Practical Uses of OpenSSL command in Linux
Last Updated :
23 Mar, 2020
OpenSSL is a cryptography software library or toolkit that makes communication over computer networks more secure. The OpenSSL program is a command-line tool for using the various cryptography functions of OpenSSL’s crypto library from the shell. It is generally used for Transport Layer Security(TSL) or Secure Socket Layer(SSL) protocols. OpenSSL is licensed under an apache-style license, which means that under some simple license conditions, one can use the toolkit for commercial or non-commercial purposes.
You can check the installed version of OpenSSL command using the following command
$openssl version

Practical Uses of OpenSSL Command
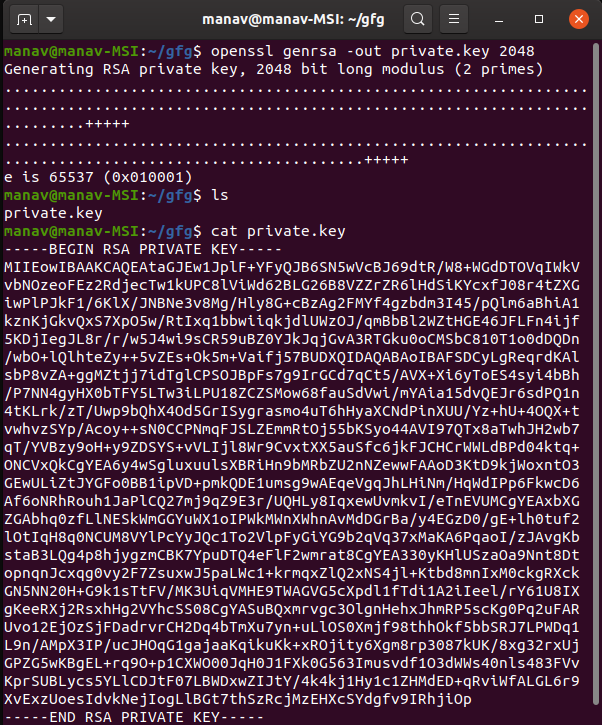
1. To Create RSA Private Key.
$openssl genrsa -out private.key 2048
It will generate the RSA key file with the name private.key. Here, we have used 2048 for high security. Lower bit size can even be used.
2. Create new Private Key and CSR.
$openssl req -nodes -newkey rsa:2048 -keyout custom.key -out custom.csr
It will ask for the details like country code, state and locality name, Organization name, your name, email address, etc. And after entering all the details it will generate 2 files one with the CSR extension and the other with key extension representing CSR and private key respectively.

3. Create new Private Key and Self Signed certificate.
$openssl req -x509 -sha512 -nodes -days 730 -newkey rsa:2048 -keyout custom.key -out custom.pem
It will ask for details like country code, state and locality name, Organization name, your name, email address, etc. And after entering all the details it will generate 2 files one with the PEM extension and the other with key extension representing Self Signed Certificate and private key respectively. In the example, we have set validity to 730 days but in case you don’t mention this then it will take the value of one month by default. You can even change the algorithm of encryption as per your own convenience. In this example, we have used the SHA512 algorithm.

4. Verifying a CSR file
$openssl req -noout -text -in custom.csr
It will display the details you entered at the time of creating the CSR file which could be used to verify that the correct CSR file is sent to the correct receiver.

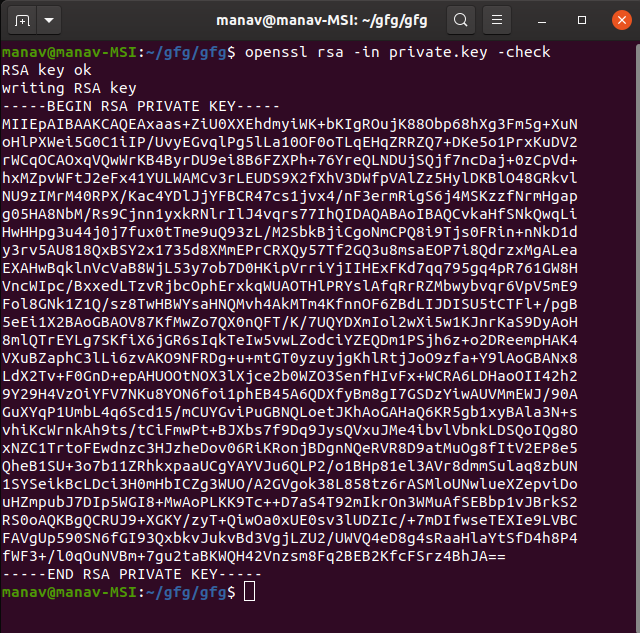
5. Verifying a private key file.
$openssl rsa -in private.key -check
It will verify and check the RSA key and if it is Ok it will display the following result.
6. Verifying the Certificate Signer Authority
$openssl x509 -in custom.pem -noout -issuer -issuer_hash
It will display the details you entered at the time of creating the pem file which could be used to verify that the correct pem file is sent to the correct receiver.

7. Checking Hash value of a certificate
$openssl x509 -noout -hash -in custom.pem
It will display the hash value of the pem certificate file.

8. Converting PEM to DER format
$openssl x509 -outform der -in custom.pem -out custom.der
It will change the extension of the certificate from .pem to .der and will create a new file with .der extension.

9. Checking pem file certificate expiry date
$openssl x509 -noout -in custom.pem -dates
It will display the valid from and valid up to date of the certificate.

Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...