Pre-Requisite: Threats
With the advancement in technology, it becomes easier day by day for hackers to gain access to sensitive data, disable applications, etc. Thus, Application Security has become a major concern. One method used to implement application security in the design process is through THREAT MODELLING.
Threats can be anything that can take advantage of a vulnerability to breach security and negatively alter, erase, or harm objects or objects of interest. Threat Modelling can be done at any stage of development but if done at the beginning it will help in the early determination of threats that can be dealt with properly.
Purpose of Threat Modeling
The purpose of Threat modeling is to identify, communicate, and understand threats and mitigation to the organization’s stakeholders as early as possible. Documentation from this process provides system analysts and defenders with a complete analysis of probable attackers’ profiles, the most likely attack vectors, and the assets most desired by the attacker.
Achievement of Threat Modeling
- Defines security of application
- Identifies and investigates potential threats and vulnerabilities
- Results in finding architecture bugs earlier
Process of Threat Modeling
1. Aim
The target before approaching Threat Modeling must be clear within ourselves what we will achieve from Threat Modeling, that is our application must follow the CIA Triad.
- Confidentiality: It helps in protecting data from unauthorized access.
- Integrity: It helps in preventing restricted changes.
- Availability: It helps in performing important tasks under certain attacks.
2. Visualization
Here, we will deal with what we are going to build. We must have a document overview of the application which helps in making our process easier. Here we will build diagrams that will help us in making our process easier.
It can be done in two ways:
- Data Flow Diagram: It helps in showing how the flow of data occurs in the system.
- Process Flow Diagram: It helps in finding the process of the system that from where users interact in the system, and how the system works internally.
3. Threat Identification
Here we are going to deal with how we can identify threats or what can go wrong in the process. By analyzing the images of the previous section, you have found how threats can be identified. These methods are mentioned in threat modeling methodologies..
4. Mitigation
Here, we are going to deal with what we will do about the Threats. Here we will review the layers to identify the required vulnerabilities. Mitigation involves a continuous investigation of each vulnerability so that the most effective efforts can be designed.
5. Validation
This is the final step in the process of Threat Modeling, here we are going to deal with whether we have done a good job or not. Have all the threats been mitigated or not? We will check the changes and as threat modeling is not a one-time activity, we have to regularly watch these things.
Threat Modelling Methodologies
The development team will be able to implement application security as part of the design and development process by using threat modeling to identify threats, risks, and mitigation during the designing phase. There are various threat modeling methodologies available. We will be discussing 8 methodologies:
1. STRIDE: STRIDE is a methodology developed by Microsoft for threat modeling. It provides a mnemonic for security threats in six categories:
- Spoofing: An adversary posing as another user, component, or another system that has an identity in the system being modeled.
- Tampering: The modification of data within the system to achieve a malicious goal.
- Repudiation: The ability of an adversary to deny performing some malicious activity in absence of sufficient proof.
- Information Disclosure: The exposure of protected data to a user that is not otherwise allowed access to that data.
- Denial of Service: This occurs when an adversary uses illegitimate means to assume a trust level that he currently has with different privileges.
- Elevation of Privilege: This threat occurs when an attacker successfully breaches the administrative controls of a system and tampers its configured permissions and privileges. By this, attackers can reach from low-level systems in the network to systems of higher authority, which contain confidential information.
2. DREAD: DREAD was proposed for threat modeling but due to inconsistent ratings, it was dropped by Microsoft in 2008. It is currently used by OpenStack and many other corporations. It provides a mnemonic for risk rating security threats using five categories. The categories are:
- Damage Potential: ranks the extent of damage that would occur if a vulnerability is exploited.
- Reproducibility: ranks how easy it is to reproduce an attack
- Exploitability: Assigns a number to the effort required to launch the attack.
- Affected Users: A value characterizing how many people will be impacted if an exploit becomes widely available.
- Discoverability: Measures the likelihood of how easy it is to discover the threat.
3. Process for Attack Simulation and Threat Analysis (PASTA): It is a seven-step, risk-centric methodology. The purpose is to provide a dynamic threat identification, enumeration, and scoring process. Upon completion of the threat model, security subject matter experts develop a detailed analysis of the identified threats. Finally, appropriate security controls can be enumerated. This helps developers to develop an asset-centric mitigation strategy by analyzing the attacker-centric view of an application.
4. Trike: The focus is on using threat models as a risk management tool. Threat models are based on the requirement model. The requirements model establishes the stakeholder-defined “acceptable” level of risk assigned to each asset class. Analysis of the requirements model yields a threat model from which threats are identified and assigned risk values. The completed threat model is used to build a risk model based on assets, roles, actions, and calculated risk exposure.
5. VAST: VAST is an acronym for Visual, Agile, and Simple Threat modeling. The methodology provides actionable outputs for the unique needs of various stakeholders like application architects and developers, cyber security personnel, etc. It provides a unique application and infrastructure visualization scheme such that the creation and use of threat models do not require specific security subject matter expertise.
6. Attack Tree: Attack trees are the conceptual diagram showing how an asset, or target, might be attacked. These are multi-level diagrams consisting of one root node, leaves, and children nodes. From bottom to Top, child nodes are conditions that must be satisfied to make the direct parent node true. An attack is considered complete when the root is satisfied. Each node may be satisfied only by its direct child nodes.
Suppose there is 1 grandchild below the root node. In such a case multiple steps must be taken to carry out an attack first the grandchild’s conditions must be satisfied for the direct parent node to be true and then the direct parent node condition must be satisfied to make the root node true. It also has AND and OR options which represent alternatives and different steps toward achieving that goal.
