The year is 2024. Our reliance on technology has reached unprecedented heights, but so have the dangers lurking in the digital shadows. Cybercrime is evolving at breakneck speed, leaving individuals and organizations exposed to an ever-widening array of threats. This article serves as a stark wake-up call, unveiling the Top 10 Cyber Security Threats currently wreaking havoc across the globe.

Cyber Security Threats World is Facing
Ransomware, phishing attacks, malware attacks, and other cybersecurity threats are some examples. One of the fastest-growing areas is cybersecurity nowadays. The need for data protection is being recognized by more individuals than ever before. Businesses, in particular, are paying attention, as data breaches cost billions of dollars each year and expose vast amounts of personal information.
As of August 2020, it was estimated that there have been over 445 million cyberattacks worldwide this year, more than double the total for the full year of 2019. While many of these attacks were thought to be driven by our increased use of the Internet as a result of the coronavirus pandemic and lockdowns, the threat to businesses remains significant, with the cost of cybercrime expected to reach $10.5 trillion by 2025(According to Cybersecurity Ventures). The threats posed by cyber thieves will only increase as organizations become more dependent on the Internet and technology.
What is the definition of a Cyber Threat?
A cyber threat can be defined as any activity, deliberate or unintentional, that has the potential to harm an automated information system or activity. In simpler terms, it’s anything that could put your computer systems, networks, and data at risk.
Here are some key points to remember about cyber threats:
- They can be intentional or unintentional: This means they can be caused by malicious actors like hackers or criminals, but also by accidental mistakes or even natural disasters.
- They can target many things: From individual devices to entire networks and critical infrastructure, cyber threats can have wide-ranging targets and impacts.
- They can have various goals: From stealing data or disrupting operations to causing financial losses or even physical harm, cyber threats can have diverse motivations.
Sensitive data has been exposed as a result of several high-profile cyberattacks in recent years.
For example, the 2017 Equifax data breach exposed the personal information of more than 143 million people, including dates of birth, residence, and Social Security numbers. Marriott International revealed in 2018 that hackers gained access to its systems and stole the personal information of nearly 500 million customers. The inability to establish, test, and retest technical security measures, including encryption, authentication, and firewalls, allowed a cybersecurity threat in both situations.
Cyber attackers can exploit sensitive data to steal information or gain access to a person’s or company’s bank accounts, among other potentially destructive activities, which is why cybersecurity experts are so critical of keeping private data secure.
Today’s Top CyberSecurity Threats
Many small business owners feel that their firm is too small or that their business is modest enough not to be targeted for attack, but this is far from the case. Small companies often take a careless approach to Internet security, resulting in inadequate security and leaving them vulnerable to attacks. Hackers are using increasingly sophisticated and automated tactics, allowing them to attack thousands of small company websites at once.
Certainly! Let’s delve into the Top 10 Cyber Threats that the world is facing with in 2024. These threats pose significant challenges to organizations, individuals, and global security:
1. Ransomware

Cyber Security Threats World – Ransomware
Ransomware attacks continue to plague businesses and governments alike. The concept is simple: attackers encrypt your data and demand a ransom for its release. High-profile incidents like the Colonial Pipeline attack, where a hefty ransom was paid, underscore the severity of this threat.
Ransomware is a type of malicious software designed to encrypt a victim’s data, rendering it inaccessible. Attackers then demand a ransom payment in exchange for providing the decryption key. This effectively holds the victim’s data hostage, creating a high-pressure situation often resulting in significant financial losses.
Modus Operandi:
Ransomware attacks can occur through various means, including:
- Phishing emails: Deceptive emails containing malicious attachments or links that, when clicked, download and install the ransomware on the victim’s device.
- Exploiting software vulnerabilities: Attackers leverage unpatched vulnerabilities in software or operating systems to gain unauthorized access and deploy ransomware.
- Supply chain attacks: Malicious code is injected into legitimate software or updates during the development or distribution process, impacting unsuspecting end users.
