What is Pegasus Spyware and How It Works?
Last Updated :
02 Aug, 2021
No one can deny that in this digitally advanced era, the incidents of cyberattacks like hacking, data breaches, etc. are increasing exponentially. And in a similar context, recently a term has become very much popular worldwide – ‘Pegasus Spyware’.

If you don’t know about it yet then no worries as here in this article we’re going to know about every crucial aspect of this ‘Pegasus Spyware’ such as what is this, how it works, why it is being used, etc. But before knowing about the ‘Pegasus Spyware’, first, let’s understand what is Spyware? Spyware is some sort of malicious software that is usually installed in your computer or mobile device, even without your consent, to damage your system or steal sensitive data.
What is Pegasus Spyware?
The Pegasus Spyware, created by the Israeli cyber intelligence firm NSO Group, is also designed to hack the computers or mobile devices to gain access to the device and retrieve the data from it without the user’s consent and then deliver it to the third party who is actually spying on you. However, the parent organization of this Pegasus Spyware claims that it is intended to help government authorities to be used against terrorists and criminals by spying on them.
Pegasus Spyware was first identified around 4-5 years ago when a human rights activist from the United Arab Emirates received a text message that was actually a phishing setup. He sent these messages to the security agency and it was found out that if he (the user) had opened those links – his phone would have been infected with the malware, named Pegasus.
Recently, a database of around 50,000 phone numbers that may have been targeted for surveillance using Pegasus, was leaked to several standard investigative media platforms. And most importantly, among these 50,000 contacts, the Pegasus Project (a general name given to this investigative report) found that there are hundreds of public officials contacts also. However, the availability of any number in this database doesn’t compulsorily mean that the respective device was successfully penetrated – and various cyber investigation mechanisms are currently going on for the same.
How Does It work?
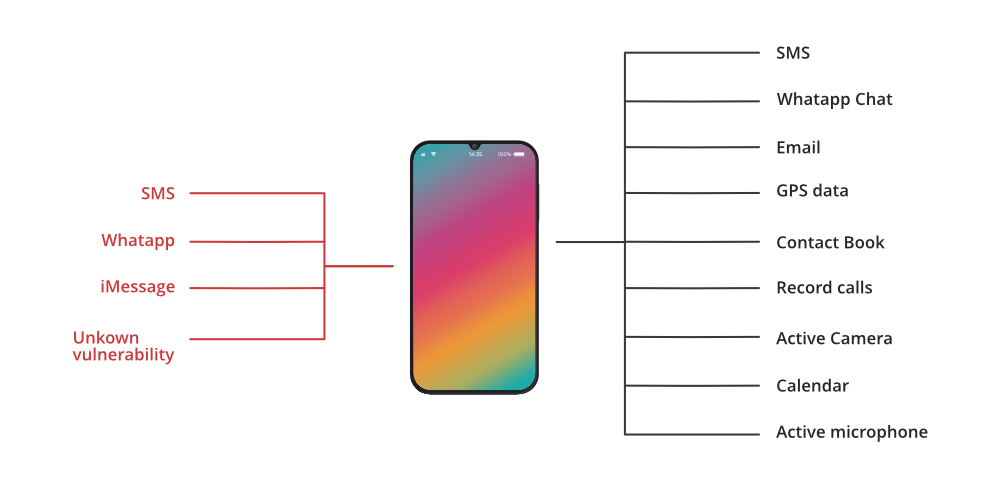
Let us tell you that this Pegasus Spyware attacks the devices so seamlessly that even the device owner might not have any idea about it. You can better understand this with a situation like even a WhatsApp missed call (yes, you heard it right….a missed call) can make the Pegasus Spyware hack your device. Other than that, based on various standard reports, it has been observed that Pegasus is using a variety of endpoints to attack the devices such as it is using iMessage to attack iPhones.
The noticeable thing here is that it follows the zero-click method i.e, the device owner even isn’t required to click on the message, mail, link, etc. or to give any input to make the malware work. On top of that, if the user finds something suspicious and deletes the message – the spyware would still infect the device.
And once the Pegasus gets into your smartphone, now your text messages & emails, contacts, photos, passwords, etc. can be accessed by the other party. In fact, the access is given to such an extent that even your device mic or camera can also be operated by the one who’s is spying on you very conveniently. The Pegasus Spyware can even access the end-to-end encrypted messages or files as it can now steal them before the encryption or after the decryption.
You also need to know that the company behind this Pegasus Spyware made Amazon’s AWS cloud infrastructure as a part of their system – however, now Amazon has deactivated all the accounts of the NSO group after the advent of recent investigation reports.
Can this Pegasus Spyware affect our normal lives? – Okay, firstly we need to understand that as said by NSO Group, the intention behind the development of this ‘Pegasus Spyware’ is to help the government bodies by providing them the advanced technology to detect and prevent terrorism or criminal activities. Also, this spyware is quite expensive to use (as per the reports, it charges government bodies around USD 650,000 to spy on 10 iPhones or android smartphones with some additional charges like installation fee, annual maintenance, etc.) – hence, practically it won’t be feasible for the govt. agencies to use this tool without any solid or justified reason. So, you might consider yourself safe from this Pegasus Spyware due to these particular reasons.
In fact, Apple has also issued a statement over this Pegasus Spyware matter – “Attacks like the ones described are highly sophisticated, cost millions of dollars to develop, often have a short shelf life, and are used to target specific individuals” that is somehow true as well and again depicts that normal users do not need to worry much about it.
But, what if in the future there comes spyware that is as strong (or even more than that) as this Pegasus Spyware and being quite affordable as well – then don’t you think it can be misused and impact normal people lives as well. Yes, that’s actually the point! Instead of just ignoring this Pegasus Spyware, we should be well-aware of this, understand its pros and cons to avoid such kinds of spyware or cyberattacks in the future. For instance, we can consider the below-mentioned points to prevent ourselves from these Spywares likes Pegasus, etc.
- One of the basic approaches is to keep the Operating System and other apps in the device updated.
- Open only those links or messages on your device that are sent by recognized and trusted contacts.
- You should avoid using public WiFi services such as at cafes, parks, etc.
- Always have a backup of the important data stored in your device.
Also, do remember that following the above-mentioned approaches will not make you completely safe from spyware like Pegasus and others – but yes, the more you’ll follow such strategies and preventive measures, the more your risk to get attacked by these Spywares will get reduce!!
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...