What is User Authentication in DBMS?
Last Updated :
18 Mar, 2024
User Authentication is a process in which the identity of any user is verified before they can access anything in your database. It is the process of securing data from unauthorized access. It is important to implement user authentication in DBMS to prevent data theft, data loss, or network attacks.
There are various methods of data authentication in DBMS such as multi-factor authentication, password authentication certificate authentication, biometrics token authentication, device authentication API authentication, etc.
In this article, we will be discussing the importance and implementation of user authentication in DBMS.
What is User Authentication in DBMS?
It is the process of verifying whether the person accessing the data is legitimate or not. In other words, it is a process in DBMS of verifying the identity of the user to prevent unauthorized access to any database. It is used in securing the database and preventing malicious access.
It typically involves asking the user for a username and password to access the contents of any database. These credentials are typically also stored in another database which is used to verify the legitimacy of these credentials by matching them both and checking if they are correct. In simple terms, only the correct person who is authorized to access the data inside the database is allowed to do so. There are various benefits of user authentication in DBMS:
- Preventing unauthorized or malicious access: Proper authentication in DBMS will allow you to prevent unauthorized access which can lead to harm such as stealing, modifying, or deleting your important data.
- Preventing Data Loss & corruption: User authentication in DBMS allows you to prevent data loss and corruption by verifying only experts are allowed to access the database. An unauthorized person may not have proper understanding about the structure of the DBMS which may lead to accidental deletion of important data.
- Providing Access Control: It means that only some specific user roles (such as Administrators) are allowed to access the data which helps prevent data abuse and accidental information loss.
- Securing Networks and Network Chains: User authentication in a fairly large database will help prevent ransomware attacks on a large network of any organization by preventing unauthorized access to the interface.
- Preventing Data theft: User authentication will help prevent data theft by not allowing hackers or people with malicious intent to access and leak the data on the dark web.
Implementing User Authentication in DBMS
To implement user authentication in DBMS, you need to follow certain steps and guidelines to ensure the proper implementation. The most common way of implementing user authentication in DBMS in providing access control, Access control allows only certain individuals or set of individuals to access the contents of any DBMS.
One of the most popular ways of providing user authentication in DBMS are known as role based access control and attribute based access control.
Role Based Access Control
Role based access control uses a certain types of roles to specify the accessibility of any database. There are mainly two types of roles in role based access control:
- User: A user is a normal individual who can access the contents of any database. They cannot change/delete the contents of any database, they can only view the content. It is a basic role in which the individual is only using the service and cannot change or interfere with the contents of the database
- Administrator: An administrator is a person or individual who is used to manage all of the contents of any database. They can change/delete/copy or merge the contents of database in any way that is required. In simple terms they have all the control required to modify the contents of any DBMS.
Attribute Based Access Control
Attribute based access control is an authorization technique which uses certain properties known as attributes to specifiy the accessibility instead of roles.
Attribute based access control is an authorization system that defines access based on characteristics such as:
- Security principals
- Resources
- The environment of an access request
- Characteristics, such as department, location, manager, and time of day
- User characteristics
- Object characteristics
- Action types
Types of User Authentication in DBMS
There are many types of user authentication in DBMS, which vary from usability to usability. Different kinds of DBMS require different types of user authentication. The main types of user authentication in DBMS are specified below:
Username & Password Authentication
It is one of the simplest forms of user authentication where the person accessing the DBMS is identifed through a certain username and password. These username and password are unique. Username will help distinguish between the persons accessing the database and Password will help you prevent unauthorized access to any database.
This type of authentication is sometimes also known as Login Authentication.
.png)
Certificiate Based User Authentication
Certificate based authentication is a type of user authentication which uses a digital certificate which is derived from cryptography to identify a user, device or machine. It is used to grant access to any application, database or any network. It is a much more secure alternative to user and password authentication, It uses a digital certificate or document to verify a user which contains information or details such as:
- The public key
- The user or device’s name
- The name of the Certificate Authority (CA) that issued the certificate
- The date from which the certificate is valid
- The expiry date of the certificate
- The version number of the certificate data
- A serial number
Token Based User Authenitcation
A token based authenitcation allows the user the verify their identify by reciving a unique access token. This token is used by the user to access the database rather than having them re-enter their credentials each time. Auth tokens are like tickets which the users retain as long as the token remains valid. It is a much more secure alternative to username and password based authentication.