Impact:
Ransomware attacks can have devastating consequences for individuals and organizations alike. Some potential impacts include:
- Data loss: Encrypted data becomes unusable, potentially leading to permanent data loss if backups are unavailable or compromised.
- Financial losses: Ransom payments can be substantial, ranging from hundreds to millions of dollars depending on the target and attacker’s demands.
- Operational disruptions: Business operations can be severely disrupted, leading to lost productivity, revenue, and customer trust.
- Reputational damage: Organizations that suffer ransomware attacks can face significant reputational damage due to data breaches and service disruptions.
Defense Strategies :
- Regular software updates: Keeping software and operating systems up-to-date with the latest security patches helps address known vulnerabilities.
- Employee awareness training: Educating employees about phishing scams and other social engineering tactics can significantly reduce the risk of successful attacks.
- Data backups: Regularly backing up critical data ensures recovery options in case of ransomware infection.
- Cybersecurity solutions: Implementing robust cybersecurity solutions, including firewalls, intrusion detection systems, and endpoint protection, can help detect and prevent ransomware attacks.
2. Misconfigurations and Unpatched Systems
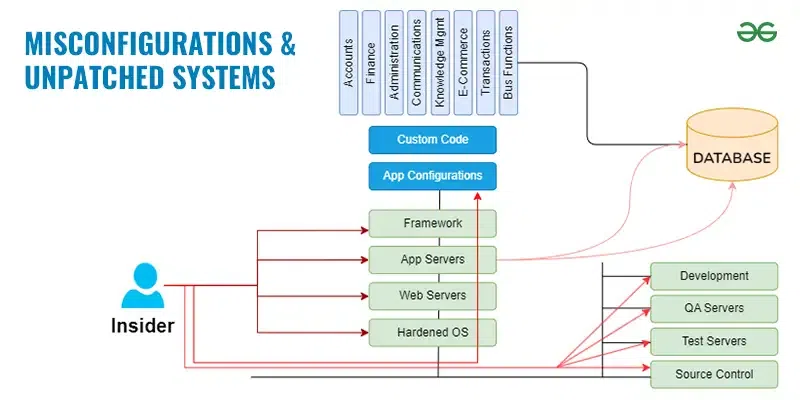
Cyber Security Threats World – Misconfigurations and Unpatched Systems
Neglecting system updates and misconfigurations can leave vulnerabilities wide open. Cybercriminals exploit these weaknesses to gain unauthorized access or disrupt services.
In the ever-evolving landscape of cybersecurity, two critical vulnerabilities remain prevalent: misconfigurations and unpatched systems. These seemingly minor oversights can create significant security gaps, acting as open doors for cybercriminals to exploit and launch devastating attacks.
Misconfigurations: Loose Locks on the Digital Gate
Misconfigurations occur when security settings are not implemented correctly or deployed with errors, leaving systems and applications susceptible to attack. This can happen at various levels, including:
- Operating systems: Incorrectly configured firewalls, open ports, or disabled security features can expose sensitive data and systems.
- Applications: Default configurations with weak passwords or disabled security features can be easily exploited.
- Network devices: Misconfigured routers, switches, and other network devices can create vulnerabilities that allow attackers to gain unauthorized access to the network.
- Cloud environments: Complex cloud configurations with mismanaged access controls or insecure storage settings can be vulnerable to data breaches.
These misconfigurations, like unlocked doors or forgotten keys, provide easy entry points for attackers, enabling them to steal data, disrupt operations, or launch further attacks.
Unpatched Systems: Outdated Software with Exposed Weaknesses
Unpatched systems refer to software or operating systems that lack the latest security updates, leaving them vulnerable to known and newly discovered vulnerabilities. These vulnerabilities are like cracks in the foundation of a building, waiting to be exploited by attackers with readily available tools and knowledge.
Attackers constantly scan for unpatched systems, exploiting these vulnerabilities to gain access, install malware, or launch other malicious activities. The consequences can be severe, including:
- Data breaches: Attackers can exploit vulnerabilities to steal sensitive data like personal information, financial records, or intellectual property.
- Ransomware attacks: Unpatched systems are prime targets for ransomware attacks, where attackers encrypt data and demand ransom for its decryption.
