Adding a third party Module into Metasploit Framework
Last Updated :
26 Feb, 2024
Metasploit Framework is a popular open-source tool for security testing and penetration testing. It comes packed with hundreds of ready-to-use exploits, payloads, encoders, and more to help test systems for weaknesses. However, the true power of Metasploit lies in its modular architecture that allows the community to contribute and expand its capabilities. As new vulnerabilities are discovered, third-party modules are developed that can be easily added into Metasploit.
In this article, we will explore through the steps to install a custom third-party module in Metasploit. We will see how to identify module GitHub repositories, download and place the files correctly, load the module and access the new functionality within Metasploit.
How to add a third-party Module to the Metasploit Framework?
Step 1: Download the Module
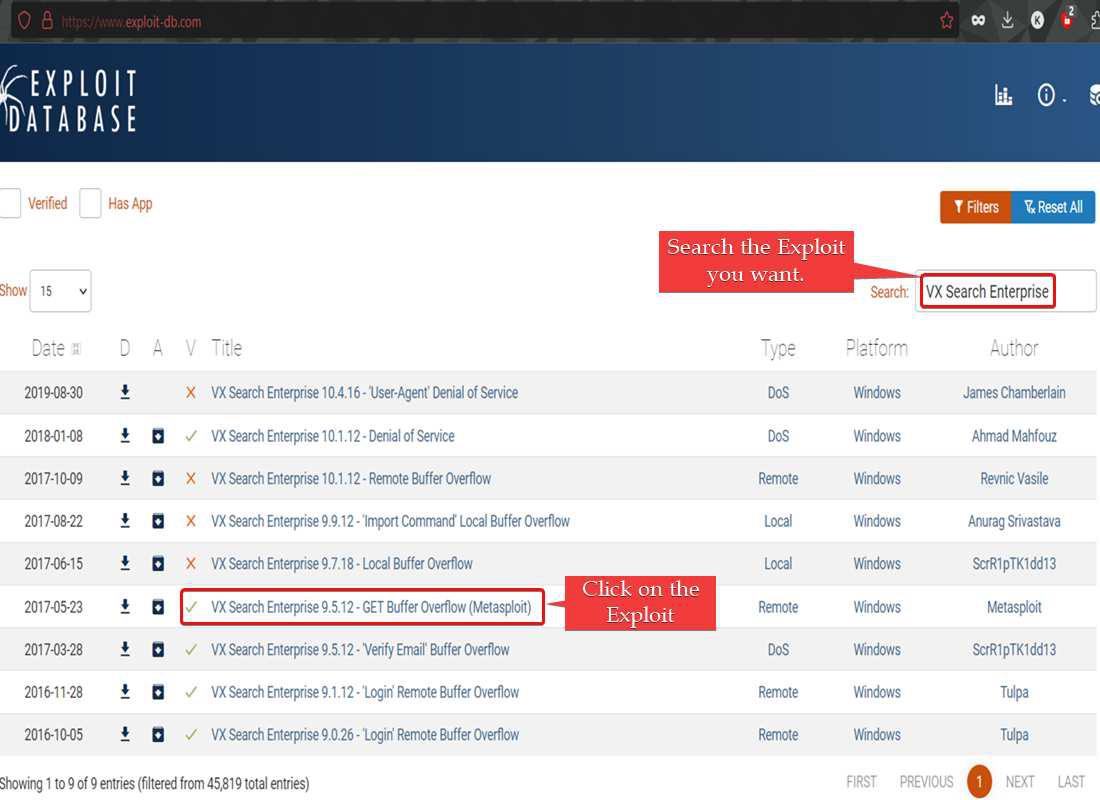
Locate and download the desired Metasploit module from Exploit-db by searching for “metasploit” or the specific module name. Ensure it suits your requirements and is compatible with your Metasploit version.
