Secure Electronic Transaction (SET) Protocol
Last Updated :
21 Mar, 2023
Secure Electronic Transaction or SET is a system that ensures the security and integrity of electronic transactions done using credit cards in a scenario. SET is not some system that enables payment but it is a security protocol applied to those payments. It uses different encryption and hashing techniques to secure payments over the internet done through credit cards. The SET protocol was supported in development by major organizations like Visa, Mastercard, and Microsoft which provided its Secure Transaction Technology (STT), and Netscape which provided the technology of Secure Socket Layer (SSL).
SET protocol restricts the revealing of credit card details to merchants thus keeping hackers and thieves at bay. The SET protocol includes Certification Authorities for making use of standard Digital Certificates like X.509 Certificate.
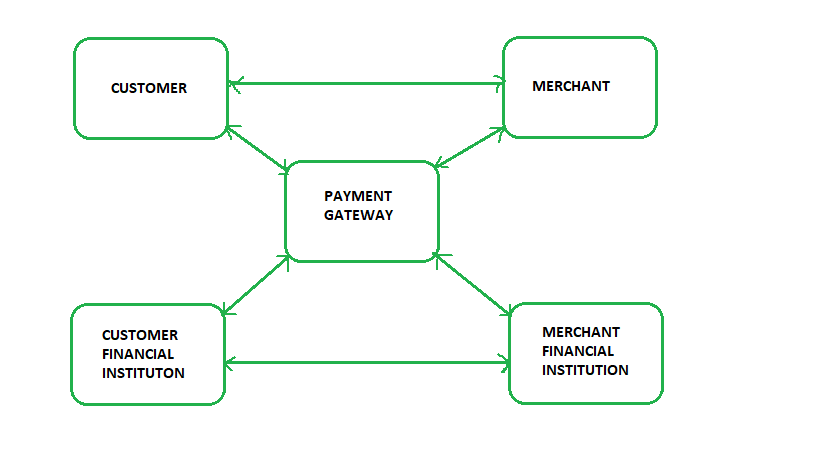
Before discussing SET further, let’s see a general scenario of electronic transactions, which includes client, payment gateway, client financial institution, merchant, and merchant financial institution.
Requirements in SET: The SET protocol has some requirements to meet, some of the important requirements are:
- It has to provide mutual authentication i.e., customer (or cardholder) authentication by confirming if the customer is an intended user or not, and merchant authentication.
- It has to keep the PI (Payment Information) and OI (Order Information) confidential by appropriate encryptions.
- It has to be resistive against message modifications i.e., no changes should be allowed in the content being transmitted.
- SET also needs to provide interoperability and make use of the best security mechanisms.
Participants in SET: In the general scenario of online transactions, SET includes similar participants:
- Cardholder – customer
- Issuer – customer financial institution
- Merchant
- Acquirer – Merchant financial
- Certificate authority – Authority that follows certain standards and issues certificates(like X.509V3) to all other participants.
SET functionalities:
- Provide Authentication
- Merchant Authentication – To prevent theft, SET allows customers to check previous relationships between merchants and financial institutions. Standard X.509V3 certificates are used for this verification.
- Customer / Cardholder Authentication – SET checks if the use of a credit card is done by an authorized user or not using X.509V3 certificates.
- Provide Message Confidentiality: Confidentiality refers to preventing unintended people from reading the message being transferred. SET implements confidentiality by using encryption techniques. Traditionally DES is used for encryption purposes.