- Malware infections: Unpatched systems are susceptible to malware infections that can steal data, disrupt operations, or even damage hardware.
By neglecting to patch software vulnerabilities, organizations and individuals create opportunities for attackers to exploit these weaknesses, potentially causing significant harm.
Defense Strategies :
- Regular security audits: Regularly assess systems and applications for misconfigurations and identify potential vulnerabilities.
- Patch management: Implement a robust patch management system to ensure timely application of security updates for all software and operating systems.
- Security awareness training: Educate employees about the risks of misconfigurations and the importance of secure practices.
- Strong security controls: Implement strong security controls such as firewalls, intrusion detection systems, and access controls to further protect systems and data.
3. Credential Stuffing

Cyber Security Threats World – Credential Stuffing
Attackers use stolen credentials (often from previous data breaches) to gain unauthorized access to accounts. Weak or reused passwords are a prime target.
In the realm of cyber threats, credential stuffing emerges as a stealthy attack method that leverages stolen username and password combinations to gain unauthorized access to multiple accounts. Imagine a thief trying countless keys on different doors; credential stuffing operates similarly, attempting stolen login details across various platforms.
Modus Operandi:
- Data Breaches: Attackers acquire username and password combinations through data breaches on various websites or services. These breaches can expose millions of user credentials, forming the attacker’s ammunition.
- Automated Attacks: Utilizing sophisticated tools, attackers bombard login pages with stolen credential pairs, attempting to gain access to accounts on different platforms. These tools can test thousands of combinations per second, significantly increasing the attack’s reach.
- Weak Passwords and Reuse: The success of credential stuffing hinges on weak passwords and password reuse across different accounts. If the same login details are used on multiple platforms, a successful attack on one grants access to others, multiplying the impact.
Impact:
The consequences of credential stuffing can be far-reaching:
- Account Takeovers: Attackers gain access to email accounts, banking portals, social media profiles, and more, potentially leading to financial losses, identity theft, and reputational damage.
- Data Breaches: Compromised accounts can be used to launch further attacks, steal sensitive data, or even spread malware, creating cascading security issues.
- Reputational Damage: Organizations experiencing credential stuffing attacks face a loss of trust from their users, impacting brand image and customer loyalty.
Defense Strategies :
- Strong Password Practices: Enforce strong password policies, encouraging users to create unique and complex passwords for each account.
- Multi-Factor Authentication (MFA): Implement MFA as an additional layer of security, requiring a second verification step beyond just username and password.
- Regular Password Updates: Encourage users to update their passwords regularly, especially after major data breaches or suspicious activity.
- Data Breach Monitoring: Monitor for data breaches that might expose user credentials and promptly notify affected users to change their passwords.
- Security Awareness Training: Educate users about credential stuffing and phishing tactics to help them identify and avoid suspicious login attempts.
Also Read : Ethical Hacking and Cyber Security Fundamentals
4. Social Engineering
Human manipulation remains a potent weapon. Phishing emails, pretexting, and baiting lure victims into revealing sensitive information or performing actions that compromise security.

Cyber Security Threats World – Social Engineering
Social engineering, in the context of cyber threats, refers to a malicious practice that exploits human trust, emotions, and vulnerabilities to manipulate victims into divulging sensitive information or granting unauthorized access to systems and data. Think of it as a con artist’s digital playbook, where attackers leverage psychological tactics to trick their targets rather than relying solely on technical exploits.
Modus Operandi:
Social engineering attacks typically follow a well-defined structure:
- Target Selection: Attackers carefully choose their victims, often targeting individuals with access to valuable data or systems, based on information gathered through social media, phishing emails, or other means.
- Relationship Building: Attackers attempt to build rapport with their targets, posing as legitimate figures like customer support representatives, IT personnel, or even friends or colleagues.
- Manipulation and Deception: Utilizing various tactics like urgency, fear, or appeals to trust, attackers manipulate their targets into providing confidential information, clicking on malicious links, or installing malware.
