Gate IT 2005
Question 81
i = 0
do {
j = i + 1;
while ((j < n) && E1)
j++;
if (j < n) E2;
} while (j < n);
flag = 1;
for (j = 0; j < n; j++)
if ((j! = i) && E3)
flag = 0;
if (flag)
printf("Sink exists");
else
printf ("Sink does not exist");
Question 82
i = 0
do {
j = i + 1;
while ((j < n) && E1) j++;
if (j < n) E2;
} while (j < n);
flag = 1;
for (j = 0; j < n; j++)
if ((j! = i) && E3)
flag = 0;
if (flag)
printf("Sink exists");
else
printf("Sink does not exist");
Question 83
- A node determines whether its neighbours in the graph are accessible. If so, it sets the tentative cost to each accessible neighbour as 1. Otherwise, the cost is set to ∞.
- From each accessible neighbour, it gets the costs to relay to other nodes via that neighbour (as the next hop).
- Each node updates its routing table based on the information received in the previous two steps by choosing the minimum cost.
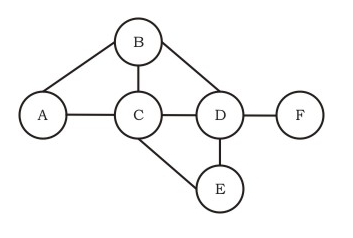
| 1) | Table for node A
| ||||||||||||||||||
| 2) | Table for node C
| ||||||||||||||||||
| 3) | Table for node B
| ||||||||||||||||||
| 4) | Table for node D
|
Question 84
- A node determines whether its neighbours in the graph are accessible. If so, it sets the tentative cost to each accessible neighbour as 1. Otherwise, the cost is set to ∞.
- From each accessible neighbour, it gets the costs to relay to other nodes via that neighbour (as the next hop).
- Each node updates its routing table based on the information received in the previous two steps by choosing the minimum cost.

| 1) | Table for node A
| ||||||||||||||||||
| 2) | Table for node C
| ||||||||||||||||||
| 3) | Table for node B
| ||||||||||||||||||
| 4) | Table for node D
|
Question 85
Question 86
- T11 > T21
- T12 > T22
- T11 < T21
- T12 < T22
Question 87
find -name passwd -printis executed in /etc directory of a computer system running Unix. Which of the following shell commands will give the same information as the above command when executed in the same directory?
Question 88
ln -s file 1 file 2 ln -s file 2 file 3Which of the following types of information would be lost from her file system? (I) Hobbies (II) Friends (III) Courses
Question 89
Question 90
A database table T1 has 2000 records and occupies 80 disk blocks. Another table T2 has 400 records and occupies 20 disk blocks. These two tables have to be joined as per a specified join condition that needs to be evaluated for every pair of records from these two tables. The memory buffer space available can hold exactly one block of records for T1 and one block of records for T2 simultaneously at any point in time. No index is available on either table. If Nested-loop join algorithm is employed to perform the join, with the most appropriate choice of table to be used in outer loop, the number of block accesses required for reading the data are
There are 90 questions to complete.