Note: We are going to add buffer overflow exploit for VX Search Enterprise v9.5.12. This module exploits a stack-based buffer overflow vulnerability in the web interface of VX Search Enterprise v9.5.12, caused by improper bounds checking of the request path in HTTP GET requests sent to the built-in web server. This module has been tested successfully on Windows 11 x64.
To add the third-party SMB exploit module to the Metasploit Framework, navigate to the Metasploit directory in your terminal, commonly where SMB-related exploit modules are stored. Use the appropriate command to copy or move the new module into this directory for installation.
Command:
cd /usr/share/metasploit-framework/modules/exploits/windows/smb
Output:

Identify the exploit module you wish to add to Metasploit by searching on platforms like exploit-db.com, GitHub, or packetstormsecurity. Copy the link to the page hosting the exploit module for reference during the installation process.
Command:
wget ( exploit link )
Output:
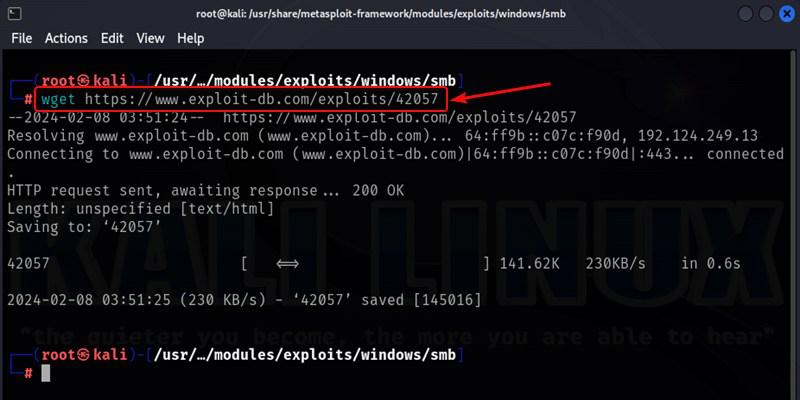
Using wget to download the exploit files directly into the modules directory allows easily adding third party Metasploit modules from any source.
Step 2: Reloading and Searching the Module
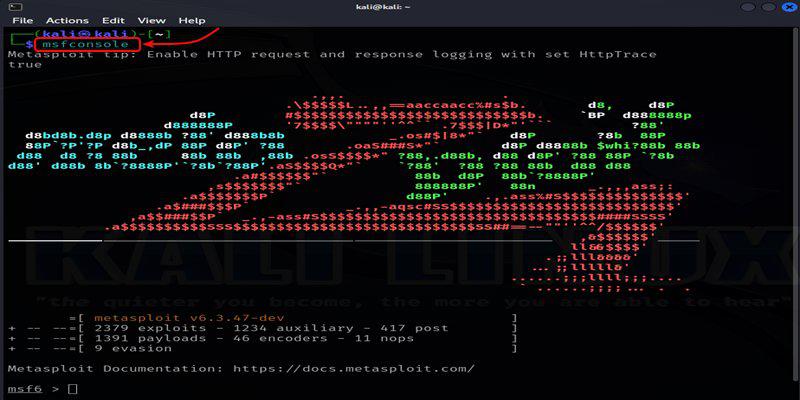
After downloading the third-party exploit modules into the Metasploit folders, open the Metasploit Framework using the provided command. Once loaded, you can search for and utilize the newly added exploit modules.