7. Common Vulnerability Scoring System (CVSS): It provides a way to capture the principal characteristics of a vulnerability and produce a numerical score (ranging from 0-10, with 10 being the most severe) depicting its severity.
The score can then be translated into a qualitative representation (such as low, medium, high, and critical) to help organizations properly assess and prioritize their vulnerability management processes.
8. T-MAP: T-MAP is an approach that is used in Commercial Off The Shelf (COTS) systems to calculate the weights of attack paths. This model is developed by using UML class diagrams, access class diagrams, vulnerability class diagrams, target asset class diagrams, and affected Value class diagrams.
Tools for Threat Modelling
1. Microsoft’s Threat Modelling Tool: This tool identifies threats based on STRIDE threat model classification and is based on Data Flow Diagram (DFD), which can be used to discover threats associated with overall IT assets in an organization.
2. MyAppSecurity: It offers the first commercially available threat modeling tool – ThreatModeler. It uses a VAST threat classification scheme and it is based on a Process Flow Diagram (PFD), which provides a detailed view of the risks and vulnerable loopholes.
3. IriuRisk: Offers both a community and a commercial version of the tool. This tool is primarily used to create and maintain a live Threat model throughout the entire SDLC. It connects with several different tools like OWASP ZAP, BDD-Security, etc. to facilitate automation and involves fully customizable questionnaires and Risk Pattern Libraries.
4. securiCAD: It is a threat modeling and risk management tool developed by the Scandinavian company Foresees. Risk is identified and quantified by conducting automated attack simulations of current and future IT architectures and providing decision support based on the findings. securiCAD is offered in both commercial and community editions.
5. SD Elements by Security Compass: It is a software security requirements management platform that includes automated threat modeling capabilities. A short Questionnaire about the technical details and compliance drivers of the application is conducted to generate a set of threats. Countermeasures are included in the form of actionable tasks for developers.
6. Modeling Attack Trees: Commercial Tools like SecurITree, AttackTree+, and open-source tools like ADTool, Ent, and SeaMonster are used to model Attack Trees.
7. CVSS 3.0: CVSS is currently at version 3.0. It is used for the CVSS model. In addition to this, the CVV score of vulnerabilities identified for different hardware and software can be analyzed online, as it aids to identify potential threats, which can harm the system.
8. Tiramisu: This tool is used for the T-MAP approach. It is used to calculate a list of all attack paths and produce overall threats in terms of the total weight of attack paths.
How To Create a Threat Model
All threat modeling processes start with creating a visual representation of the application or system being analyzed. There are two ways to create a visual representation:
1. Visual Representation using Data Flow Diagram
The Microsoft Methodology, PASTA, and Trike each develop a visual representation of the application infrastructure utilizing data flow diagrams (DFD). DFDs were developed in the 1970s as tools for system engineers to provide a high-level visualization of how an application works within a system to move, store, and manipulate data. The concept of trust boundaries was added in the early 2000s by Security professionals in an attempt to make them applicable to threat modeling.
DFDs are used to identify broad categories usually using the STRIDE threat classification scheme. The list of threats identified through such methods is limited and thus a poor starting point for the modeling. DFD based approach uses three main steps:
- View System as an adversary.
- Characterize the system.
- Determine the threats.
- DFD does not accurately represent the design and flow of the application.
- They analyze how data is flowing rather than how users interact with the system.
- DFD-based threat modeling has no standard approach due to which different people create threat models with different outputs for the same scenario or problem.
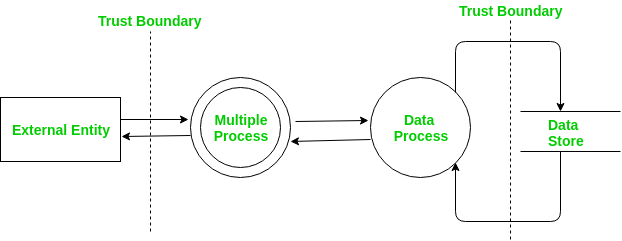
DFD Based Threat Modeling
2. Visual Representation using Process Flow Diagram
To deal with the limitations of DFD-based threat modeling Process Flow Diagrams were introduced in 2011 as a tool to allow Agile software development teams to create threat models based on the application design process. These were specifically designed to illustrate how the attacker thinks.
The attacker does not analyze data flow. Rather, they try to figure out how they can move through an application that was not supported in DFD-based threat modeling.
Their analysis emphasizes how to abuse ordinary use cases to access assets or other targeted goals. The VAST methodology uses PFD for the visual representation of an application.
Threat models based on PFD view applications from the perspective of user interactions. Following are the steps for PFD-based threat modeling:
- Designing application’s use cases
- The communication protocols by which individuals move between use cases are defined
- Including the various technical controls – such as forms, cookies, etc
- PFD-based threat models are easy to understand and don’t require any security expertise.
- Creation of process map -showing how individuals move through an application. Thus, it is easy to understand the application from the attacker’s point of view.
FAQs
1. What is Threat Modeling?
Threat Modeling is a technique that helps in communicating threats and identifying vulnerabilities within the condition of protecting something valuable.
2. How can you approach Threat Modeling?
Threat Modeling can be approached in three ways:
- By approaching through the vulnerability of the asset.
- By approaching through the mind of attackers.
- By approaching through the working of Software.
Share your thoughts in the comments
Please Login to comment...