Securing Cassandra
Last Updated :
30 Sep, 2022
In this article, we will discuss how we can secure a Cassandra cluster and It involves tasks like authentication, authorization, etc. let’s discuss one by one.
There are four concepts to secure Cassandra Authorization, Authentication, Encryption, Firewalls.
-
Authentication:
In this, we will check How we allow applications and users to log into the cluster.
- Authorization:
In this, we deal with the granting of permissions such that the user wants to create, read and write data, etc. to access a database or database objects such as tables and materialized views.
- Encryption:
In this, we refer to the use of the Secure Socket Layer (SSL) which is security layers to secure communications between clients and Cassandra databases, and among a cluster’s nodes.
- Firewalls:
In this, we managing firewall port such that 9042 is a Client port for Cassandra (client) access involves knowing which ports you must keep open.
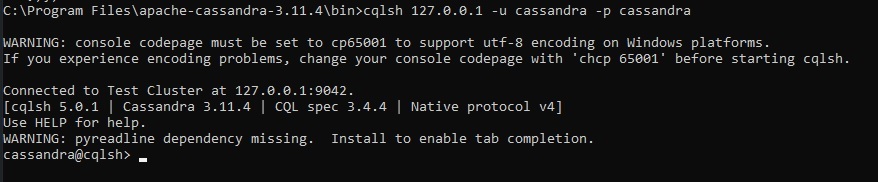
Now, we are going to use cqlsh with administrator privileges. Cassandra comes with a built-in role Cassandra and the password is also Cassandra. cqlsh query used to access the built-in role is the following.
cqlsh 127.0.0.1 -u cassandra -p cassandra
Output:
Now, If we will try to create a new role, alter Role, Drop Role, etc. we can receive the following error like
InvalidRequest: Error from server:
code=2200 [Invalid query]message="org.apache.cassandra.auth.CassandraRoleManager
doesn't support PASSWORD.
Configuring Authentication :
All authorization and authentication are through database roles. Use the CREATE ROLE, ALTER ROLE, DROP ROLE, LIST ROLES, and LIST_PERMISSIONS commands instead.
To resolve the following error change default Authentication values in the cassandra.yaml file.
//default value
#authenticator: AllowAllAuthenticator
// set the authenticator value
authenticator: org.apache.cassandra.auth.PasswordAuthenticator
//default value
#authorizer: AllowAllAuthorizer
//set the authorizer value
authorizer: org.apache.cassandra.auth.CassandraAuthorizer
After any change in the Cassandra.yaml file saves the file and then Restart the database and again log in to cqlsh using the credentials for the default superuser Cassandra.
cqlsh -u cassandra -p cassandra
Now, we are going to create a new role, list role, drop role, etc.
Create a new role :
To create a new role used the following CQL query.
cassandra@cqlsh> create user 'User' with password 'User';
We can see the output of the following query by using “list roles” commands.
Output:

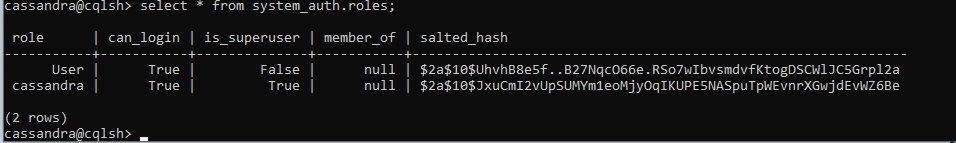
In Cassandra By default, the LOGIN property in the CREATE ROLE statement has the value False. When you’re creating a login role, you must set this property to True. we can view the roles in a database by querying the system_auth.roles table, shown here:
//system_auth.roles: Stores roles and role members.
select * from system_auth.roles;
Output:
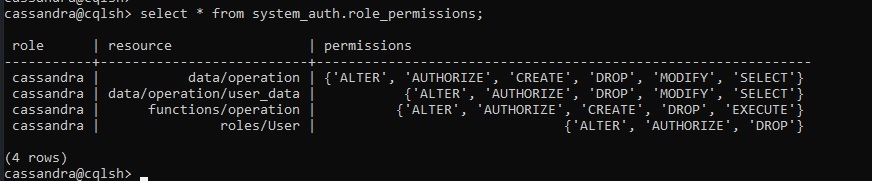
Role permissions:
By using, role permissions cql query we can check the permissions like a role can create, read, delete, etc. data operations on a particular database and role created by a superuser.
cassandra@cqlsh> select * from system_auth.role_permissions;
Output:
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...