It is often used to grant temprory access based on the date and time. Tokens can be useful in scenarios where you might need to grant any user temprory access to the database.
Multi-Factor Authenitcation
A multifactor authenitcation approach is such in which the login process requires multiple methods of authenitcation such as an OTP (one time password) or E-mail verification.
It is one of the most popular methods of authentication which secures any database by verifying only the real individuals can access any database. It is used with the login authentication and even when the password has been compromised this type of authentication can secure the database by only allowing the real individual to access the contents and not any imposter who might have gained the password of the real individual.
It is a type of authentication which uses a combination of crtieria such as login credentials, biometric scan, time and location etc.
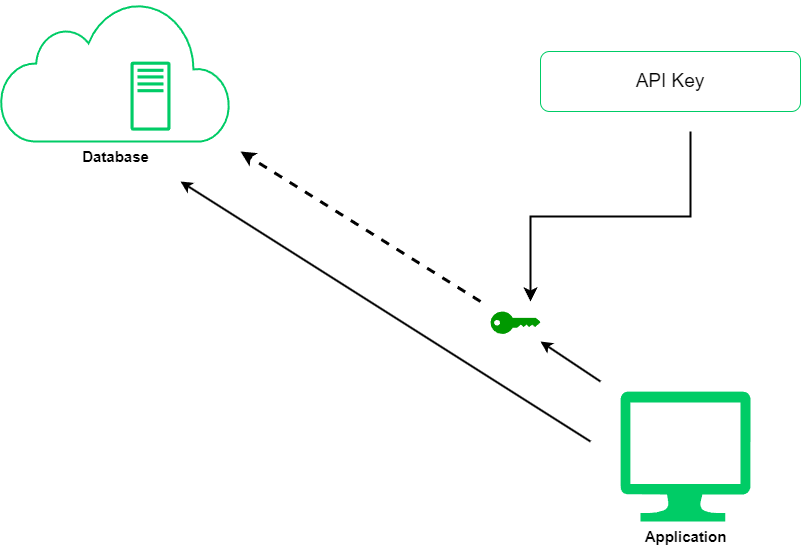
API Key Authenitcation
An application programming interface (API) key is a code used to identify an application or user and is used for authentication. It is a type of credential which is used to verify the user before accessing any database.
It is a unique identifier which is used to perform API call. API calls are ways for program to interact with each other, Every program has a unique API key for the user which can be used to access any part of the database.
Importance of User Authentication in DBMS
There are several advantages of implementing user authentication in DBMS such as:
- It helps increase the data security and integrity: User authentication is used to ensure that only the authorized person is accessing the database. It is used to help in preventing unauthorized access and data loss from malcious access.
- Promotes data confidentiality: User authentication helps to contribute the data confidentiality by ensuring only the authorized users can view the sensitive information stored inside the database.
- Better Database management: User authentication helps database management by assigning roles such as end-user and administrator which properly specifies the people who can access and modify the database.
- Session Management: User authentication is closely tied to session management in DBMS. Once a user is authenticated, the system establishes a session for that user, allowing them to interact with the database until the session expires or is terminated.
- Prevents data leak: User authentication will certainly help preventing the leakage of important information such as Addresses, Phone numbers or confidential information of any person stored inside a database by providing better authentication facility.
- Prevents Network attacks: Authenticating any user insided a database mangement system will ensure no such individual who aims to harm the system may enter the database and destroy important contents of the DBMS. Unauthorized access to database may lead to coordinated network attacks which can harm the organizations growth and integrity.
Conclusion
In conclusion, User authentication is a process in which the identify of any user is verified before they can access anything in your database. It is the process of securing data from unauthorized access. It is very important in DBMS to implement user authentication since a databse can hold multiple sensitive information which needs to be secured at all times.
Frequently Asked Questions on User Authentication in DBMS – FAQs
What is the significance of user authenitcation in DBMS?
User authentication in DBMS helps you to secure your databse by only allowing certain authorized individuals to access the DBMS and preventing misuse.
What is the most popular way to implement user authentication in DBMS?
The most popular way to integrate user authentication in DBMS is through username and password protection which allows only those individuals who have a certain username and a corresponding password to access the database.
What is API authenitcation?
API authentication is the process of verifying the identity of a user or other actor – in order to confirm that they have the necessary permissions for whatever they’re trying to do via an API, such as accessing any database or modifying it.
Share your thoughts in the comments
Please Login to comment...