.
Host Keys :
Authentication occurs at Transport Layer, as the server uses different asymmetric encryption techniques, the server has multiple host keys, it is compulsory that the server must exchange its key to identify the host. To happen this process the client host must also know the server host key.
The client has 2 methods of verifying the server host identity as follows.
- Client storing each hostname with name-to-key associations in his own local database, This method requires to maintain huge data.
- If each host is certified by a Certificate Authority then the client can be able to verify the host’s identity by using certification Authority.
Share your thoughts in the comments
Please Login to comment...