Common Tactics:
Social engineering attacks can employ a diverse range of tactics, including:
- Phishing emails: Deceptive emails designed to appear legitimate, often impersonating trusted institutions or individuals, to trick recipients into clicking on malicious links or attachments.
- Smishing and vishing: Similar tactics using text messages (smishing) or phone calls (vishing) to deceive victims into sharing information or clicking on harmful links.
- Pretexting: Fabricating a scenario or impersonating a trusted entity to gain access to restricted information or systems.
- Tailgating: Physically following authorized individuals into secure areas to gain unauthorized access.
- Baiting: Leaving attractive-looking but harmful digital items (e.g., USB drives) to entice victims into downloading malware.
Impact:
Social engineering attacks can have severe consequences, including:
- Data breaches: Attackers can gain access to sensitive data like financial records, personal information, or intellectual property.
- Financial losses: Victims may be tricked into transferring money or making fraudulent purchases.
- System disruptions: Malware installed through social engineering can disrupt operations and cause significant downtime.
- Reputational damage: Organizations that fall victim to social engineering attacks can suffer reputational damage and loss of trust from their customers and partners.
Defense Strategies:
- Security awareness training: Educating employees and individuals about common social engineering tactics can significantly reduce the risk of falling victim.
- Verification: Always verify the legitimacy of requests, even if they appear to come from trusted sources. Do not click on suspicious links or attachments.
- Strong passwords and data protection: Utilize strong passwords and avoid sharing sensitive information unless absolutely necessary and through secure channels.
- Multi-factor authentication: Implement MFA as an additional security layer to make unauthorized access more difficult.
- Security protocols: Establish clear security protocols for handling sensitive data and accessing systems.
5. Phishing Attacks

Cyber Security Threats World – Phishing Attacks
Phishing attacks, a prevalent tactic in the cyber threat landscape, aim to lure victims into revealing sensitive information or clicking on malicious links through deceptive emails or messages. Imagine a cybercriminal casting a digital lure, disguising it as a trustworthy entity, to bait unsuspecting individuals into compromising their data security.
Modus Operandi:
- Target Selection: Attackers often target individuals or organizations with valuable data, using various methods like social media scraping or data breaches to gather information.
- Crafting the Bait: Emails are meticulously crafted to mimic legitimate sources, such as banks, credit card companies, or even trusted colleagues. They may contain logos, familiar layouts, and urgent language to instill trust and a sense of urgency.
- The Hook: Malicious links or attachments are embedded within the emails, designed to either steal sensitive information directly upon clicking or install malware that grants attackers access to systems and data.
Common Phishing Techniques:
- Spear Phishing: Highly targeted attacks personalized with specific details about the victim to increase legitimacy.
- Smishing: Phishing attempts delivered via text messages to mobile devices.
- Vishing: Phishing attempts conducted through phone calls, often impersonating customer service representatives or technical support personnel.
- Watering Hole Attacks: Compromising legitimate websites frequently visited by targets to infect their devices with malware when they visit.
Impact:
The consequences of successful phishing attacks can be severe:
- Data Breaches: Sensitive data like login credentials, financial information, or personal details can be stolen, leading to identity theft, financial losses, and reputational damage.
- Malware Infections: Downloaded malware can disrupt systems, steal data, or launch further attacks within the network.
- Ransomware Attacks: Phishing emails can be used to deliver ransomware that encrypts data, demanding ransom payments for decryption.
- Business Disruption: Phishing attacks can disrupt business operations, causing downtime and productivity losses.
Defense Strategies:
- Security Awareness Training: Educating employees and users about phishing tactics and red flags helps them identify and avoid suspicious emails.
- Email Filtering and Security Software: Utilize robust email filtering systems and security software to detect and block phishing attempts.
- Verification: Always verify the sender’s legitimacy, even if the email appears familiar. Do not click on suspicious links or attachments.
- Strong Passwords and Data Protection: Implement strong password policies and avoid sharing sensitive information readily.
- Multi-Factor Authentication: Employ MFA as an additional layer of security for critical accounts.
