What is Zed Attack Proxy?
Last Updated :
14 Jun, 2022
Zed Attack Proxy is an open-source security software written in Java programming language and released in 2010. It is used to scan web applications and find vulnerabilities in it. It was started as a small project by the Open Web Application Security Project (OWASP) and now it is the most active project maintained by thousands of individuals around the globe. It is available for Linux, Windows, and mac in 29 languages. It can also be used as a proxy server like a burp suite to manipulate the request including the HTTPS request. Daemon mode is also present in it which can later be controlled by REST API.
Features:
- Passive Scanner
- Automated Scanner
- Proxy Server
- Port Identification
- Directory Searching
- Brute Force Attack
- Web Crawler
- Fuzzer
Why do we use Zed Attack Proxy? Zed Attack Proxy is used to detect vulnerabilities present on any web server and try to remove them. Here is some big vulnerability that could be present in the web server:
- SQL injection
- Cross-site scripting (XSS)
- Broken access control
- Security miss-configuration
- Broken authentication
- Sensitive data exposure
- Cross-site request forgery (CSRF)
- Using components with known vulnerabilities.
Some Important Terminologies:
- Proxy Server: It is a server that acts as a mediator for clients who want to go through the request and want to alter them.
- Spider: It is a type of information gathering process in which the application in this case ZAP will go through the whole web page and try to find out all the links and other important details.
- Passive Scan: In this type of scanning the vulnerability is detected without getting in direct contact with the target machine.
- Active Scan: In this, the vulnerability is detected by getting in direct contact with the target machine which makes it very easy to be detected by the administrator.
Working Process: First we set up the proxy server with any browser. The browser sends website data to the proxy server and then the browser inside the ZAP process the request and perform attacks and generates the report. 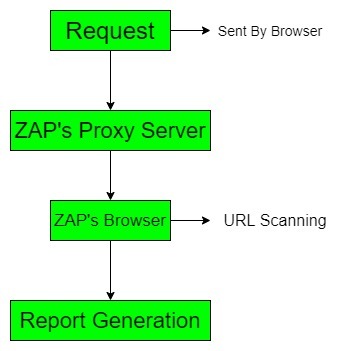
Configuration Steps:
- Step 1: Download ZAP from https://www.zaproxy.org/download/ by selecting the proper operating system.
- Step 2: Run the file and follow the instruction until the installation is complete.
Steps to Run:
- Step 1: Open the application through the terminal or by clicking on the icon.
- Step 2: In the next step, select the first option and click start.

- Step 3: Now choose a target to scan and enter its web address in the green highlighted box and click attack.

- Step 4: Now you will have to wait for a few minutes to get the result.
Share your thoughts in the comments
Please Login to comment...