Tunneling
Last Updated :
13 Apr, 2023
A technique of inter-networking called Tunneling is used when source and destination networks of the same type are to be connected through a network of different types. Tunneling uses a layered protocol model such as those of the OSI or TCP/IP protocol suite.
So, in other words, when data moves from host A to B it covers all the different levels of the specified protocol (OSI, TCP/IP, etc.) while moving between different levels, data conversion (Encapsulation) to suit different interfaces of the particular layer is called tunneling.
For example, let us consider an Ethernet to be connected to another Ethernet through a WAN as:

Tunneling
The task is sent on an IP packet from host A of Ethernet-1 to host B of Ethernet-2 via a WAN.
Steps
- Host A constructs a packet that contains the IP address of Host B.
- It then inserts this IP packet into an Ethernet frame and this frame is addressed to the multiprotocol router M1
- Host A then puts this frame on Ethernet.
- When M1 receives this frame, it removes the IP packet, inserts it in the payload packet of the WAN network layer packet, and addresses the WAN packet to M2. The multiprotocol router M2 removes the IP packet and sends it to host B in an Ethernet frame.
How Does Encapsulation Work?
Data travels from one place to another in the form of packets, and a packet has two parts, the first one is the header which consists of the destination address and the working protocol and the second thing is its contents.
In simple terminology, Encapsulation is the process of adding a new packet within the existing packet or a packet inside a packet. In an encapsulated packet, the header part of the first packet is remain surrounded by the payload section of the surrounding packet, which has actual contents.
Why is this Technique Called Tunneling?
In this particular example, the IP packet does not have to deal with WAN, and the host’s A and B also do not have to deal with the WAN. The multiprotocol routers M1 and M2 will have to understand IP and WAN packets. Therefore, the WAN can be imagined to be equivalent to a big tunnel extending between multiprotocol routers M1 and M2 and the technique is called Tunneling.
Types of Tunneling Protocols
- Generic Routing Encapsulation
- Internet Protocol Security
- Ip-in-IP
- SSH
- Point-to-Point Tunneling Protocol
- Secure Socket Tunneling Protocol
- Layer 2 Tunneling Protocol
- Virtual Extensible Local Area Network
1. Generic Routing Encapsulation (GRE)
Generic Routing Encapsulation is a method of encapsulation of IP packets in a GRE header that hides the original IP packet. Also, a new header named delivery header is added above the GRE header which contains the new source and destination address.
GRE header act as a new IP header with a Delivery header containing a new source and destination address. Only routers between which GRE is configured can decrypt and encrypt the GRE header. The original IP packet enters a router, travels in encrypted form, and emerges out of another GRE-configured router as the original IP packet as they have traveled through a tunnel. Hence, this process is called GRE tunneling.
2. Internet Protocol Security (IPsec)
IP security (IPSec) is an Internet Engineering Task Force (IETF) standard suite of protocols between 2 communication points across the IP network that provide data authentication, integrity, and confidentiality. It also defines the encrypted, decrypted, and authenticated packets. The protocols needed for secure key exchange and key management are defined in it.
3. IP-in-IP
IP-in-IP is a Tunneling Protocol for encapsulating IP packets inside another IP packet.
4. Secure Shell (SSH)
SSH(Secure Shell) is an access credential that is used in the SSH Protocol. In other words, it is a cryptographic network protocol that is used for transferring encrypted data over the network. It allows you to connect to a server, or multiple servers, without having to remember or enter your password for each system which is to log in remotely from one system to another.
5. Point-to-Point Tunneling Protocol (PPTP)
PPTP or Point-to-Point Tunneling Protocol generates a tunnel and confines the data packet. Point-to-Point Protocol (PPP) is used to encrypt the data between the connection. PPTP is one of the most widely used VPN protocols and has been in use since the early release of Windows. PPTP is also used on Mac and Linux apart from Windows.
