No rate limiting flaw in cyber security
Last Updated :
22 Jun, 2022
Rate limiting is a process to limit requests possible. It is used to control network traffic.Suppose a web server allows upto 20 requests per minute. If you try to send more than 20 requests, an error will be triggered. This is necessary to prevent the attackers from sending excessive requests to the server.
No rate limit is a flaw that doesn’t limit the no. of attempts one makes on a website server to extract data.It is a vulnerability which can prove to be critical when misused by attackers.
REAL LIFE EXAMPLES :
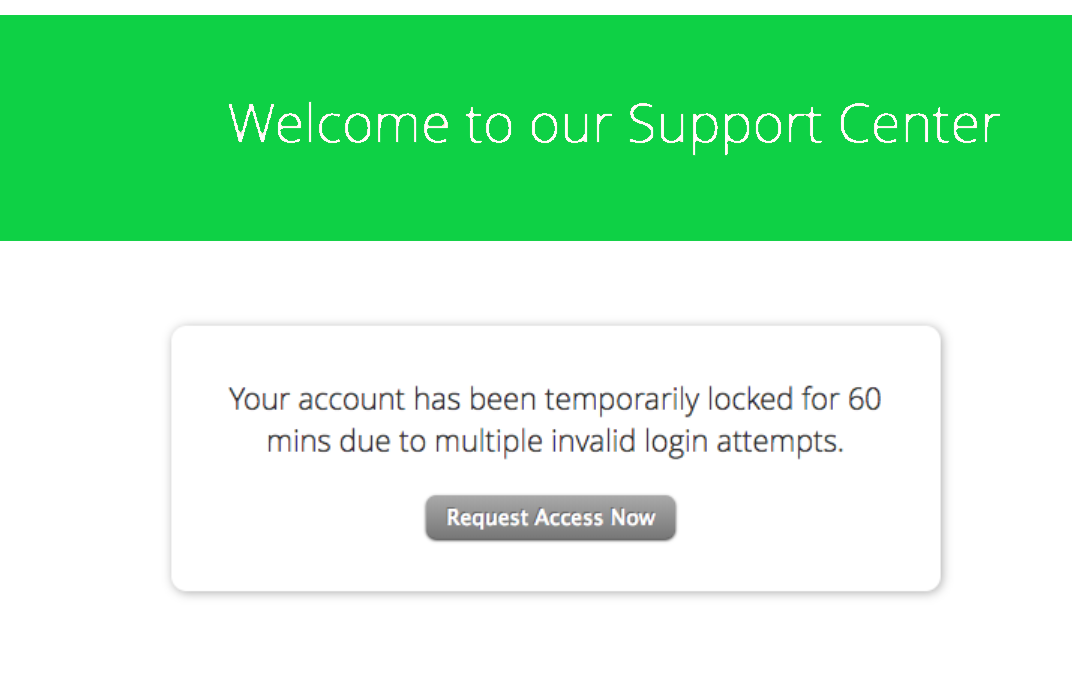
- When you try to login to your account, after 3-4 wrong attempts, your account gets suspended for some hours.Rate limiting is the reason behind it!
Example-
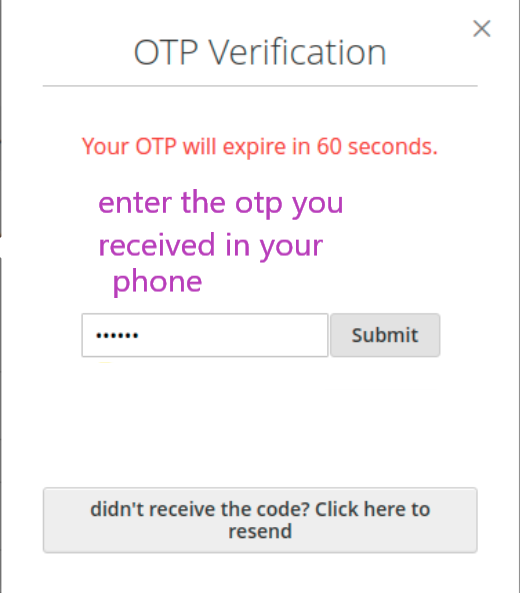
2.The otp you get has some time limit, after which your otp becomes invalid. Here too, rate limiting is the reason behind it.
Example –
USES OF RATE LIMITING FEATURE :
- reduces excessive load on web servers
- prevent DOS(denial of service) attack
- help stop certain kinds of malicious bot activity like login to an account using multiple guess password and user id
- Also prevent brute-force attacks
RECENT RATE LIMITING FLAW IN ZOOM APP :
The zoom app has become popular in the lockdown , it has become an essential alternative to offline classes.Attackers were successfully able to crack the password of the private meetings by exploiting the no-rate limit flaw vulnerability of zoom app.Zoom web client allowed brute force attempts to crack password protected private meetings that occurred in Zoom.Later, this vulnerability was patched by security experts.
BUSINESS IMPACT :
Let’s take an OTP situation. Now suppose, the length of otp is 3 digits and an attacker is guessing the otp for successful transaction theft. If no rate limiting is implemented in the web application, the hacker can manually type 000-999 values on otp to check which one is correct. This method is a little bit cumbersome, so the hacker can use a burp suite tool to do the same job in less time.Hence, after 30min, the otp gets unlocked and the attack is successful.
Now, in the same scenario, if rate limiting was implemented in a web application, suppose allow only 5 attempts or a time limit of 2 minutes. In this case, it’s almost impossible for the hacker to crack the otp . Thus,preventing the attack from happening.
HOW TO PREVENT RATE LIMITING FLAW?
- Monitoring API activity against your rate limit.
- Catching errors caused by rate limiting.
- Reducing the number of requests.
- Extra precautions are taken with login, otp, vouchers etc.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...