6. Malware
In the realm of cyber threats, malware stands as a prominent adversary, encompassing a diverse range of malicious software designed to harm individuals and organizations in various ways. Imagine it as a digital parasite, infiltrating systems and exploiting vulnerabilities to disrupt operations, steal data, or cause financial losses.

Cyber Security Threats World – Malware
Manifestations and Methods:
Malware can take on numerous forms, each with its distinct malicious intent:
- Viruses: Self-replicating malware that spreads readily through infected files or applications, aiming to damage systems and corrupt data.
- Worms: Similar to viruses but exploit network vulnerabilities to propagate automatically, potentially causing widespread disruption.
- Trojan Horses: Disguised as legitimate software or files, tricking users into installing them, granting attackers unauthorized access to systems.
- Ransomware: Encrypts a victim’s data, rendering it inaccessible, and demands a ransom payment for decryption, creating a high-pressure situation.
- Spyware: Steals sensitive information like passwords, financial data, or browsing habits without the user’s knowledge.
- Adware: Displays unwanted advertisements or redirects users to malicious websites, generating revenue for attackers.
Delivery Mechanisms:
Malware can infiltrate systems through various means:
- Phishing emails: Deceptive emails containing malicious attachments or links that, when clicked, download and install malware on the victim’s device.
- Exploiting software vulnerabilities: Attackers leverage unpatched vulnerabilities in software or operating systems to gain unauthorized access and deploy malware.
- Infected websites or downloads: Downloading files or visiting compromised websites can unknowingly install malware on your device.
- Physical media: Infected USB drives or other external storage devices can be used to spread malware.
Impact:
The consequences of malware infections can be significant:
- Data breaches: Sensitive information can be stolen, leading to identity theft, financial losses, and reputational damage.
- Financial losses: Ransomware attacks can demand hefty payments, and data breaches can incur significant recovery costs.
- System disruptions: Malware can disrupt operations, cause downtime, and hinder productivity.
- Privacy violations: Spyware can compromise user privacy by stealing personal information and browsing habits.
Defense Strategies:
- Security software: Install and maintain reputable antivirus and anti-malware software to detect and block malicious threats.
- Keep software updated: Regularly update operating systems, applications, and firmware to address known vulnerabilities.
- Be cautious with emails and downloads: Avoid suspicious emails, attachments, and downloads from untrusted sources.
- Use strong passwords: Employ unique and complex passwords for all accounts and enable multi-factor authentication when available.
- Back up your data: Regularly back up your data to ensure recovery options in case of malware infection.
7. Zero-Day Exploits
In the constant battle against cyber threats, zero-day exploits emerge as particularly dangerous weapons. These exploits target previously unknown vulnerabilities in software or systems, leaving defenders without patches or solutions to prevent attacks. Imagine an invisible crack in a fortress wall, known only to attackers, granting them unrestricted access before anyone can even begin repairs.

Cyber Security Threats World – Zero-Day Exploits
Modus Operandi:
- Discovery: Attackers meticulously research and identify vulnerabilities in software or systems that remain unknown to the vendor or developers. This often involves complex reverse engineering and analysis of software code.
- Weaponization: The discovered vulnerability is transformed into an exploit, a malicious code specifically designed to leverage the weakness and gain unauthorized access to systems or data.
- Silent Attack: Before the software vendor or users have any knowledge of the vulnerability, attackers launch their exploit, potentially compromising systems and stealing data before anyone can react.
Impact:
The consequences of successful zero-day exploits can be devastating:
- Data Breaches: Attackers can gain access to sensitive data like financial records, personal information, or intellectual property.
- System Takeovers: Exploits can be used to take complete control of systems, disrupt operations, and launch further attacks.
- Ransomware Attacks: Zero-day vulnerabilities can be exploited to deliver ransomware, encrypting data and demanding ransom payments.
- Reputational Damage: Organizations that experience zero-day attacks can suffer significant reputational damage and loss of trust from their customers and partners.
Defense Strategies:
- Security Patch Management: Implement a robust patch management system to apply security updates promptly once they become available.
