XSRFProbe – CSRF Audit and Exploitation Toolkit
Last Updated :
23 Feb, 2022
Cross-Site Request Forgery (CSRF) is an attack that causes certified users to raise a request to a Web application against which they are currently certified. XSRFProbe tool is an advanced and automated cyber security tool that can detect CSRF vulnerabilities in the target web application. This tool is developed in the Python Language and is also available on the GitHub platform. We get the detailed output in the form of documents that contains all the logs and the crucial information regarding our scan.
Note: Make Sure You have Python Installed on your System, as this is a python-based tool. Click to check the Installation process: Python Installation Steps on Linux
Installation of XSRFProbe Tool on Kali Linux OS
Step 1: Use the following command to install the tool in your Kali Linux operating system.
git clone https://github.com/0xInfection/XSRFProbe.git
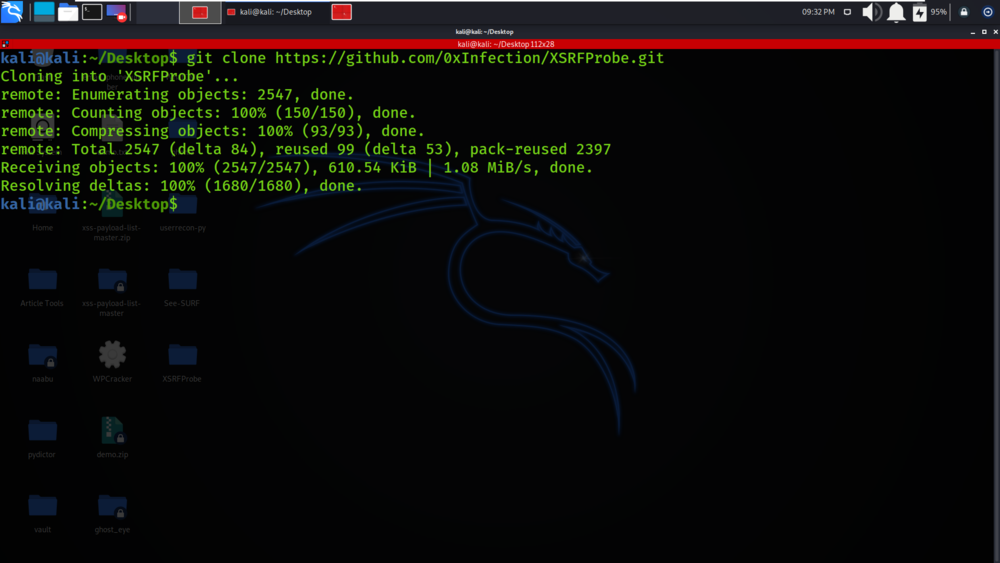
Step 2: Now use the following command to move into the directory of the tool. You have to move in the directory in order to run the tool.
cd XSRFProbe
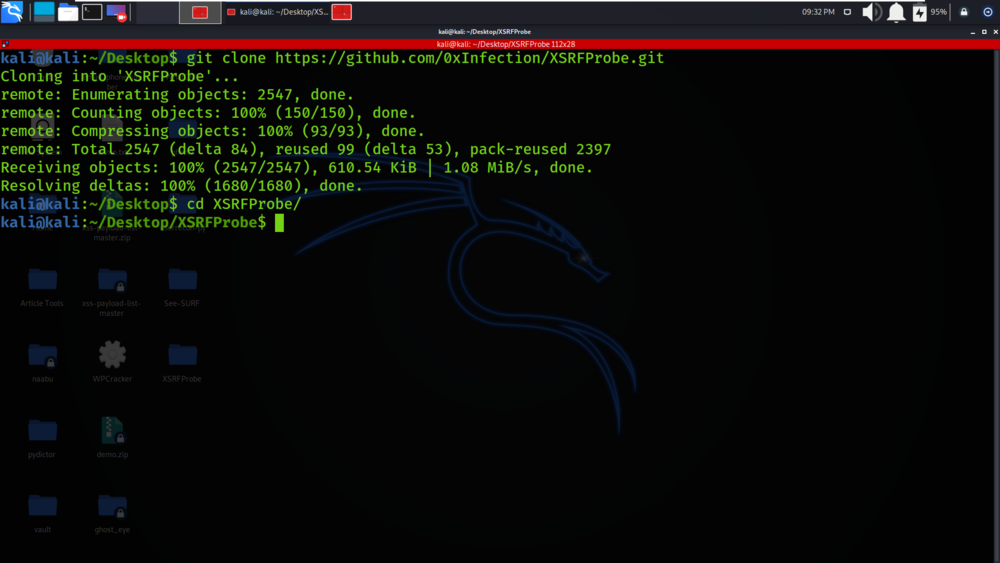
Step 3: You are in the directory of the XSRFProbe. Now you have to install the tool by using the following command.
