Gate IT 2007
Question 11
The address sequence generated by tracing a particular program executing in a pure demand paging system with 100 bytes per page is
0100, 0200, 0430, 0499, 0510, 0530, 0560, 0120, 0220, 0240, 0260, 0320, 0410.
Suppose that the memory can store only one page and if x is the address which causes a page fault then the bytes from addresses x to x + 99 are loaded on to the memory.
How many page faults will occur ?
0100, 0200, 0430, 0499, 0510, 0530, 0560, 0120, 0220, 0240, 0260, 0320, 0410.
Suppose that the memory can store only one page and if x is the address which causes a page fault then the bytes from addresses x to x + 99 are loaded on to the memory.
How many page faults will occur ?
Question 12
Consider the following statements about the timeout value used in TCP.
i. The timeout value is set to the RTT (Round Trip Time) measured during TCP connection establishment for the entire duration of the connection.
ii. Appropriate RTT estimation algorithm is used to set the timeout value of a TCP connection.
iii. Timeout value is set to twice the propagation delay from the sender to the receiver.
Which of the following choices hold?
Question 13
Consider a TCP connection in a state where there are no outstanding ACKs. The sender sends two segments back to back. The sequence numbers of the first and second segments are 230 and 290 respectively. The first segment was lost, but the second segment was received correctly by the receiver. Let X be the amount of data carried in the first segment (in bytes), and Y be the ACK number sent by the receiver.
The values of X and Y (in that order) are
Question 14
Consider the following two statements:
i. A hash function (these are often used for computing digital signatures) is an injective function.
A. encryption technique such as DES performs a permutation on the elements of its input alphabet.
Which one of the following options is valid for the above two statements?
Question 15
Exponentiation is a heavily used operation in public key cryptography. Which of the following options is the tightest upper bound on the number of multiplications required to compute bn mod m,0≤b,n≤m ?
Question 16
Consider the XML document fragment given below:
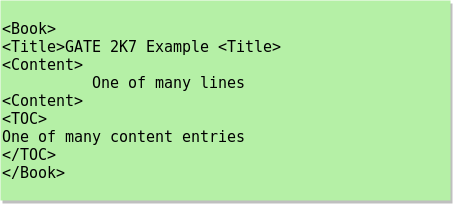
Consider the XPath expression: *[not (self ) : : TOC]
What would be the result of the given XPath expression when the current node is Book?

Consider the XPath expression: *[not (self ) : : TOC]
What would be the result of the given XPath expression when the current node is Book?
Question 18
Consider the XML document fragment given below:
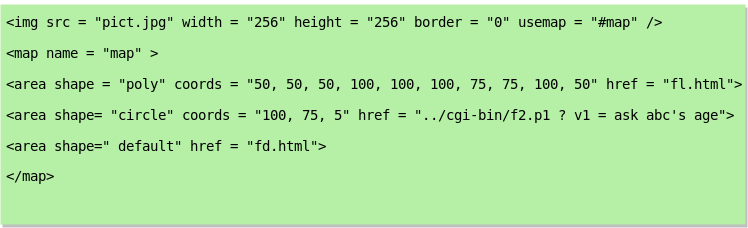
With reference to the HTML lines given above, consider the following statements.
1. Clicking on the point <80, 75> does not have any effect.
2. The web browser can identify the area applicable to the mouse-click within the image and the subsequent action to be taken without additional responses from the web server.
3. The dots in the cgi-bin URL will be resolved by the web browser before it is sent to the web server
4. The "fd.html" request when sent to the web server will result in a GET request.
Exactly how many of the statements given above are correct?

With reference to the HTML lines given above, consider the following statements.
1. Clicking on the point <80, 75> does not have any effect.
2. The web browser can identify the area applicable to the mouse-click within the image and the subsequent action to be taken without additional responses from the web server.
3. The dots in the cgi-bin URL will be resolved by the web browser before it is sent to the web server
4. The "fd.html" request when sent to the web server will result in a GET request.
Exactly how many of the statements given above are correct?
Question 19
The trapezoidal method is used to evaluate the numerical value of [Tex]\\int_0^1 $e^x$\\,dx[/Tex]. Consider the following values for the step size h.
i. 10-2
ii. 10-3
iii. 10-4
iv. 10-5
For which of these values of the step size h, is the computed value guaranteed to be correct to seven decimal places. Assume that there are no round-off errors in the computation.
i. 10-2
ii. 10-3
iii. 10-4
iv. 10-5
For which of these values of the step size h, is the computed value guaranteed to be correct to seven decimal places. Assume that there are no round-off errors in the computation.
Question 20
A partial order P is defined on the set of natural numbers as follows. Here x/y denotes integer division.
i. (0, 0) ∊ P.
ii. (a, b) ∊ P if and only if a % 10 ≤ b % 10 and (a/10, b/10) ∊ P.
Consider the following ordered pairs:
i. (101, 22)
ii. (22, 101)
iii. (145, 265)
iv. (0, 153)
Which of these ordered pairs of natural numbers are contained in P?
i. (0, 0) ∊ P.
ii. (a, b) ∊ P if and only if a % 10 ≤ b % 10 and (a/10, b/10) ∊ P.
Consider the following ordered pairs:
i. (101, 22)
ii. (22, 101)
iii. (145, 265)
iv. (0, 153)
Which of these ordered pairs of natural numbers are contained in P?
There are 80 questions to complete.
Last Updated :
Take a part in the ongoing discussion