What is Multiplicative Cipher in Cryptography?
Last Updated :
08 Apr, 2024
Prerequisites: What is a Substitution Cipher , What is a Monoalphabetic Cipher?
A multiplicative cipher is a type of cipher that comes under a monoalphabetic cipher, in which each letter that is present in the plaintext is replaced by a corresponding letter of the ciphertext, according to a fixed multiplication key.
The basic task behind the multiplicative cipher is to use a large prime number as a multiplication key, and then use the modular arithmetic of the integers modulo, the key to encode and decode the plaintext. The encryption process is done by multiplying the numerical value of each letter in the plaintext by the key and then taking the result modulo the key. For example, if the key is 7 and the plaintext letter is ‘s’, the numerical value of ‘s’ is 18, and so the ciphertext letter is (18*7) mod 26 = 22. So the cipher text symbol will be ‘w’ for the letter ‘a in this case.
The decryption process is simply the reverse of the encryption process, i.e., by dividing the numerical value of each letter in the ciphertext by key and then taking the result modulo of the key. One of the main advantages of the multiplicative cipher is its simplicity i.e. It is easy to implement and easy to understand, and it does not require any large amount of computational power. In conclusion, we can say that multiplicative cipher is a simple encryption technique that can be easily implemented. However, it is not a secure method of encryption and can be easily broken too. It is suitable for small-scale applications but not recommended for practical purposes.
Formula:
C = (P * K) Mod m
Here,
- C = Cipher text
- P = Plain text
- K = Key
- Mod = Modulus
- m = A fixed positive Integer(Example 26 for alphabets)
Encryption
Let us understand this by implementing a simple example using the Multiplicative Cipher.
Step 1: So here we are going to cipher text a simple plain text, let us assume the plain text is “GEEKSFORGEEKS” and let us consider the key as 7.
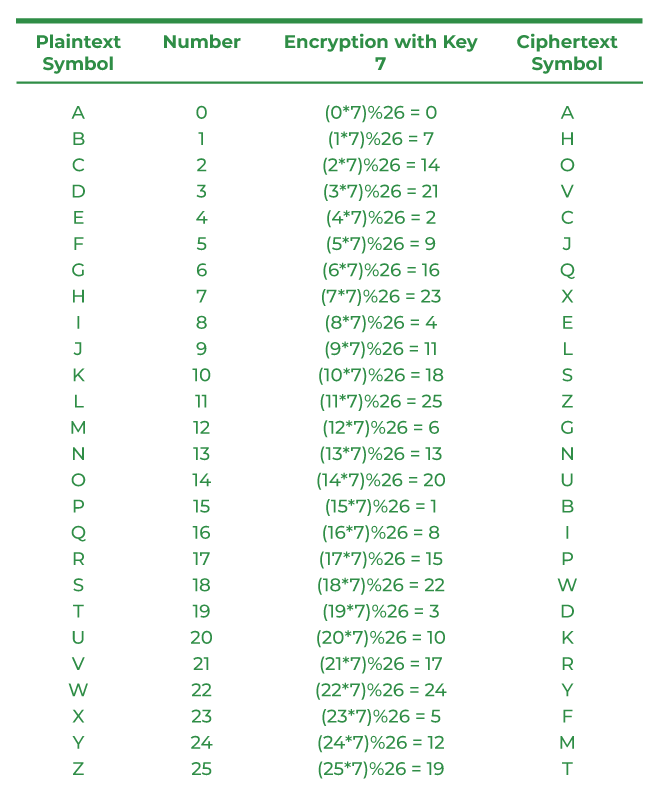
Step 2: First of all we will require an alphabet table with numeric values attached to each alphabet so that we can do the encryption process fastly. See the image attached below for a better understanding.

Numeric values for each alphabet
Step 3: Now, apply the formula which is mentioned above. So it will look like this after calculation.
Step 4: So, once the calculation part is done now you can easily encrypt your given plain text. So in our case, it was “GEEKSFORGEEKS”, so it will become:
Plain text = GEEKSFORGEEKS
Multiplicative Cipher text = QCCSWJUPQCCSW
Decryption
Let us consider the above cipher text i.e. “QCCSWJUPQCCSW” as an example to perform decryption using the multiplicative cipher.
Step 1: For decryption first we need to find the multiplication inverse of the key. So in our above example, the key is 7.
