Network security is defined as the activity created to protect the integrity of your network and data. Every company or organization that handles a large amount of data, has a degree of solutions against many cyber threats.
Any action intended to safeguard the integrity and usefulness of your data and network is known as network security. This is a broad, all-encompassing phrase that covers software and hardware solutions, as well as procedures, guidelines, and setups for network usage, accessibility, and general threat protection.
The most basic example of Network Security is password protection which the user of the network chooses. In recent times, Network Security has become the central topic of cyber security with many organizations inviting applications from people who have skills in this area. The network security solutions protect various vulnerabilities of the computer systems such as:
- Users
- Locations
- Data
- Devices
- Applications
Types of Network Security
There are several types of network security through which we can make our network more secure, Your network and data are shielded from breaches, invasions, and other dangers by network security. Here below are some important types of network security:
1. Email Security
The most common danger vector for a security compromise is email gateways. Hackers create intricate phishing campaigns using recipients’ personal information and social engineering techniques to trick them and direct them to malicious websites. To stop critical data from being lost, an email security programme restricts outgoing messages and stops incoming threats.
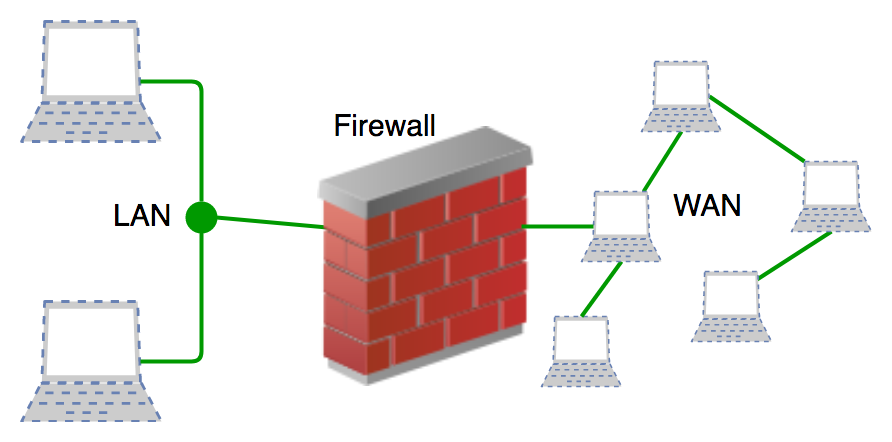
2. Firewalls
Your trusted internal network and untrusted external networks, like the Internet, are separated by firewalls. They control traffic by enforcing a set of predetermined rules. A firewall may consist of software, hardware, or both.
3. Network Segmentation
Network traffic is divided into several categories by software-defined segmentation, which also facilitates the enforcement of security regulations. Ideally, endpoint identity—rather than just IP addresses—is the basis for the classifications. To ensure that the appropriate amount of access is granted to the appropriate individuals and that suspicious devices are controlled and remediated, access permissions can be assigned based on role, location, and other factors.
4. Access Control
Your network should not be accessible to every user. You need to identify every user and every device in order to keep out any attackers. You can then put your security policies into effect. Noncompliant endpoint devices might either have their access restricted or blocked. Network access control (NAC) is this process.
5. Sandboxing
Sandboxing is a cybersecurity technique in which files are opened or code is performed on a host computer that simulates end-user operating environments in a secure, isolated environment. To keep threats off the network, sandboxing watches the code or files as they are opened and searches for harmful activity.
6. Cloud Network Security
Workloads and applications are no longer solely housed in a nearby data centre on-site. More adaptability and creativity are needed to protect the modern data centre as application workloads move to the cloud.
7. Web security
A online security solution will restrict access to harmful websites, stop web-based risks, and manage staff internet usage. Your web gateway will be safeguarded both locally and in the cloud. “Web security” also include the precautions you take to safeguard your personal website.
Benefits of Network Security
Network Security has several benefits, some of which are mentioned below:
- Network Security helps in protecting clients’ information and data which ensures reliable access and helps in protecting the data from cyber threats.
- Network Security protects the organization from heavy losses that may have occurred from data loss or any security incident.
- It overall protects the reputation of the organization as it protects the data and confidential items.
Working on Network Security
The basic principle of network security is protecting huge stored data and networks in layers that ensure the bedding of rules and regulations that have to be acknowledged before performing any activity on the data.
These levels are:
- Physical Network Security
- Technical Network Security
- Administrative Network Security
These are explained below:
1. Physical Network Security: This is the most basic level that includes protecting the data and network through unauthorized personnel from acquiring control over the confidentiality of the network. The same can be achieved by using devices like biometric systems.
2. Technical Network Security: It primarily focuses on protecting the data stored in the network or data involved in transitions through the network. This type serves two purposes. One is protected from unauthorized users, and the other is protected from malicious activities.
3. Administrative Network Security: This level of network security protects user behavior like how the permission has been granted and how the authorization process takes place. This also ensures the level of sophistication the network might need for protecting it through all the attacks. This level also suggests necessary amendments that have to be done to the infrastructure.
Types of Network Security
The few types of network securities are discussed below:
1. Access Control: Not every person should have a complete allowance for the accessibility to the network or its data. One way to examine this is by going through each personnel’s details. This is done through Network Access Control which ensures that only a handful of authorized personnel must be able to work with the allowed amount of resources.
2. Antivirus and Anti-malware Software: This type of network security ensures that any malicious software does not enter the network and jeopardize the security of the data. Malicious software like Viruses, Trojans, and Worms is handled by the same. This ensures that not only the entry of the malware is protected but also that the system is well-equipped to fight once it has entered.
3. Cloud Security: This is very vulnerable to the malpractices that few unauthorized dealers might pertain to. This data must be protected and it should be ensured that this protection is not jeopardized by anything. Many businesses embrace SaaS applications for providing some of their employees the allowance of accessing the data stored in the cloud. This type of security ensures creating gaps in the visibility of the data.
4. Email Security: Email Security is defined as the process designed to protect the Email Account and its contents safe from unauthorized access. For Example, you generally see, fraud emails are automatically sent to the Spam folder. because most email service providers have built-in features to protect the content.
5. Firewalls: A firewall is a network security device, either hardware or software-based, which monitors all incoming and outgoing traffic and based on a defined set of security rules accepts, rejects, or drops that specific traffic. Before Firewalls, network security was performed by Access Control Lists (ACLs) residing on routers.
6. Application Security: Application security denotes the security precautionary measures utilized at the application level to prevent the stealing or capturing of data or code inside the application. It also includes the security measurements made during the advancement and design of applications, as well as techniques and methods for protecting the applications whenever.
7. Intrusion Prevention System(IPS): An intrusion Prevention System is also known as Intrusion Detection and Prevention System. It is a network security application that monitors network or system activities for malicious activity. The major functions of intrusion prevention systems are to identify malicious activity, collect information about this activity, report it, and attempt to block or stop it.
Frequently Asked Question on Network Security – FAQs
What is network security?
Network security is defined as the activity created to protect the ntegrity of your network and data.
What is Firewall?
Your trusted internal network and untrusted external networks, like the Internet, are separated by firewalls.
What is an intrusion detection system (IDS)?
An intrusion detection system (IDS) monitors network traffic in order to spot potentially harmful transactions and promptly notifies users when one is detected.
What is a Denial-of-Service (DoS) attack?
A denial-of-service (DoS) attack is a cyberattack type in which the attacker attempts to stop a computer or other device from working normally, thereby making it unavailable to its intended users.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...