.png)
Point-to-Point Tunneling Protocol (PPTP)
6. Secure Socket Tunneling Protocol (SSTP)
A VPN protocol developed by Microsoft that uses SSL to secure the connection, but only available for Windows.
7. Layer 2 Tunneling Protocol (L2TP)
L2TP stands for Layer 2 Tunneling Protocol, published in 2000 as proposed standard RFC 2661. It is a computer networking protocol that was designed to support VPN connections used by an Internet service provider (ISP) to enable VPN operation over the Internet. L2TP combines the best features of two other tunneling protocols- PPTP(Point-to-Point Tunneling Protocol) from Microsoft and L2F(Layer 2 Forwarding) from Cisco Systems.
8. Virtual Extensible Local Area Network (VXLAN)
Virtual Extensible Local Area Network is short called VXLAN. It is a network virtualization technology that stretches layer 2 connections over layer 3 networks by encapsulating Ethernet frames in a VXLAN packet which includes IP addresses to address the scalability problem in a more extensible manner.
What is SSL Tunneling?
SSL Tunneling involves a client that requires an SSL connection to a backend service or secures a server via a proxy server. This proxy server opens the connection between the client and the backend service and copies the data to both sides without any direct interference in the SSL connection.
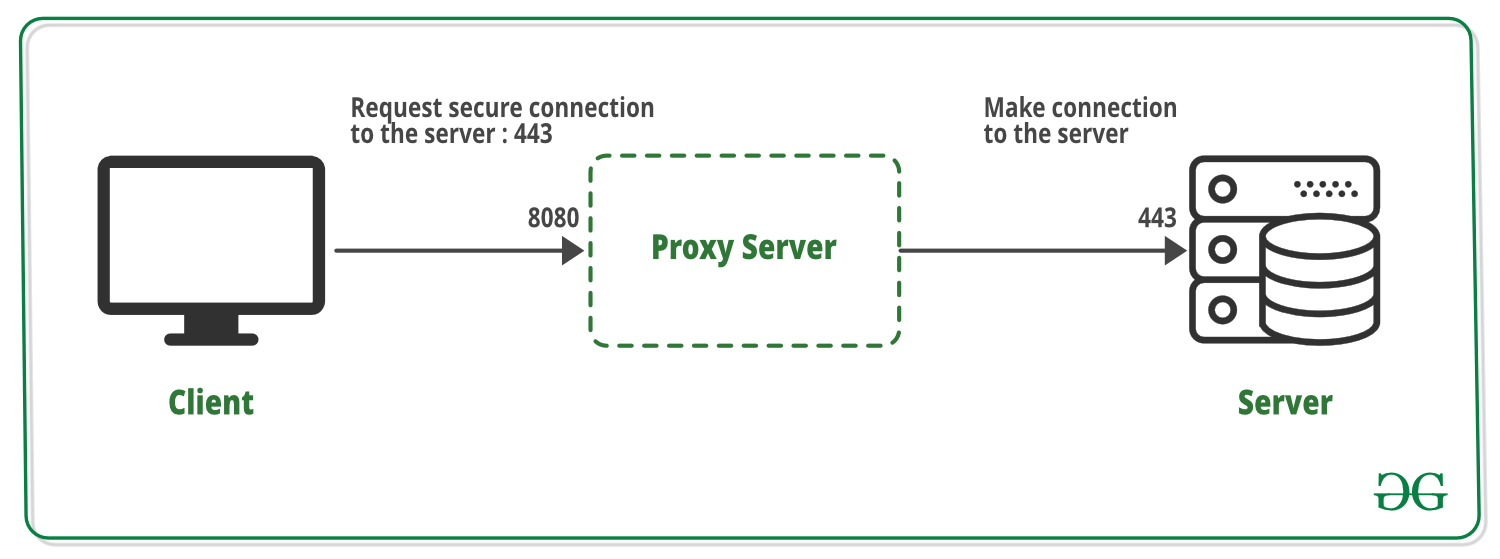
SSL Tunneling
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...