Multiplication inverse of 7 is 15
Step 2: The basic formula that can be used to implement Multiplicative Cipher is:
Decryption= (C * Multiplication inverse of the key) Mod 26
Here,
c = ciphertext
Mod = Modulo
Step 3: Let’s see how decryption can be done using the above formula:
Ciphertext = QCCSWJUPQCCSW and multiplication inverse key = 15
Ciphertext: Q –> 16 Decryption: (16*15) mod 26 Plaintext: 6 –> G
Ciphertext: C –> 2 Decryption: (2*15) mod 26 Plaintext: 4 –> E
Ciphertext: C –> 2 Decryption: (2*15) mod 26 Plaintext: 4 –> E
Ciphertext: S –> 18 Decryption: (18*15) mod 26 Plaintext: 10 –> K
Ciphertext: W –> 22 Decryption: (22*15) mod 26 Plaintext: 18 –> S
Ciphertext: J –> 9 Decryption: (9*15) mod 26 Plaintext: 5 –> F
Ciphertext: U –> 20 Decryption: (20*15) mod 26 Plaintext: 14 –> O
Ciphertext: P –> 15 Decryption: (15*15) mod 26 Plaintext: 17 –> R
Ciphertext: Q –> 16 Decryption: (16*15) mod 26 Plaintext: 6 –> G
Ciphertext: C –> 2 Decryption: (2*15) mod 26 Plaintext: 4 –> E
Ciphertext: C –> 2 Decryption: (2*15) mod 26 Plaintext: 4 –> E
Ciphertext: S –> 18 Decryption: (18*15) mod 26 Plaintext: 10 –> K
Ciphertext: W –> 22 Decryption: (22*15) mod 26 Plaintext: 18 –> S
Step 4: After Decryption
Ciphertext = QCCSWJUPQCCSW
After decryption the plain text = GEEKSFORGEEKS
In, this way you can implement Encrypt a plain text and Decrypt a cipher text for Multiplicative cipher in cryptography.
Example:
Let’s walk through a Python example of the Multiplicative Cipher with proper explanation and output:
Python
def encrypt(plain_text, key):
cipher_text = ""
for char in plain_text:
if char.isalpha():
# Convert to uppercase to have a consistent range
char = char.upper()
# Apply the multiplicative cipher formula
encrypted_char = chr(((ord(char) - ord('A')) * key) % 26 + ord('A'))
cipher_text += encrypted_char
else:
# If the character is not a letter, leave it unchanged
cipher_text += char
return cipher_text
def decrypt(cipher_text, key):
plain_text = ""
# Calculate the modular multiplicative inverse of the key
key_inverse = pow(key, -1, 26)
for char in cipher_text:
if char.isalpha():
char = char.upper()
# Apply the multiplicative cipher decryption formula
decrypted_char = chr(((ord(char) - ord('A')) * key_inverse) % 26 + ord('A'))
plain_text += decrypted_char
else:
plain_text += char
return plain_text
# Example
plain_text = "HELLO"
key = 7
# Encryption
cipher_text = encrypt(plain_text, key)
print("Encrypted:", cipher_text)
# Decryption
decrypted_text = decrypt(cipher_text, key)
print("Decrypted:", decrypted_text)
Explanation:
- The ‘encrypt‘ function takes a plaintext and a key as input and returns the encrypted ciphertext. It iterates through each character in the plaintext, applies the multiplicative cipher formula, and builds the ciphertext.
- The ‘decrypt‘ function takes a ciphertext and a key as input and returns the decrypted plaintext. It calculates the modular multiplicative inverse of the key and then applies the decryption formula to each character in the ciphertext.
- In the example, we use the plaintext “HELLO” and a key of 7. The encryption process produces the ciphertext, and the decryption process recovers the original plaintext.
- The modular multiplicative inverse is calculated using the ‘pow‘ function with the third argument as 26 (the size of the English alphabet). This ensures that the inverse exists in a modulo 26 arithmetic.
Output:
Encrypted: OLSSV
Decrypted: HELLO
In this example, the original message “HELLO” is encrypted to “OLSSV” using a multiplicative cipher with a key of 7. The decryption process successfully recovers the original message.
Criteria for Selecting a Key
- The key should be relatively prime to the length of the alphabet. That means the key should not have any common factors with the alphabet or plaintext except for 1. This is important because if the key shares a factor with the plaintext, it can be easily broken by factoring in the key.
- The key should not be easily guessable or should not be easily cracked. This means that the key should be a large, random number that is difficult to guess or factor.
- The key should be changed frequently to prevent cryptographic attacks. This is important because even if a key is secure when it is first chosen, it can become less secure over time as technology and methods for breaking encryption increase.
- The key should be kept secret and only shared with authorized parties. This is important because if the key is known by an unauthorized party, they will be able to decrypt the message.
Benefits of Multiplicative Cipher
- Efficiency: It is relatively efficient in terms of storage and computation, as it only requires a single multiplication operation per character of the plaintext.
- Simplicity: The multiplicative cipher is a simple encryption technique that is easy to implement and easy to understand. It does not require any large amount of computational power.
- Fast Speed: Since the encryption and decryption process is based on simple mathematical operations, it can perform quickly hence, making it suitable for applications that require high-speed encryption.
Limitations of Multiplicative Cipher
- Vulnerability to discover the key: The multiplicative cipher is probably vulnerable to key discovery attacks, especially when the key is a bit small or not sufficiently random.
- Limited security: The multiplicative cipher is not considered to be one of the secure methods of encryption, as it can be easily broken/cracked by simple mathematical operations.
- Lack of diffusion: It does not provide any diffusion, i.e. the same plaintext letter will always be mapped to the same ciphertext letter. Thus making it vulnerable to frequency analysis attacks, in this, the attacker can determine the key by analyzing the frequency of the letters in the ciphertext.
- Not suitable for modern encryption: The multiplicative cipher is not suitable for modern encryption because it does not provide the level of security required for the current communication systems.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...