Secure Shell, commonly known as SSH, is like a super-secure way to talk to faraway computers, called servers. It’s like a secret tunnel on the internet that keeps your conversations safe and private. Imagine you’re sending a letter, and instead of sending it openly, you put it in a magic envelope that only you and the person you’re sending it to can open. That’s what SSH does for your computer talks.
This article is here to help beginners, those who are just starting with this stuff, to understand how to use SSH. We’ll show you the steps to use a special command (think of it like a secret handshake) to connect your computer to a faraway server in the world of Linux. By the end of this guide, you’ll be more confident in using SSH to make your computer talks safe and secure when dealing with those remote servers.
What is SSH ?
SSH, or Secure Shell, constitutes a cryptographic network protocol designed to enable secure communication between two systems over networks that may not be secure. This protocol is widely employed for remote access to servers and the secure transmission of files between computers. In essence, SSH acts as a secure conduit, establishing a confidential channel for communication in scenarios where the network may pose security risks. This technology is instrumental for professionals seeking a reliable and secure method of managing servers and transferring sensitive data across computers in a controlled and protected manner. ssh runs at TCP/IP port 22.
Syntax of SSH Command in Linux
The basic syntax for using the SSH command is as follows:
ssh [username]@[hostname or IP address]
Here,
Replace [username] with your remote server username, and [hostname or IP address] with the server’s hostname or IP address.
Prerequisites
Before delving into the world of SSH, it’s essential to ensure that certain prerequisites are in place. Here’s a checklist to guarantee a smooth connection:
- Remote Computer Status:
- Make sure the remote computer is turned on and has an active network connection. SSH relies on network connectivity, and the remote server needs to be accessible.
- Identification Information:
- Obtain the IP address or the name of the remote machine. This information is crucial for directing your SSH connection to the correct server.
- Permission to Access:
- Ensure that you have the necessary permissions to access the remote computer. This typically involves having a valid username and password for the remote server.
- Firewall Settings:
- Check the firewall settings on both your local machine and the remote server. SSH connections use a specific port (usually port 22), so it’s crucial to ensure that your firewall allows SSH traffic. Adjustments may be required to permit secure communication.
Install SSH Component on Linux
Setting up SSH on Linux may be necessary, as some distributions don’t come with it pre-installed. Installing OpenSSH, a widely used SSH implementation, or opting for a graphical user interface (GUI) solution like the PuTTY client for Ubuntu can address this. Here’s a step-by-step guide on installing and configuring OpenSSH on both the client and server sides:
Installing it on Both Client and Server
For Debian/Ubuntu-based Systems, open the terminal and run:
sudo apt install openssh-client openssh-server
For Red Hat-based systems like CentOS or Fedora, use either of the following commands:
sudo dnf install openssh-clients openssh-server
or
sudo yum install openssh-clients openssh-server
Note : To check the status of running server after installation we can use this command “systemctl status sshd”
In case the service is not running, run it with the following command:
sudo systemctl start sshd
The command does not print an output.
To have the service start automatically on boot, run:
sudo systemctl enable sshd
Enabling the sshd service starts it during the boot process.
How to Use SSH to Connect to a Remote Server in Linux
In this example we access Ubuntu or Red hat Linux machine via the Windows command prompt using `ssh`
For example: If our IP address is “10.143.90.2” and username is “Jayesh”
Syntax to use ssh to connect to a remote server:
ssh jayesh@10.143.90.2
Add your username in place of “Jayesh” and add your IP address in place of “10.143.90.2”
 ssh to linux system from windows
ssh to linux system from windows
command consists of 3 different parts:
- ssh command instructs the system to establish an encrypted secure connection with the host machine.
- user_name represents the account that is being accessed on the host.
- host refers to the machine which can be a computer or a router that is being accessed. It can be an IP address (e.g., 192.168.1.24) or domain e.g., www.domainname.com).
Note: After logging into the host computer, commands will work as if they were written directly to the host terminal. Using a public-private key pair or SSH key pair to login into the remote host is more secure as compared to using passwords.
How to create public-private keys?
For generating public-private keys use the command:
ssh-keygen
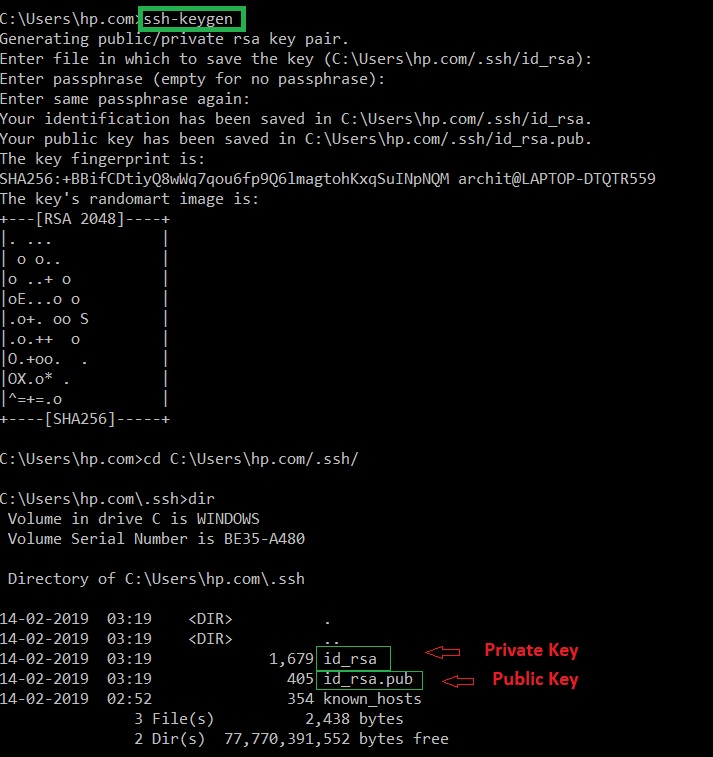 ssh-keygen
ssh-keygen
The private key must remain hidden while the public key must be copied to the remote host. After copying the public key to the remote host, the connection will be established using SSH keys and not the password.
