GATE-CS-2014-(Set-2)
Question 31
Given the STUDENTS relation as shown below.
[caption width="800"]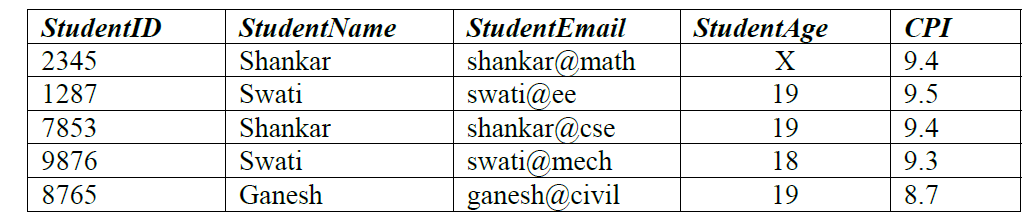 [/caption]
[/caption]
For (StudentName, StudentAge) to be the key for this instance, the value X should not be equal to
Question 32
Question 33
Question 34
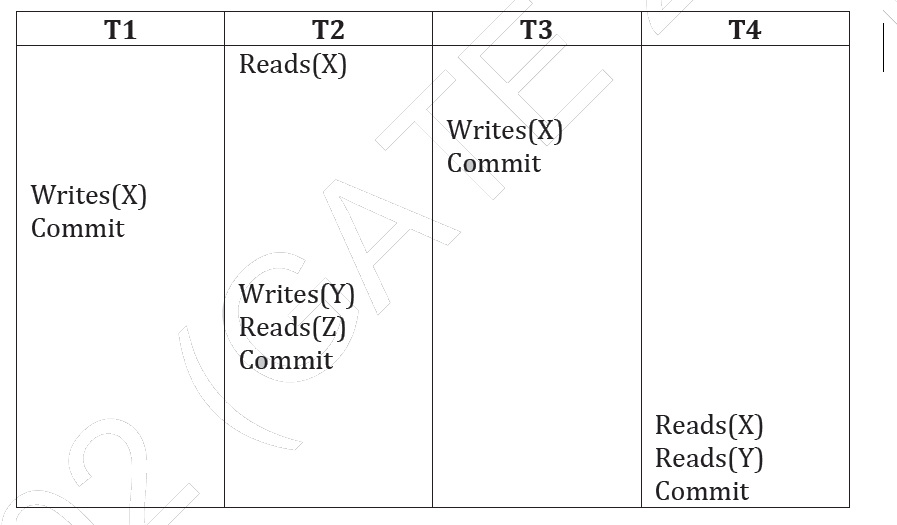
Question 35
Consider the store and forward packet switched network given below. Assume that the bandwidth of each link is 106 bytes / sec. A user on host A sends a file of size 103 bytes to host B through routers R1 and R2 in three different ways. In the first case a single packet containing the complete file is transmitted from A to B. In the second case, the file is split into 10 equal parts, and these packets are transmitted from A to B. In the third case, the file is split into 20 equal parts and these packets are sent from A to B. Each packet contains 100 bytes of header information along with the user data. Consider only transmission time and ignore processing, queuing and propagation delays. Also assume that there are no errors during transmission. Let T1, T2 and T3 be the times taken to transmit the file in the first, second and third case respectively. Which one of the following is CORRECT?
[caption width="800"]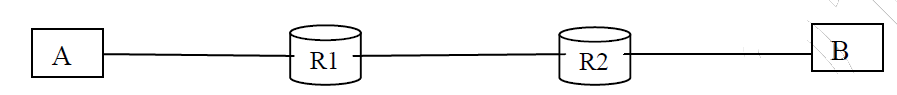 [/caption]
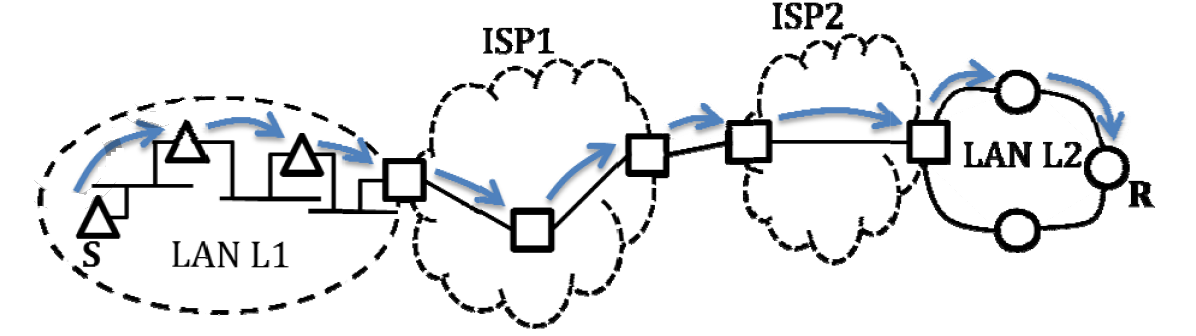
[/caption]Question 36
Q—R1—R2—R3—HH acts as an HTTP server, and Q connects to H via HTTP and downloads a file. Session layer encryption is used, with DES as the shared key encryption protocol. Consider the following four pieces of information:
[I1] The URL of the file downloaded by Q [I2] The TCP port numbers at Q and H [I3] The IP addresses of Q and H [I4] The link layer addresses of Q and HWhich of I1, I2, I3, and I4 can an intruder learn through sniffing at R2 alone?
Question 37
Question 38
Question 39
Consider a join (relation algebra) between relations r(R)and s(S) using the nested loop method. There are 3 buffers each of size equal to disk block size, out of which one buffer is reserved for intermediate results. Assuming size(r(R)) < size(s(S)), the join will have fewer number of disk block accesses if
Question 40
There are 64 questions to complete.