sudo python3 setup.py install
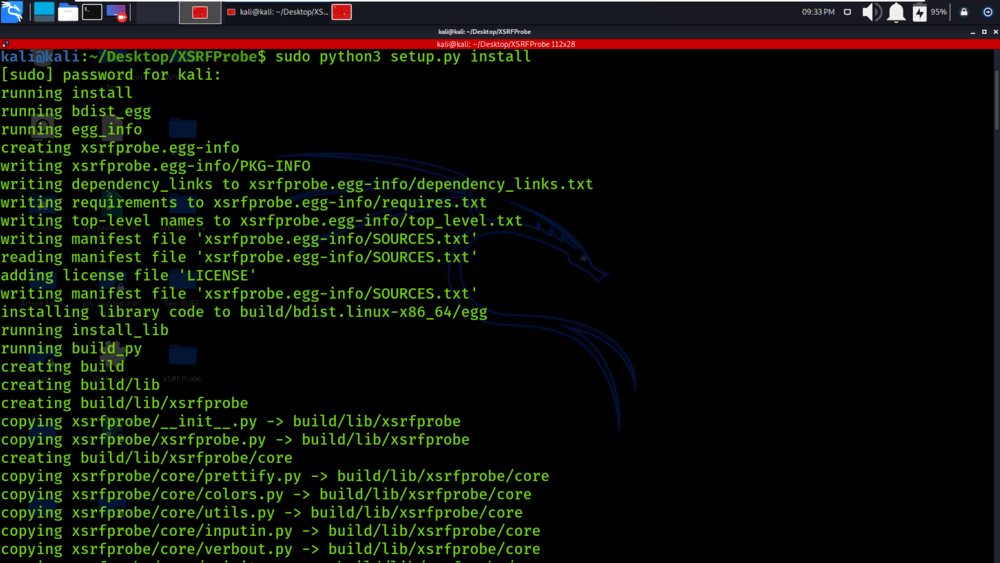
Step 4: All the dependencies have been installed in your Kali Linux operating system. Now use the following command to run the tool and check the help section.
xsrfprobe -h
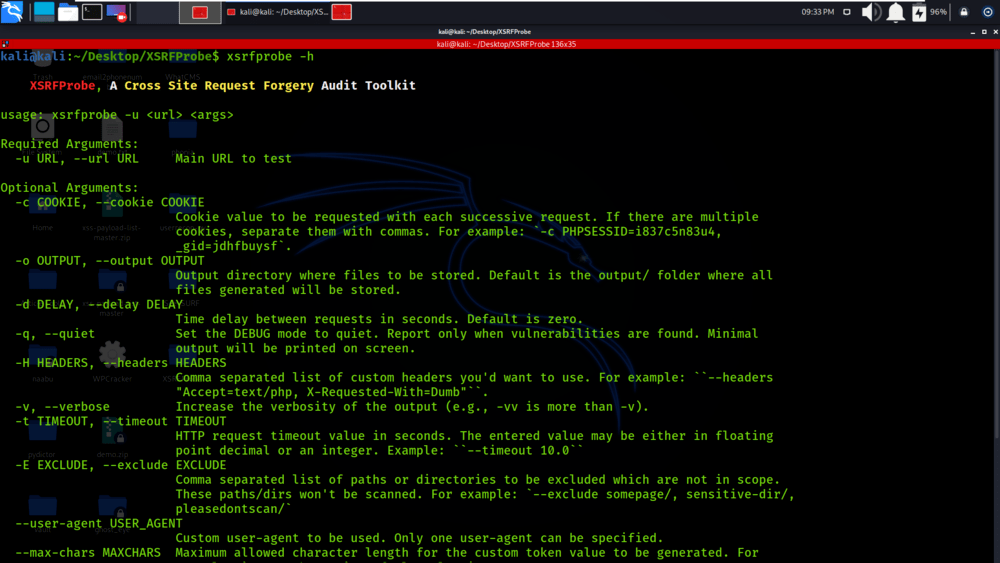
Working with XSRFProbe Tool on Kali Linux OS
Example/Usage: Main URL to test
xsrfprpbe -u http://www.geeksforgeeks.org