Options available in ssh
Note: Here instead of user and host add username and IP address you want to connect to. And localhost is IP of our local system.
| Forces ssh to use protocol SSH-1 only. |
ssh -1 user@host
|
| Forces ssh to use protocol SSH-2 only. |
ssh -2 user@host
|
| Allows IPv4 addresses only. |
ssh -4 user@host
|
| Allows IPv6 addresses only. |
ssh -6 user@host
|
| Authentication agent connection forwarding is enabled. |
ssh -A user@host
|
| Authentication agent connection forwarding is disabled. |
ssh -a user@host
|
| Compresses all data (including stdin, stdout, stderr, and data for forwarded X11 and TCP connections) for a faster transfer of data. |
ssh -C user@host
|
| Selects the cipher specification for encrypting the session. Specific cipher algorithm will be selected only if both the client and the server support it. |
ssh -c aes256-cbc user@host
|
| Requests ssh to go to background just before command execution. |
ssh -f user@host command
|
| Allows remote hosts to connect to local forwarded ports. |
ssh -g -L 8080:localhost:80 user@host
|
| Prevents reading from stdin. |
ssh -n user@host command
|
| Port to connect to on the remote host. |
ssh -p 2222 user@host
|
| Suppresses all errors and warnings |
ssh -q user@host
|
| Display the version number. |
ssh -V
|
| Verbose mode. It echoes everything it is doing while establishing a connection. It is very useful in the debugging of connection failures. |
ssh -v user@host
|
| Enables X11 forwarding (GUI Forwarding). |
ssh -X user@host
|
The Three Major Encryption Techniques Used by SSH.
SSH is significantly more secure than the other protocols such as telnet because of the encryption of the data. There are three major encryption techniques used by SSH:
- Symmetrical encryption: This encryption works on the principle of the generation of a single key for encrypting as well as decrypting the data. The secret key generated is distributed among the clients and the hosts for a secure connection. Symmetrical encryption is the most basic encryption and performs best when data is encrypted and decrypted on a single machine.
- Asymmetrical encryption: This encryption is more secure because it generates two different keys: Public and Private key. A public key is distributed to different host machines while the private key is kept securely on the client machine. A secure connection is established using this public-private key pair.
- Hashing: One-way hashing is an authentication technique which ensures that the received data is unaltered and comes from a genuine sender. A hash function is used to generate a hash code from the data. It is impossible to regenerate the data from the hash value. The hash value is calculated at the sender as well as the receiver’s end. If the hash values match, the data is authentic.
Frequently asked questions about `ssh` command in Linux.
1) What does SSH stand for?
SSH stands for “Secure Shell”.
2) What is SSH used for?
SSH is used to securely connect to a remote system or server. It can be used to transfer data between two connected systems.
3) What port does SSH run on?
SSh runs at TCP/IP port 22.
4) How can we access a Linux Machine via the Windows command prompt using SSH?
We can access a Linux machine via the windows command by using SSH
syntax:
ssh user_name@host(IP/Domaimn_name)
5) How can we create public-private keys using SSH?
By using SSH by using the command
ssh-keygen
6) What are the three major encryption techniques used by SSH?
The three major encryption techniques used by SSH are:
- Symmetrical encryption
- Asymmetrical encryption
- Hashing
(Explained in above context)
7) How do I use SSH to connect to a remote server in Linux?
Replace `username` with your actual username and `remote_server_ip` with the IP address or domain of the remote server.
ssh username@remote_server_ip
8) What is the SSH command for connecting to a server with a specific port?
This command connects to the remote server using port 2222. Adjust the port number as needed.
ssh -p 2222 username@remote_server_ip
9) How can I use SSH to transfer files between my local machine and a remote server?
Using SCP for file transfer. This command securely copies the local file to the specified destination on the remote server. Adjust the file paths and names accordingly.
scp local_file.txt username@remote_server_ip:/path/to/destination/
Conclusion
In this article we discussed Secure Shell (SSH) which is like a secret, safe tunnel for computers to talk securely over the internet. This guide is for beginners, helping them use SSH to connect their computer to faraway servers in the Linux world. It covers everything from the basic SSH command to prerequisites like checking your internet connection and having the right permissions. You’ll learn how to install SSH on Linux, create secure keys, and use them for safer logins. The article also includes frequently asked questions with simple answers, making sure you can confidently and securely manage remote servers using SSH in Linux. It’s like giving your computer a secret code to talk safely on the internet!
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...