- Endpoint Protection: Utilize endpoint protection software that can detect and block suspicious behavior, even if the specific exploit is unknown.
- Threat Intelligence: Subscribe to threat intelligence feeds to stay informed about emerging vulnerabilities and potential zero-day threats.
- Security Awareness Training: Educate employees about cyber threats and suspicious activities to help them identify and report potential attacks.
- Segmentation and Network Controls: Implement network segmentation and access controls to limit the potential impact of an exploit if it occurs.
8. IoT Vulnerabilities
The Internet of Things (IoT), encompassing a vast network of interconnected devices, presents exciting opportunities for automation and convenience. However, with this interconnectedness comes an increased attack surface and unique vulnerabilities that cybercriminals can exploit. Imagine a sprawling network of devices, each a potential entry point for attackers, creating a complex security challenge.
Nature of the Threat:

Cyber Security Threats World – IoT Vulnerabilities
IoT devices often have:
- Limited processing power and memory: This makes them less capable of implementing robust security measures, leaving them vulnerable to attacks.
- Standardized protocols and default configurations: Attackers can leverage known weaknesses in these protocols and exploit default configurations to gain access to multiple devices.
- Physical accessibility: Some IoT devices, like smart home gadgets, might be physically accessible, allowing attackers to tamper with them or inject malicious code.
Types of Vulnerabilities:
- Weak authentication and encryption: Insecure password practices and lack of encryption for data transmission can expose sensitive information.
- Outdated firmware: Unpatched devices with outdated firmware leave known vulnerabilities open to exploitation.
- Botnet recruitment: Large numbers of compromised devices can be aggregated into botnets to launch distributed denial-of-service (DDoS) attacks or spread malware.
- Data breaches: Sensitive data collected by IoT devices, like personal information or home automation data, can be targeted by attackers.
Impact:
- Disrupted operations: Compromised devices can disrupt critical infrastructure, causing power outages, transportation delays, or even physical harm.
- Privacy violations: Breached data can lead to identity theft, financial losses, and reputational damage.
- Cyber espionage: Sensitive information collected by IoT devices can be used for espionage or targeted attacks.
Defense Strategies :
- Strong authentication and encryption: Implement strong passwords, multi-factor authentication, and encrypt data transmission whenever possible.
- Regular firmware updates: Keep all devices updated with the latest firmware patches to address known vulnerabilities.
- Network segmentation: Isolate IoT devices from critical systems and segment them within the network to limit the attack surface.
- Physical security measures: Implement physical security measures to protect devices from unauthorized access.
- Security awareness training: Educate users about the risks of insecure IoT devices and encourage responsible practices.
9. Third-Party Exposure
In today’s interconnected world, organizations increasingly rely on third-party vendors and suppliers for various services and components. While this outsourcing offers efficiency and specialization, it also introduces a hidden vulnerability known as third-party exposure, posing significant cyber threats. Imagine your organization as a well-guarded fortress, but with a back door leading to a less secure partner’s network. Attackers might exploit this weaker link to gain access to your critical systems and data.
Understanding the Risk:

Cyber Security Threats World – Third-Party Exposure
Third-party exposure arises from dependencies on external entities, with potential vulnerabilities at various stages:
- Lack of visibility: Limited insight into third-party security practices and potential weaknesses creates blind spots in your overall cyber defense posture.
- Data sharing: Sharing sensitive data with third parties exposes it to additional risks if their security measures are inadequate.
- Supply chain attacks: Attackers can target vulnerabilities in a third-party’s systems or software to gain access to your organization through that compromised link.
- Integration risks: Insecure integration between your systems and third-party platforms can create additional entry points for cyberattacks.
Potential Consequences:
The consequences of failing to address third-party exposure can be severe:
- Data breaches: Attackers exploiting vulnerabilities in a third-party’s systems can gain access to your sensitive data, leading to financial losses, reputational damage, and regulatory penalties.
- Disruptions: Cyberattacks impacting your third-party partners can disrupt your operations, leading to downtime, lost productivity, and revenue losses.
