Personally Identifiable Information Leakage Vulnerability
Last Updated :
12 Dec, 2022
Personally identifiable information leakage vulnerability is a vulnerability where the information gives specific details about a specific individuals,that in turns help to distinguish that particular individuals from the rest of other individual. Further, this vulnerability becomes critical when the information is used to track, identify or contact a particular individual. For example, the information used to pinpoint a individual are – address,name,phone number,identifying number such as aadhaar number or pan card details,gender,date of birth, email address, or a combination of these things. The non-sensitive information of individual like name,gender etc can be transferred in an insecure form without causing any harm to the individual but the sensitive information like aadhaar card details,pan card number etc must be transferred in a secure way such as encrypting the data so as to prevent any unwanted exposure of the data or cause harm to the individual. Organizations uses PIIL (personally identifiable information leakage ) to understand which information are needed to be kept secure and which information dont need any extra security.
What kind of information can be regarded as personally identifiable information (PII):
The following are the categories of Personally Identifiable Information:
- Identity: This includes the name,date of birth, signature,gender,race,alias of name etc of the individual
- Contact information: This includes the Street address, work address, phone number,email id etc of the individual
- Personal identification number: This includes the aadhaar number,bank account number,pan card number,driving license number,passport number,credit card number of the individual
- Professional information: This includes the job role to which the individual is entitled, his date of joining,his company name, his salary, his HR etc.
- Healthcare: This includes individual’s fingerprint, iris scanner, photograph,his personal medical records etc.
- IT related: This mainly consists of an individual’s IP address, his browsing history, his ad preference, cookies etc.
Who is responsible to guard personally identifiable information (PII):
To safeguard Personally Identifiable Information of the users, it’s the responsibility of the individual as well as the responsibility of the organization that stores the data of the individual.but generally the organization makes sure to protect your data even if the organization is not meant to do so. The simple reason being is most of the consumers believe that the organization is responsible to safeguard their data, and if the organization fails to do so, then it may face reputational damage thus losing valuable customers even if the organization or the company is not really responsible for this. Therefore, every organizations always make sure to protect the data of their customers. The rise in data breaches is making the security standards of organization higher day by day. As new technologies are rolling out, newer kinds of threats and attacks are also rolling out. following are the main kinds of data breaches:
- Harming or targeting an individual: By leaking information about individuals, the hacker intends to blackmail the victim or can even cause data theft,bullying, humiliation etc.
- Harming or targeting a particular organization: By leaking information from an organization’s database, the hacker intends to reduce the trust of customers, close the company due to loss of huge data, cause reputational damage etc.
How the PII gets exposed:
Personally Identifiable Information can occur in variety of ways making it difficult for the data security protocols to prevent such leakage and to protect sensitive or confidential information. following are the categories of threats-
- Insider threat: This involves a person who is from inside the organization intentionally or unintentionally views sensitive data which otherwise shouldnt be accessible to common users. This indirectly creates risk to the organizations reputation and displays its inability to secure consumers information properly.example- the employee details is sent to someone in plain text format and is not encrypted to secure its transmission.
- Outside threat: This involves a person who is outside the organization( precisely an intruder) who tries to tamper with the system’s data in order to extract confidential data from the system. strict implementation of security prevents such mishaps from happening. example- social engineering the password of the social media accounts.
- Security misconfigurations: This generally happens with an application that either intends to store sensitive data or captures it. Security misconfigurations can expose huge amount of data and can also provide a gateway to internal and external threat agents to get the sensitive data. Example- company not incorporating two factor authentication or otp to add to the security levels.
Example of PII:
The below picture shows a live example of Personally Identifiable Information leakage.
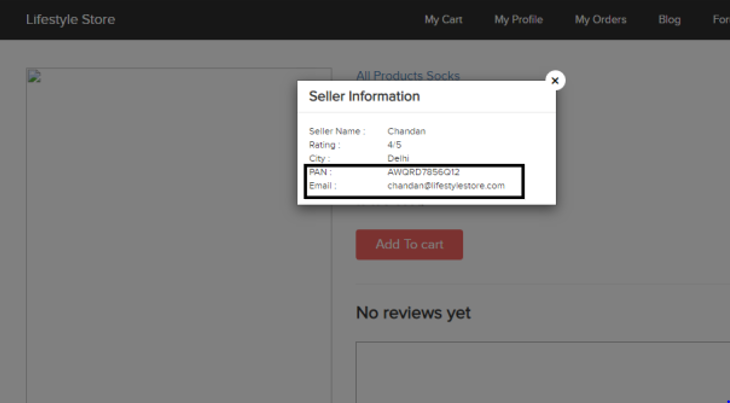
as we can see, its an e-commerce website that looks somewhat similar to facebook. in this, when one clicks on seller info, a pop up is displayed on screen and it shows the city, pan card number,email id of the seller which is clearly leaking confidential information about that seller. now the seller can easily be targeted by misusing these information which is available to all the consumer of this website.Now we understood the vulnerability of this leakage.
How to protect personally identifiable information (PII):
As we discussed earlier about the sensitive and non sensitive data, thus its natural to protect only the sensitive data from leakage.Organizations must apply proper safeguards to protect the confidentiality of PII based on categories of PII in its confidentiality impact levels. following are the measures that need to be taken-
- Training: All the employees of the organization must be trained in such a way so as to prevent any inside threat mishap.training the employees properly reduces the possibility of PII leakage substantially.
- Reduce PII holdings: This means the organization or the user must give only the required details and avoid unnecessary non mandatory details . in nutshell- the minimum data needed to operate. This reduces the chance to pin point or target a individual with lesser known data.
- Remove unnecessary collection of PII: Establishing a plan or mechanism inside company to remove any unnecessary collection of information from its consumers and use of PII for proper functioning of application.
- Data Loss Prevention: Implementing such systems that can track the transfer of sensitive data within or outside the organization and identify suspicious patterns that might lead to a breach.
- Restricting access: Implementing software that prevent certain individual of organization to access highly sensitive information thereby preventing any possibility of inside attacks or threats. it must be made on an authorization basis.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...