Command:
msfconsole
Output:
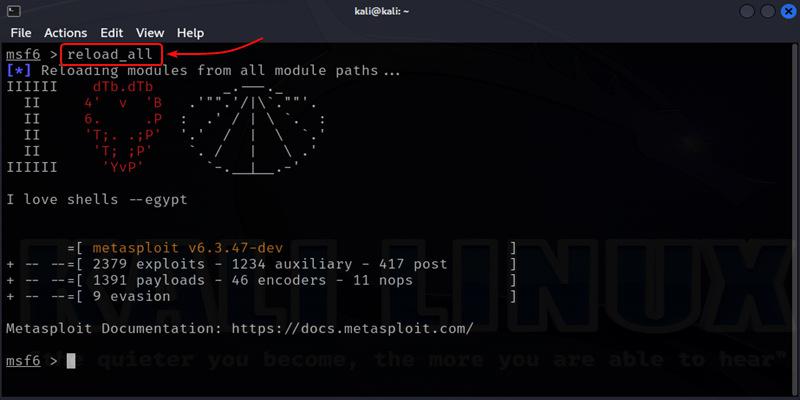
After adding new third-party modules to the Metasploit Framework, it’s crucial to reload Metasploit for the changes to take effect. Utilize the command specified below to initiate a reload, ensuring that all modules, including the newly added ones, are updated and accessible for use in your penetration testing activities. This step ensures the framework recognizes and incorporates the newly added modules.
Command:
reload_all
Output:
To locate a module in the Metasploit Framework, use the provided command. You can search for modules based on their name or description keywords. For example, the following command displays all modules with “VX” in their name or description:
Command:
search VX
Output:
![Searching for the Moduel [Newly Added]](https://media.geeksforgeeks.org/wp-content/uploads/20240208155009/6.jpg)
Step 3: Set-Up the Exploit and Check the Information
Set up the exploit by loading the new third-party module using the “use” command in Metasploit. After loading, check the module information using the “info” command to ensure its configuration and parameters are correctly set.
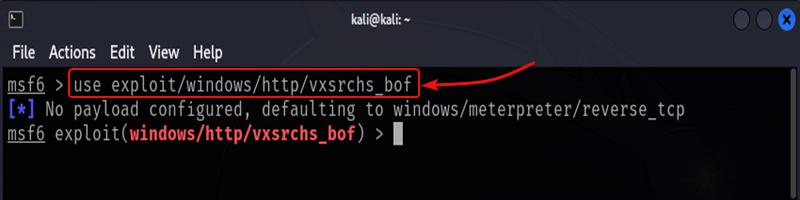
Command:
use exploit/windows/http/vxsrchs_bof
Output:
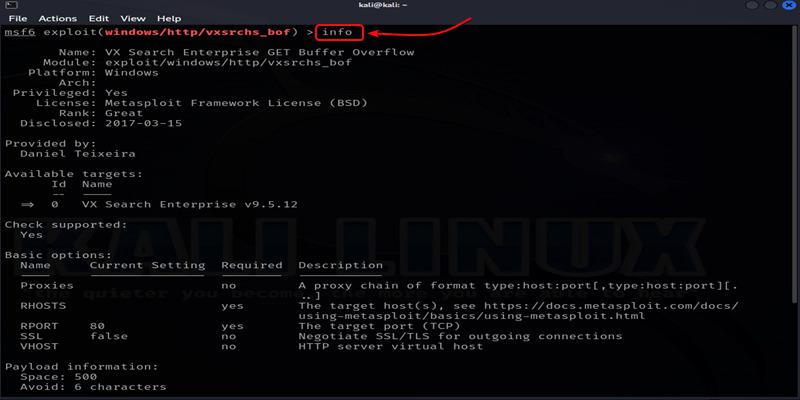
To check the information of the loaded module, type the command “info” in the Metasploit console and press enter. This command provides details about the module, including its name, description, author, and available options, ensuring you have the necessary information before configuring and running the exploit.
Command:
info
Output:
Conclusion
In conclusion, adding a third-party module to the Metasploit Framework involves identifying, downloading, and placing the module correctly, followed by reloading Metasploit for the changes to take effect. The modular architecture of Metasploit allows for seamless integration of community-contributed modules, expanding its capabilities. By following these steps, users can enhance their penetration testing toolkit with custom exploits, showcasing the flexibility and extensibility of the Metasploit Framework.
Share your thoughts in the comments
Please Login to comment...