- Ransomware attacks: Ransomware targeting a third party might encrypt your data stored on their systems, demanding ransom payments for decryption.
- Loss of trust: Security breaches caused by third-party vulnerabilities can erode customer and partner trust in your organization.
Defense Strategies :
- Rigorous vendor assessment: Conduct thorough security assessments of potential and existing third-party partners to evaluate their security practices and potential vulnerabilities.
- Contractual agreements: Establish clear contractual clauses that mandate specific security standards and compliance requirements for third parties handling your data.
- Data security controls: Implement data encryption, access controls, and other security measures to protect sensitive information shared with third parties.
- Continuous monitoring: Regularly monitor third-party activity and security posture to identify and address potential risks promptly.
- Incident response planning: Develop a comprehensive incident response plan to effectively manage and mitigate security incidents involving third parties.
10. Poor Cyber Hygiene
In the battlefield of cybersecurity, poor cyber hygiene emerges as a silent yet significant threat, creating vulnerabilities that attackers readily exploit. Imagine a fortress with sturdy walls but overflowing with waste, providing attackers with footholds and entry points. Similarly, neglecting basic security practices creates a breeding ground for cyber threats, jeopardizing individuals and organizations alike.

Cyber Security Threats World – Poor Cyber Hygiene
Manifestations of Poor Hygiene:
Several practices contribute to poor cyber hygiene:
- Weak passwords: Using easily guessable passwords or reusing them across multiple accounts creates easy access points for attackers.
- Unpatched software: Failing to update software with the latest security patches leaves known vulnerabilities exposed for attackers to exploit.
- Phishing susceptibility: Falling prey to phishing emails or clicking on suspicious links allows attackers to install malware or steal sensitive information.
- Unsanctioned software: Downloading and installing software from untrusted sources can introduce malware or other security risks.
- Physical device neglect: Losing or leaving devices unattended without proper password protection exposes them to unauthorized access.
- Lack of data backups: Not having regular backups of critical data leaves organizations vulnerable to data loss in case of cyberattacks or system failures.
Impact of Poor Hygiene:
The consequences of poor cyber hygiene can be far-reaching:
- Data breaches: Attackers can gain access to sensitive data like financial information, personal details, or intellectual property, leading to financial losses, identity theft, and reputational damage.
- Malware infections: Downloaded malware can disrupt operations, steal data, or launch further attacks within the network.
- Ransomware attacks: Unpatched systems are prime targets for ransomware attacks, where attackers encrypt data and demand ransom payments for decryption.
- System disruptions: Malware infections or compromised devices can disrupt critical systems, causing downtime and productivity losses.
- Compliance violations: Organizations with poor cyber hygiene practices may face regulatory penalties for non-compliance with data protection regulations.
Defense Strategies :
- Create strong and unique passwords: Use complex passwords with a combination of upper and lowercase letters, numbers, and symbols, and avoid reusing them.
- Enable multi-factor authentication (MFA): Add an extra layer of security by requiring a second verification step beyond just a password when logging in.
- Install and update software regularly: Keep operating systems, applications, and firmware updated with the latest security patches to address known vulnerabilities.
- Be cautious with emails and downloads: Verify the sender and legitimacy of emails before opening attachments or clicking on links. Download software only from trusted sources.
- Secure your devices: Use strong passwords or PINs to lock your devices and encrypt sensitive data. Avoid leaving them unattended in public places.
- Regularly back up your data: Implement a regular backup schedule to ensure you have copies of critical data in case of system failures or attacks.
- Educate users: Raise awareness among employees or family members about cyber threats and best practices for secure online behavior.
Types of Cybersecurity Solutions
The evolving landscape of cyber threats necessitates a diverse arsenal of solutions to protect your critical assets. Here’s a breakdown of some key types of cybersecurity solutions to consider:
1. Endpoint Security:
- Protects individual devices like laptops, desktops, and mobile phones from malware, unauthorized access, and data breaches.
- Solutions include antivirus/anti-malware software, endpoint detection and response (EDR), mobile device management (MDM).