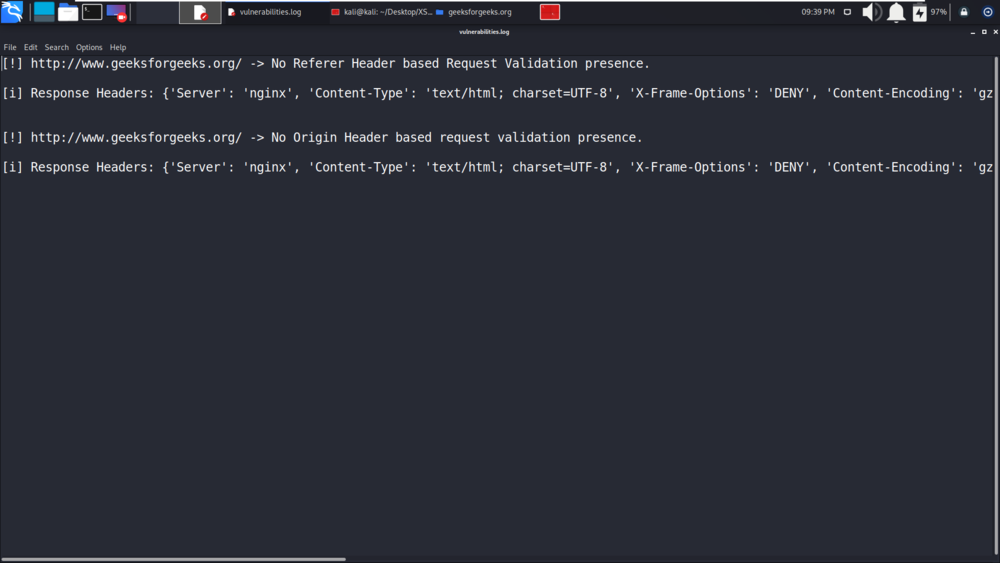
Testing on the geeksforgeeks.org domain is been started successfully.
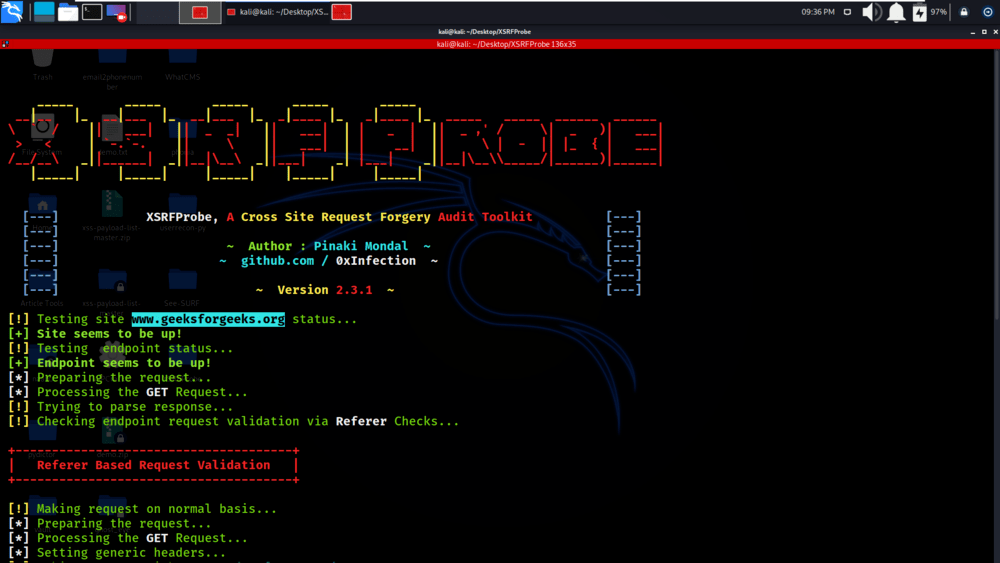
The tool is checking for Referrer-based Request Validation on geeksforgeeks.org.
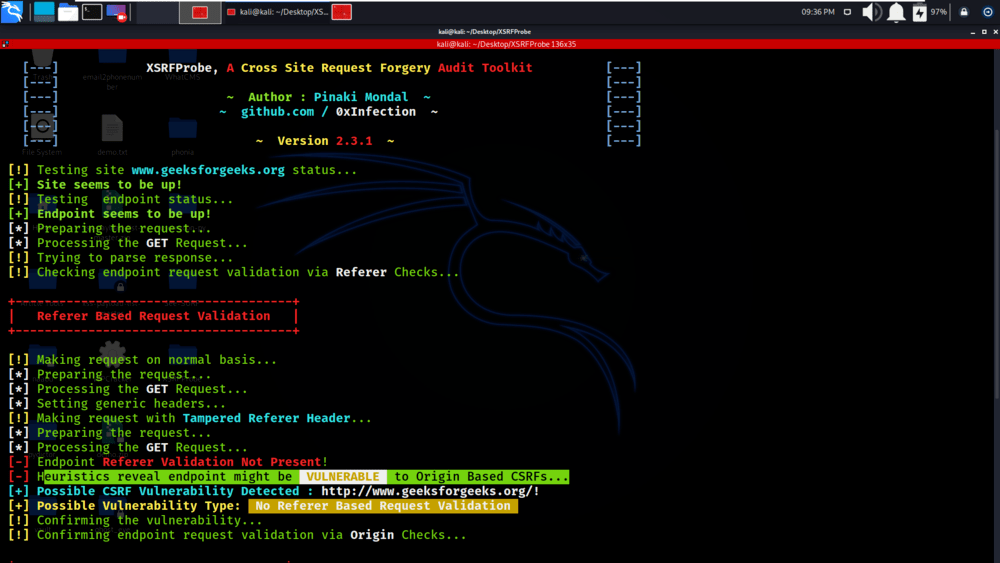
Now in the below screenshot, you can see that tool is been checking for Origin Based Request Validation.