- Provide Message Integrity: SET doesn’t allow message modification with the help of signatures. Messages are protected against unauthorized modification using RSA digital signatures with SHA-1 and some using HMAC with SHA-1,
Dual Signature: The dual signature is a concept introduced with SET, which aims at connecting two information pieces meant for two different receivers :
Order Information (OI) for merchant
Payment Information (PI) for bank
You might think sending them separately is an easy and more secure way, but sending them in a connected form resolves any future dispute possible. Here is the generation of dual signature:
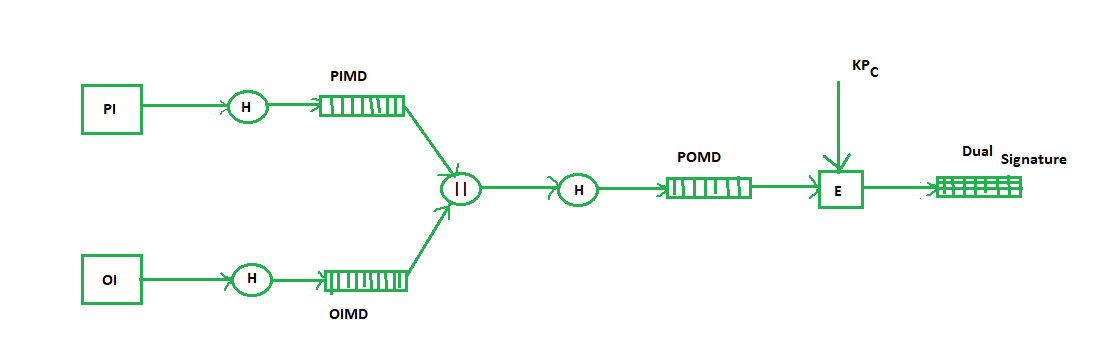
Where,
PI stands for payment information
OI stands for order information
PIMD stands for Payment Information Message Digest
OIMD stands for Order Information Message Digest
POMD stands for Payment Order Message Digest
H stands for Hashing
E stands for public key encryption
KPc is customer's private key
|| stands for append operation
Dual signature, DS= E(KPc, [H(H(PI)||H(OI))])
Purchase Request Generation: The process of purchase request generation requires three inputs:
- Payment Information (PI)
- Dual Signature
- Order Information Message Digest (OIMD)
The purchase request is generated as follows:
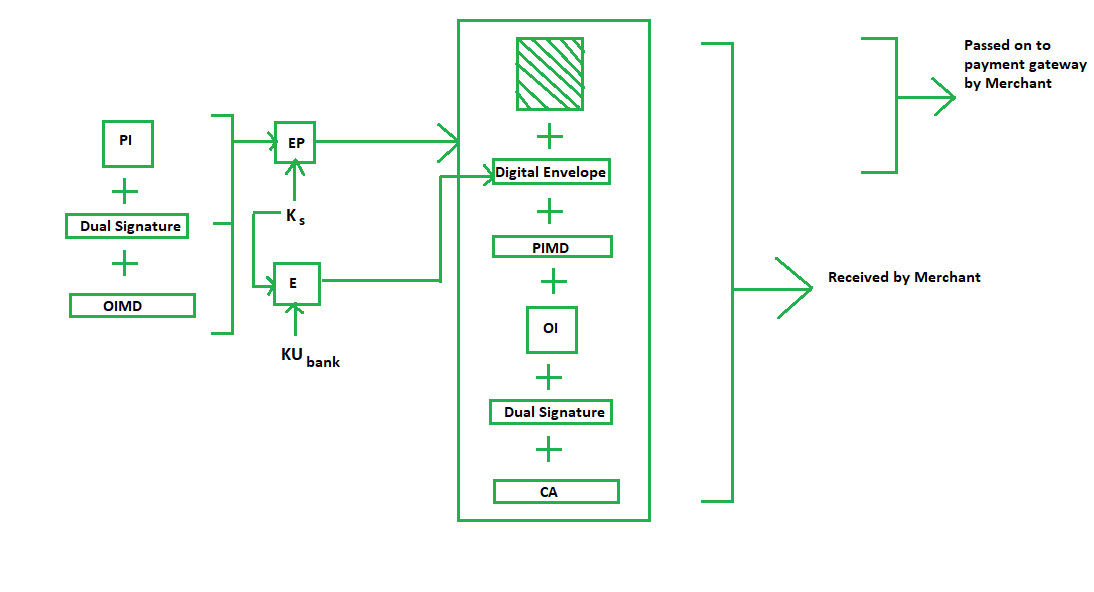
Here,
PI, OIMD, OI all have the same meanings as before.
