What is Kerberos Authentication?
Last Updated :
27 Mar, 2023
Authentication is the process of verifying the identity of a user or information so that the receiver can ensure that the message has been sent from a genuine source or not.
Kerberos is a Network Authentication Protocol evolved at MIT, which uses an encryption technique called symmetric key encryption and a key distribution center. Although Kerberos is ubiquitous in the digital world, it is widely used in secure systems based on reliable testing and verification features. Kerberos is used in Posix authentication, as well as in Active Directory, NFS, and Samba. And it is another authentication system for SSH, POP, and SMTP.
Kerberos Protocol Flow:
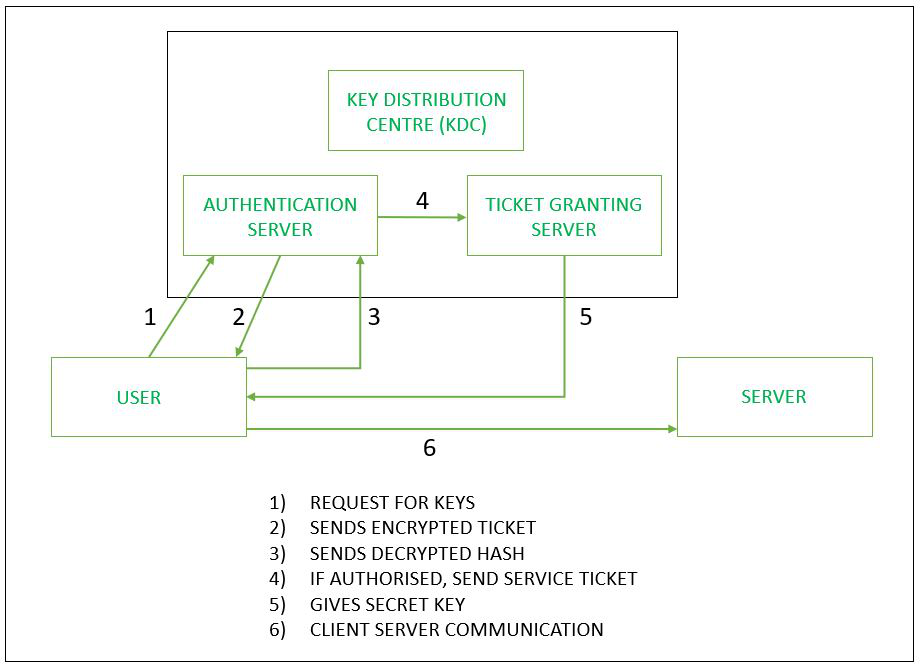
This works on the Client-Server based Model. Kerberos makes use of symmetric key cryptography and a key distribution center (KDC) to authenticate and verify consumer identities. The symmetric key used is the same for encryption and decryption. A KDC is a database of all the secret keys. A KDC entails 3 aspects:
- A ticket-granting server (TGS) that connects the consumer with the service server (SS).
- A Kerberos database that shops the password and identification of all tested users.
- An authentication server (AS) that plays the preliminary authentication.
Let’s say we have a user (Client) and We have a server(whose network services we require). The User must be an Authorised User.
- The user sends a message to KDC, requesting keys so that the user can prove its authenticity and access the services of the Network.
- Now AS (Authentication server) in KDC will send the ticket back to the User. The ticket will be in encrypted form.
- The user will decrypt the message and get the hash code.
- The hash code is again sent back to AS. Now AS will check for Authenticity.
- If the user is authorized, then AS gives a service ticket (Secret Key) to the Ticket Granting Server.
- TGS gives it to the User.
- Using this Ticket, the client communicates with a server.
Is Kerberos Infallible or not?
There is no 100% inaccessible level of protection, and Kerberos is. For a long time, hackers have had the opportunity over the years to find ways around you, often by making fake tickets, making repeated attempts to guess passwords (brute power/proof entry), and using a malicious computer program to reduce encryption. Apart from this, Kerberos is still the best security access protocol available today. The protocol is flexible enough to use robust encryption algorithms to help fight new threats, and when users make use of the right policies & guidelines for selecting the right passwords, there is not any problem.
Advantages of Kerberos:
- Access Control: The Kerberos authentication protocol permits powerful access control. Users advantage of a single point for track of all logins and the enforcement of protection policies.
- Mutual Authentication: Kerberos authentication permits carrier structures and customers to authenticate each other. During all steps of the process, the user and the server will understand that the counterparts that they may be interacting with are authentic.
- Limited Ticket Lifetime: Each ticket in Kerberos has timestamps and lifelong data, and the period of authentication is managed through admins.
- Reusable Authentication: Kerberos authentication is durable and reusable. Each user will effectively be tested through the system once.
- Security: Multiple secret keys, third-party authorization, and cryptography make Kerberos a secure verification protocol. Passwords are not sent over the networks, and secret keys are encrypted, making it hard for attackers to impersonate users or services.
- Performance: With respect to the Performance, Kerberos keeps track of client information after verification. This means it can do better than NTLM, especially on large farms. Also, Kerberos can transfer client information from an end-to-end webserver to other background servers such as SQL Server.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...