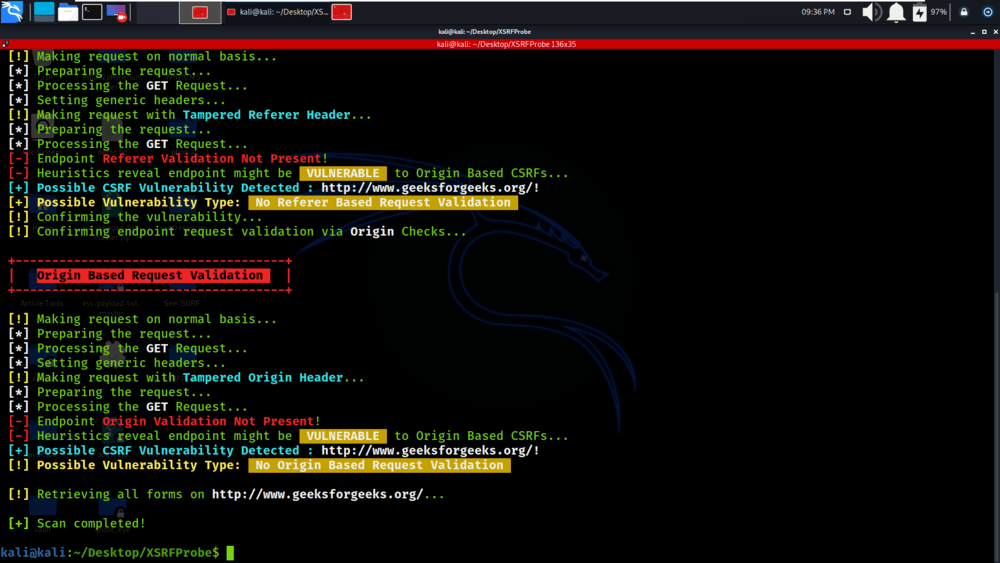
All the output logs are been saved in the output directory.
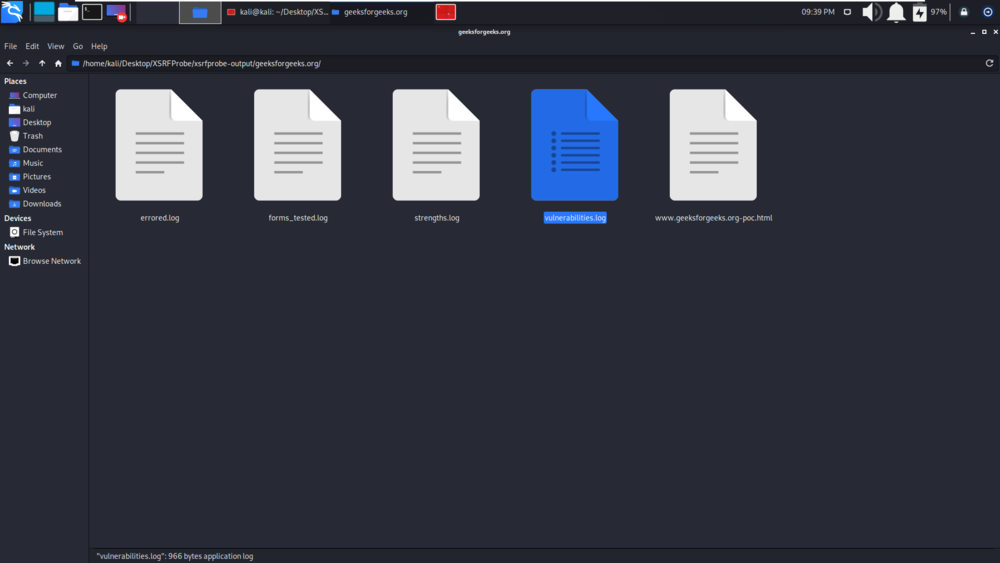
We are displaying the vulnerabilities.log file which has some crucial information about the scan.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...