Types of Node Devices in a Computer Network: End devices and Intermediary Devices
Last Updated :
03 Apr, 2023
Pre-Requisite: Physical Components of Computer Network
The computer network is a term used to refer to any group (or system) of interconnected nodes (computers, printers, or any other devices) connected by communication links known as transmission media (or channels) usually meant for the exchange of information and resource sharing.
What is Node in Computer Networks?
In Computer Networks, a Node is any device that is capable of sending or receiving data, to and from other nodes at definite and desired flow rates securely and reliably. In simple words, you can say that Nodes are the connection point among network devices that results in the transfer of data from one point to another. In a Network, more than one node can be used at one time.
On the basis of functionality and usage, the node devices can be broadly classified into the following types:
- End Devices
- Intermediary Devices
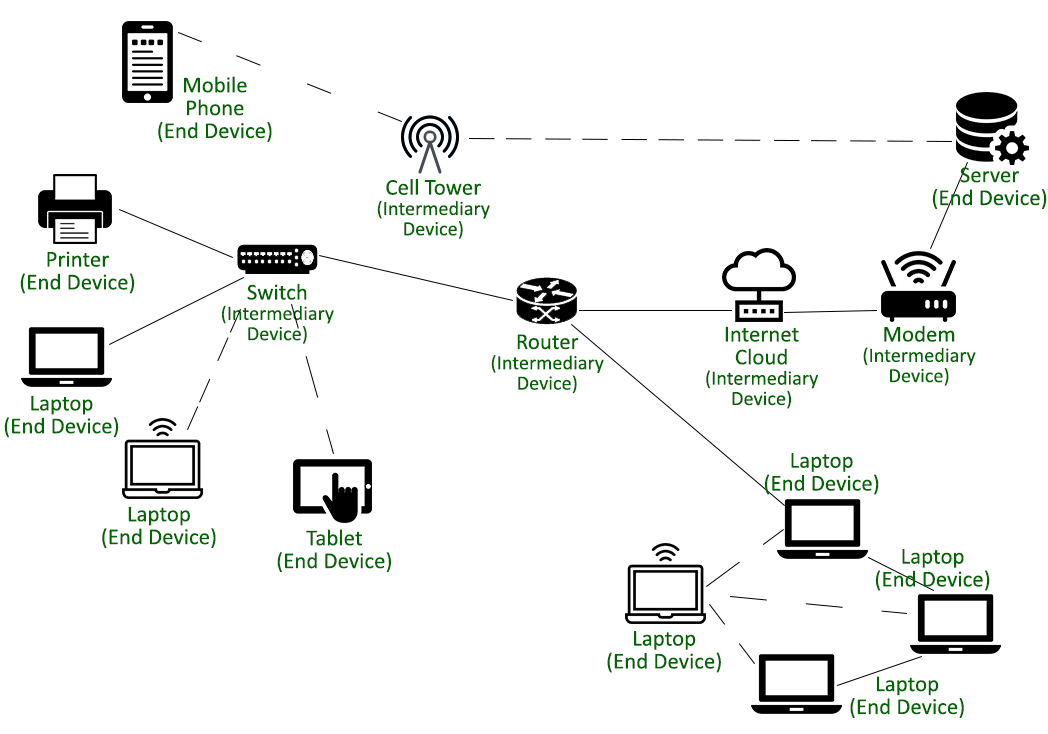
End Devices and Intermediary Devices
1. End Devices
End devices are node devices that serve as a source point or a destination point in the communication that occurs on a computer network. With the coming advancements in computer networking systems, we have nodes that can act as a client, a server, or both. The rest of the network is built around these end devices to establish communication links between them. Software installed on the node devices determines the role they offer to play in a computer network. According to their usage, the end devices can be broadly grouped into the following categories:
- End Devices as Clients: Perform the tasks of requesting data, displaying received data, etc. meant usually for usage by end clients.
- End Devices as Servers: Equipped with programs that provide information and services such as webpages or e-mails to other nodes (or hosts) on the network.
Functions of End Devices
- They serve as the originator of the data or information that flows through the network.
- Act as an interface between end-users (humans) and the communication network having several node devices.
Examples of the End Devices
Some examples of End Devices are Work Stations, Laptops, Desktop Computers, Printers and Scanners, Servers (File Servers, Web Servers), Mobile Phones, Tablets, Smart Phones, etc.
2. Intermediary Devices
Intermediary devices are node devices that are designed to forward data from one side to another side in a computer network. These intermediary devices work as a connecting medium (along with other services being offered) for other nodes and handle the tasks in the background ensuring that the data flows effectively at desired flow rates across the entire computer network.
The intermediary devices for the management of the data flowing through them use various addressing systems such as IP Addresses, MAC Addresses, and Port Numbers (or Port addresses) along with information about the network interconnections. Further various types of switching in computer networks determine the path that messages take through the network during communication.
Functions of Intermediary Devices
- Signal damping is a common phenomenon that is overcome via the regeneration and retransmission of the data signals done by these devices.
- To ensure successful transfers these devices keep a record of information on the source address, destination address, or different pathways existing through the network depending upon the switching technique being employed.
- They also detect faults and errors effectively using redundancy bits, etc. and notify the devices to further ensure fault tolerance by performing corrections while transferring data in a computer network.
- Maintenance of a definitely desired flow control and response timeout during the entire course of the communication.
- Setup, grouping, and direction of messages (or packets) according to their priorities are done by these devices.
- Provide network security by permitting or denying the flow of data, based on security settings.
Examples of the intermediary devices
Some examples of Intermediary Devices are Hubs, Switches, wireless access points, and other devices used for accessing the network, file servers, web servers, print servers, modems, and devices used for internetworking such as routers, bridges, repeaters, security firewalls, etc.
Some Other Nodes in Computer Network
- Data Communications
- Telecommunication Nodes
- Cable TV Network Nodes
- Distributed Network Nodes
- LANs & WANs
1. Data Communications: Data Communication is defined as the exchange of data between two devices via some form of transmission media such as a cable, wire or it can be air, or vacuum also. For the occurrence of data communication, communicating devices must be part of a communication system made up of a combination of hardware or software devices and programs.
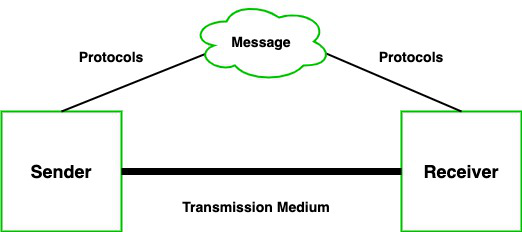
Data Communications
2. Telecommunication Nodes: Telecommunication Nodes are the nodes connected in the telephone networks which might be used privately or publicly to communicate with one another.
3. Cable TV Network Nodes: Nodes in cable TV Network Devices basically deals with the Fibre Optics cables, which are connected in homes and business areas.
4. Distributed Network Devices: Distributed network nodes are the nodes that are distributed among servers and clients.
5. LANs & WANs: LAN & WAN are used to perform actions. Here, for every Network Interface Card, we require a MAC Address.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...