2. Network Security:
- Safeguards your network infrastructure, including firewalls, routers, and switches, from unauthorized access and malicious traffic.
- Solutions include firewalls, intrusion detection and prevention systems (IDS/IPS), secure access service edge (SASE).
3. Cloud Security:
- Secures data and applications stored or processed in cloud environments like AWS, Azure, or Google Cloud Platform.
- Solutions include cloud access security broker (CASB), data encryption, cloud workload protection platforms (CWPP).
4. Application Security:
- Shields applications from vulnerabilities and attacks that exploit them to steal data or disrupt functionality.
- Solutions include static and dynamic application security testing (SAST & DAST), web application firewalls (WAF).
5. Data Security:
- Protects sensitive data at rest, in transit, and in use, ensuring confidentiality, integrity, and availability.
- Solutions include data encryption, data loss prevention (DLP), data masking, tokenization.
6. Identity and Access Management (IAM):
- Controls user access to systems and data based on their roles and permissions.
- Solutions include multi-factor authentication (MFA), single sign-on (SSO), identity governance and administration (IGA).
7. Security Information and Event Management (SIEM):
- Aggregates and analyzes security data from various sources to identify and respond to threats in real-time.
- Solutions include SIEM platforms, log management, security analytics.
8. Security Awareness Training:
- Educates employees about cyber threats and best practices for secure online behavior.
- Solutions include phishing simulations, security awareness training programs, security champions initiatives.
9. Incident Response:
- Provides a structured approach to identify, contain, eradicate, and recover from security incidents.
- Solutions include incident response plans, forensics tools, cyber insurance.
10. Threat Intelligence:
- Provides insights into emerging threats and vulnerabilities to proactively mitigate risks.
- Solutions include threat intelligence feeds, vulnerability management platforms, threat hunting.
Remember:
- No single solution offers complete protection. Combine these solutions based on your specific needs and risk profile.
- Stay updated: Regularly evaluate your security posture and adapt your solutions to address evolving threats.
- Seek expert guidance: Consult with cybersecurity professionals to design and implement a comprehensive security strategy.
Also Read : Cyber Security Tutorial
Conclusion
In 2024, cyber threats are diverse and sophisticated, from ransomware to poor cyber hygiene. Understanding these “Top 10 Cyber Security Threats” is crucial for protecting data and privacy. Implement robust security practices like software updates, strong passwords, and employee training to reduce risks. Stay informed about emerging threats and adopt a layered security approach. Remember, cybersecurity is a shared responsibility for individuals, organizations, and governments alike.
FAQs – CyberSecurity Threats
What is the biggest vulnerability in 2024?
In 2024, two big security flaws hit hard. CVE-2023-27350 let attackers into PaperCut, scoring 9.8 on CVSS. CVE-2023-34362 struck MOVEit Transfer, scoring the same, and got hit by ransomware too.
What are the OWASP Top 10 vulnerabilities for 2024?
A01:2021 – Broken Access Control, A02:2021 – Cryptographic Failures, A03:2021 – Injection, A04:2021 – Insecure Design, A05:2021 – Security Misconfiguration, A06:2021 – Vulnerable and Outdated Components, A07:2021 – Identification and Authentication Failures, A08:2021 – Software and Data Integrity Failures, A09:2021 – Security Logging and Monitoring Failures, A10:2021 – Server-Side Request Forgery (SSRF)
What are the risks of API?
APIs are vital for modern software, but they pose risks like data breaches and denial-of-service attacks. To stay safe, use strong authentication, validate data, update regularly, monitor activity, configure securely, and raise awareness.
Is A API secure?
Assessing the security of “A API” isn’t easy without specifics. Security varies, and no API is flawless. Key factors include authentication, data handling, configuration, monitoring, and infrastructure. To accurately evaluate, experts conduct penetration testing and code review.
Is REST API encrypted?
REST APIs aren’t automatically encrypted. Security relies on HTTPS for data and potential payload encryption. Check for HTTPS and payload encryption, and ensure proper authentication and input validation for overall security.
Share your thoughts in the comments
Please Login to comment...