The new things are :
EP which is symmetric key encryption
Ks is a temporary symmetric key
KUbank is public key of bank
CA is Cardholder or customer Certificate
Digital Envelope = E(KUbank, Ks)
Purchase Request Validation on Merchant Side: The Merchant verifies by comparing POMD generated through PIMD hashing with POMD generated through decryption of Dual Signature as follows:
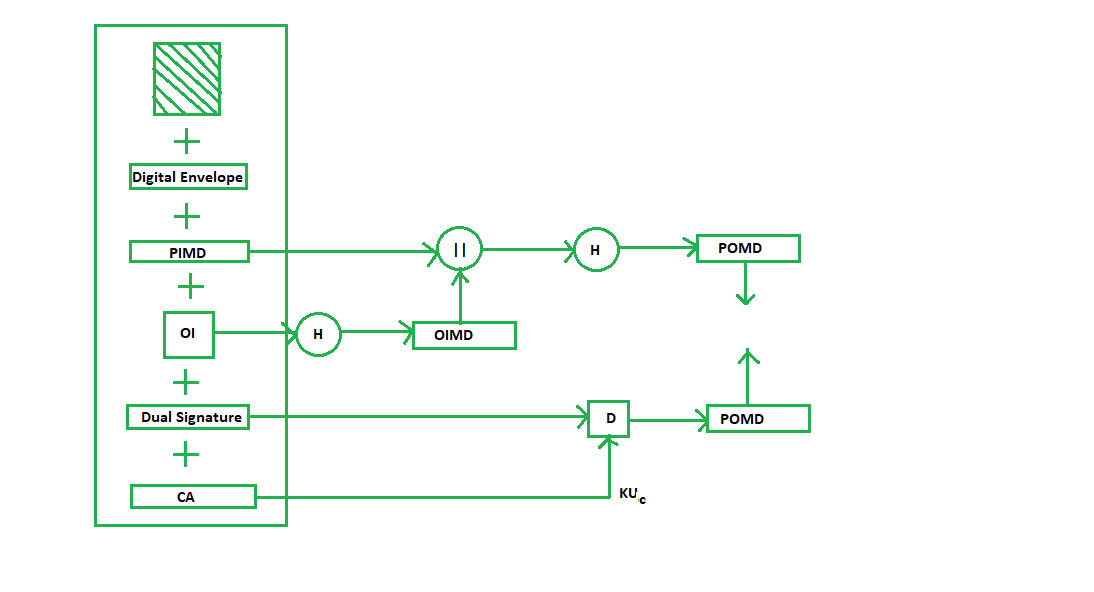
Since we used Customer’s private key in encryption here we use KUC which is the public key of the customer or cardholder for decryption ‘D’.
Payment Authorization and Payment Capture: Payment authorization as the name suggests is the authorization of payment information by the merchant which ensures payment will be received by the merchant. Payment capture is the process by which a merchant receives payment which includes again generating some request blocks to gateway and payment gateway in turn issues payment to the merchant.
The disadvantages of Secure Electronic Exchange: At the point when SET was first presented in 1996 by the SET consortium (Visa, Mastercard, Microsoft, Verisign, and so forth), being generally taken on inside the following couple of years was normal. Industry specialists additionally anticipated that it would immediately turn into the key empowering influence of worldwide internet business. Notwithstanding, this didn’t exactly occur because of a few serious weaknesses in the convention.
The security properties of SET are better than SSL and the more current TLS, especially in their capacity to forestall web based business extortion. Be that as it may, the greatest downside of SET is its intricacy. SET requires the two clients and traders to introduce extraordinary programming – – card perusers and advanced wallets – – implying that exchange members needed to finish more jobs to carry out SET. This intricacy likewise dialed back the speed of web based business exchanges. SSL and TLS don’t have such issues.
The above associated with PKI and the instatement and enlistment processes additionally slowed down the far reaching reception of SET. Interoperability among SET items – – e.g., declaration interpretations and translations among entrusted outsiders with various endorsement strategies – – was likewise a huge issue with SET, which likewise was tested by unfortunate convenience and the weakness of PKI.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...