What is components with known Vulnerability ?
Last Updated :
08 Dec, 2021
In this article, we will discuss the overview of the components with known vulnerability and will discuss how to spot and will see how to use exploit-db.com for attack purposes, and finally concluded with prevention steps. Let’s discuss it one by one as follows.
Components with known vulnerabilities :
- These components can be defined as the third-party apps or software or platforms that are outdated and contain bugs that are public to all, that is- sites like https://www.exploit-db.com contain the full detail as to how to exploit the bugs to put the security of the whole website under severe threat.
- This vulnerability arises with the fact that a website finds it difficult to code everything while making its website functional like -transaction, location, chats, etc.
- So, in order to ease the process of building the website, many websites use third-party apps which do the tasks. But the main problem is that those apps can be harmful to their system if they are not updated regularly. Components with known vulnerabilities are considered to be one of the top 10 web application vulnerabilities listed by OWASP.
- Many websites security gets compromised when they use components having known vulnerabilities.
How to spot :
There are automated tools available online ex- drop scanner which display all the outdated components present in the software. These automated tools save time for security experts by directly pointing out flaws of the website.
Business impact :
When a website uses such outdated software, the hacker can misuse the flaws and get inside the database of the website and can cause serious damage to the website by stealing critical information.
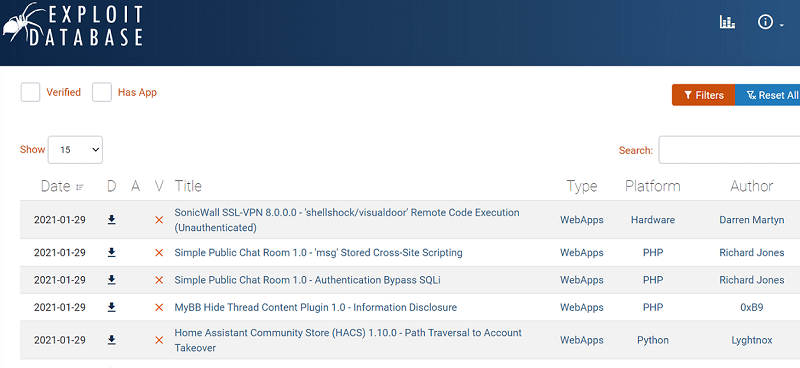
Use of exploit-db.com for attack purposes :
Step-1 :
The picture shown above contains a search option. Suppose we want to check if the current component is vulnerable to SQL vulnerability. Type “SQL injection” in the search space provided.
Step-2 :
All the software or components which suffered from SQL injection vulnerability will start getting displayed, as shown below.
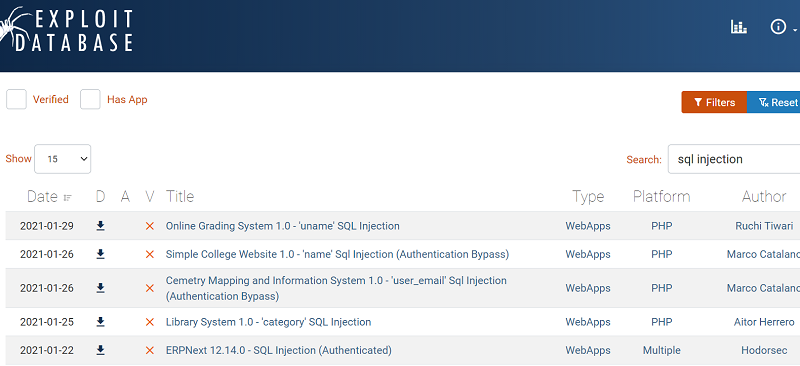
Step-3 :
Now, we simply have to search the component name with version to check if there exists any vulnerability to that particular component. Thus, one can exploit the web application easily.
Prevention Steps :
- Regular updates of the components of software will prevent this kind of attack.
- Also, if any threat is detected in any component, immediately isolate that module and release security patches for that.
- Implement regular monitoring and security assessment testing.
- You can check vulnerability assessment, and you can perform it periodically, and you can do penetration testing both internal and external to confirm the security of your application in depth.
- Remove unused dependencies, unnecessary features, components, files, etc.
- It is recommended to obtain components from official sources over secure links only to ensure security.
Share your thoughts in the comments
Please Login to comment...