What is the full form of VPN?
Last Updated :
07 Feb, 2024
Answer: VPN stands for Virtual Private Network.
It basically encrypts the connection and makes the user’s IP address hidden by using various tunneling protocols. It is used to bypass geo-blocks and for security purposes. It is secure and private means for file sharing, communication and remotely accessing data without any risk of a hack.

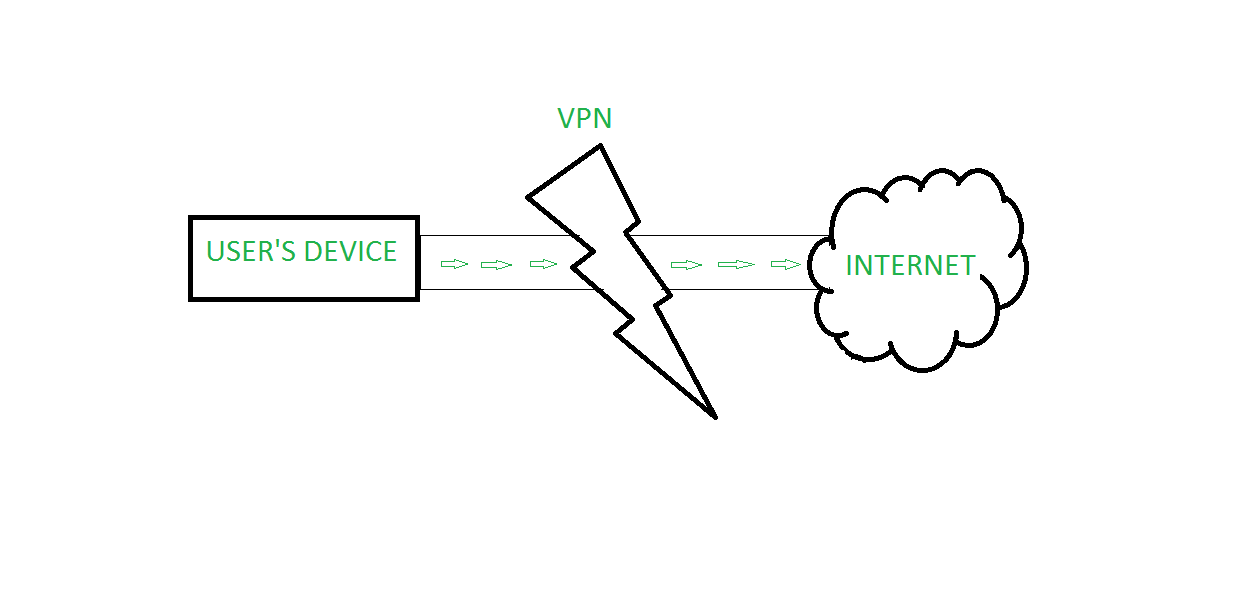
VPN tunneling ensures encryption at the user’s end and decryption at the receiver’s end, for this to happen the device should be connected to a VPN client software application.VPN acts as an intermediator between user and connection to the internet. It hides user IP address and makes a connection from VPN’s private network rather than the user’s ISP(Internet Service Provider).
History of VPN
In 1996 a Microsoft’s employee started working on Peer to Peer Tunnelling Protocol(PPTP) from where the idea of VPN originated. In 1999 the first VPN was published.
Characteristics of VPN
- It maintains confidentiality of user’s data.
- It maintains the integrity of the user’s data that is the data cannot be changed in between the transmission.
- It ensures non-repudiation that is a sender cannot deny that he/she had not sent the data.
- Data authentication is also ensured by VPN, it verifies the source and destination’s authenticity.
VPN protocols
It ensure an appropriate level of security with connected systems when the underlying network infrastructure can not provide it alone. To secure and encrypt, several different protocols can be used:
- IP Security (IPsec)
- Point-to-Point Tunneling Protocol (PPTP)
- Secure Sockets Layer (SSL) and Transport Layer Security (TLS)
- Layer 2 Tunnel Protocol (L2TP)
- OpenVPN
Working Principle of VPN
- The working principle of a VPN involves creating a secure and encrypted connection between the user’s device and a VPN server. This connection is created using a combination of encryption protocols and network protocols.
- When a user connects to a VPN, their device sends a request to the VPN server to establish a secure connection. The VPN server responds by sending the user’s device a set of encryption keys, which are used to encrypt all data that is transmitted between the device and the VPN server.
- Once the connection has been established, all data that is transmitted between the user’s device and the VPN server is encrypted using the encryption keys. This means that even if a hacker intercepts the data, they will not be able to read it.
- In addition to encryption, a VPN also uses network protocols to ensure that the data is transmitted securely. The most common network protocol used by VPNs is the Internet Protocol Security (IPsec) protocol. IPsec provides a set of security protocols that ensure the integrity, confidentiality, and authenticity of the data that is transmitted over the internet.
Advantages of VPN
- Improved Security: A VPN encrypts all data that is transmitted between the user’s device and the VPN server. This means that even if a hacker intercepts the data, they will not be able to read it.
- Privacy: A VPN masks the user’s IP address, making it difficult for websites and online services to track their online activity.
- Access to Restricted Content: Some websites and online services are restricted in certain countries. By using a VPN, users can connect to a server in another country and access the content that is restricted in their own country.
- Anonymity: By masking the user’s IP address and encrypting their data, a VPN provides a high level of anonymity online.
Disadvantages of VPN
- The time taken to fetch the data sometimes increases when fetched through VPN, so there might be a performance issue with respect to time.
- VPN allows you to hide your identity but sometimes your VPN provider company itself steals your data, which can cause security issues.
- Whenever VPN disconnection occurs there is a possibility of IP address get revealed to the network from which connection was made.
- It is always not possible to bypass restrictions applied by a website by using a VPN.
Types of VPN
There are mainly two types of VPN. They are –
- Remote Access VPN: A remote access VPN allows users to connect to a private network from a remote location. This type of VPN is often used by employees who need to access company resources from a remote location.
- Site-to-Site VPN: A site-to-site VPN connects two or more networks together over the internet. This type of VPN is often used by companies with multiple locations.
- Client-to-Site VPN: A client-to-site VPN allows individual users to connect to a private network from a remote location. This type of VPN is often used by individuals who need to access their home network from a remote location.
VPN Privacy
A VPN can hide a lot of information that can put your privacy at risk. Here are five of them.
- Your browsing history
- Your location for streaming
- Your IP address and location
- Your devices
- Your web activity — to maintain internet freedom
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...