WarDriving – Introduction
Last Updated :
03 Aug, 2022
Wireless Networks have brought a lot of convenience to our lives, allowing us to work or surf from almost anywhere- home, theaters, airports, hotels around the globe. Unfortunately, wireless networks have also brought convenience to hackers as it gives the opportunity to capture all data that we type in our computers or any connected devices through the air, and they can even gain control of them. We call this act of cruising for unsecured wireless networks “War Driving”.
What is War Driving?
War Driving originated from wardialing, a method popularized from the movie WarGames and named after that film. Term War Driving was coined by Computer Security Consultant Peter Shipley. Wardialing involves dialling every phone number in a specific sequence in search of modems. WarDriving, knew as Access Point Mapping, is the act of searching WiFi wireless networks usually in a moving vehicle using a smartphone or laptop.
Wardrivers who are successful in gaining access to your network may be interested in stealing your credentials, banking information, or any other sensitive information. They may simply use the entry into your network to install the malware that can use your device for purposes that are not under your control.
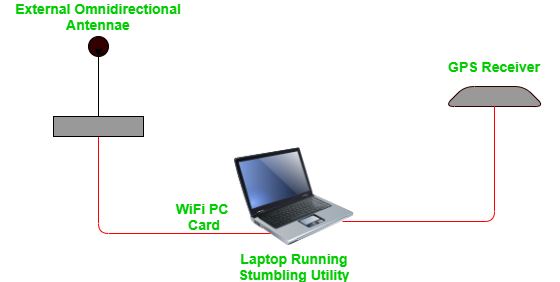
Hardware and Software Tools for WarDriving
All hardware and software components that are used while wardriving are collectively known as Rig. There is no hard and fast rule regarding what types of devices or software are used by your friendly wardriver neighbor. But in order to perform successful Wi-Fi driving, you need to use some specialized hardware and software. Let’s take a look at some tools:
1. Hardware Tools for WarDriving:
There are several hardware tools are required to perform Wardriving.
- A mobile device: This is a basic prerequisite for performing wardriving. You need a mobile computing platform like laptops, tablets, smartphones, or any other device like Raspberry Pi. These are used to subvert encryption and manage the overall process.
- Wireless network card antenna: This is the most critical component of a wardriving setup. Wardrivers may opt to use a built-in antenna and card, or they can go for additional hardware to increase the scanning power of the device.
- GPS System: The GPS system is used to determine the exact location of the Wi-Fi router that has been located. Many of the wardriving devices have built-in GPS capabilities.
2. Software Tools for Wardriving:
The primary piece of software which will be used in wardriving is an application that will be used to crack the passwords of WEP and WPA encrypted networks. There is another category of applications that are used to generate maps of the network neighborhood. There are many such software applications are available for use depending upon the operating system you prefer. This certainly not an exhaustive list of all software applications that can be used to hack a Wi-Fi network, but it will definitely give you an idea of the types of tools that are available.
Here are a few popular applications that are used by wardrivers:
Applications for generating maps:
These are the websites that are used to generate the map of network neighborhoods based on the data uploaded to the website.
- WiGLE: WiGLE is Wireless Geographic Logging Engine is a website where users can upload hotspot data like GPS coordinates, SSID, MAC Address to discover the encryption type that is used on the hotspot.
- openBmap: It is a free and open map of the wireless communicating objects like Bluetooth, Wi-Fi, cellular antennae. It provides tools to mutualize data, create and access this map.
- Geomena: It is an open geodatabase of Wi-Fi access points that are meant to be used for geolocation. The API provides a way to add data programmatically.
Tools for cracking WEP and WPA Keys:
Here is the list of few popular tools:
- MacStumbler: MacStumbler is a prominently used wireless network scanner for Mac OS X. It consists of the following features:
- Active Scanning for wireless access points.
- Log details of access points to a plain text file
- NetStumbler: It is the easiest to set up and the most popular scanner used on the Windows Platform. It emits 802.11b probes that ask wireless access points to respond if they are nearby. It has the following features:
- Active scanning for wireless access points.
- GPS Support.
- Logs access points to NS1, extended and summary Wi-Fi scan, and plain text files.
- KisMAC: This is available for the Mac platform only. This tool scans the network passively and uses a brute-force attack to crack WEP and WPA Keys.
- Aircrack: This is a very popular tool for wireless password cracking that is used worldwide. It has the following features:
- It can run on different platforms like OS X, Windows, Linux.
- It is optimized for WEP password attacks.
- It captures and analyzes data packets in an attempt to recover passwords.
- CoWPatty: This tools run on the Linux platform only and is an automated tool to execute dictionary attacks to crack WPS encrypted passwords. It only provides a command-line interface and is slower than other tools available in the market.
- WiFiphisher: This tool is available for Windows, Linux, and Mac. As the name suggests this tool performs fast automated phishing attacks on wireless networks in an attempt to steal passwords.
- Cain & Able: It works by intercepting network traffic and then uses a brute-force attack to discover the passwords.
Protecting your network from Wardrivers
The overriding factor that makes a wireless network attractive to a wardriver is the lack of adequate security. A network that is securely protected will be impervious to these types of attacks or at least it will be difficult to access that the attackers will find another, more easily compromised target.
- Change router’s administrative password: The default password for many routers is easily available on the Internet. So it is advisable to change the credentials before start using the router to make it less susceptible to attack.
- Use a Firewall: A firewall is responsible for monitoring the access to your network and will allow access only from the approved sources. Thus, it will help to some extent to stop unauthorized users from gaining access to your network.
- Enable Encryption: It is advisable to use routers that enable you to set WPA and WPA2 encryption. It is best to avoid WEP encryption as it can be cracked easily using the tools mentioned above.
- Shutdown wireless router when not in use: If you are out somewhere or will not be using the network for an extended period of time, just shut it down.
- Don’t broadcast your SSID: If you configure your router to not broadcast your SSID, then it will be difficult to detect. Even if you are not broadcasting your SSID, it can be guessed. Due to this, remember to change your SSID from factory default.
These are the best practices that can help you to secure your network from any type of unauthorized attacks. Encryption should be the topmost priority, it is the first line of defense. Secure your networks and devices using the highest level of encryption available on your router and device being used.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...